The public key is made available to anyone who wants to verify the identity of the certificate holder, while the private key is a unique key that is kept secret. This enables the certificate holder to digitally sign documents, emails and other information without a third party being able to impersonate them.
What is a public key and a private key?
What is a Public and Private Key Pair?
- Public and Private key pair helps to encrypt information that ensures data is protected during transmission. Private Key and public key are a part of encryption that encodes the information. ...
- Public Key. Public key uses asymmetric algorithms that convert messages into an unreadable format. ...
- Private Key. ...
- Key Size and Algorithms. ...
How to install a public certificate?
- Select the Internet Information Service console within the Administrative Tools menu.
- Select the Web site (host) for which the certificate was made.
- Right mouse-click and select Properties.
- Select the Directory Security tab.
- Select the Server Certificate option.
- The Welcome to the Web Server Certificate Wizard windows opens. ...
How to verify the private key in certificate?
openssl verify certificate and key. To verify a certificate is the matching certificate for a private key, we will need to break away from using the openssl verify command and switch to checking the modulus of each key. First, use the openssl rsa command to check that the private key is valid: openssl rsa -check -noout -in key.pem
How to check if SSL certificate is public or private?
What is an SSL checker?
- Open the tool: SSL Checker.
- Enter the URL in the space provided for that purpose and click on the "Check SSL Certificate" button.
- The tool will process your query and provide the results, including common name, server type, issuer, validity, certificate chaining, and additional certificate details.

What is private key of a certificate?
The private key is a separate file that's used in the encryption/decryption of data sent between your server and the connecting clients. A private key is created by you — the certificate owner — when you request your certificate with a Certificate Signing Request (CSR).
What is the public key of a certificate?
A public key certificate can be thought of as the digital equivalent of a passport. It is issued by a trusted organization and provides identification for the bearer. A trusted organization that issues public key certificates is known as a Certificate Authority (CA). The CA can be likened to a notary public.
What is public certificate and private certificate?
Both public and private certificates help customers identify resources on networks and secure communication between these resources. Public certificates identify resources on the public Internet, whereas private certificates do the same for private networks.
How can I get public key and private key from certificate?
How to Extract the Private and Public Key From pfx FileExtract the key-pair. #openssl pkcs12 -in sample.pfx -nocerts -nodes -out sample.key.Get the Private Key from the key-pair. ... Get the Public Key from key pair. ... Need to do some modification to the private key -> to pkcs8 format. ... Get those files.
What are the 3 types of certificates?
There are three main types of certificates: domain validated (DV), organization validated (OV), and extended validation (EV). An authentic authority must obtain the certificate so that users won't see this message. Any certificate will provide the same level of protection, no matter the type of validation.
Is SSL certificate a public key?
SSL uses public-key algorithms to exchange encryption key information and digital certificate information for authentication.
What is a private key?
A private key, also known as a secret key, is a variable in cryptography that is used with an algorithm to encrypt and decrypt data. Secret keys should only be shared with the key's generator or parties authorized to decrypt the data.
How do public and private keys work?
In public key cryptography, every public key matches to only one private key. Together, they are used to encrypt and decrypt messages. If you encode a message using a person's public key, they can only decode it using their matching private key.
Does SSL certificate need private key?
Your private key is the single most important component of your SSL certificate. It's what gives you the power to authenticate your website to internet users, helps to enable encryption and prevents others from impersonating you.
What is difference between public and private key?
Private key is used for both encrypting and decrypting the sensitive data. It is shared between the sender and receiver of encrypted data. Public key is used only for the purpose of encrypting the data. The private key mechanism is faster.
How do I know if my certificate is public or private?
In the Certificate windows that appears, you should see a note with a key symbol underneath the Valid from field that says, "You have a private key that corresponds to this certificate." If you do not see this, then your private key is not attached to this certificate, indicating a certificate installation issue.
How do I create a private key for my certificate?
ProcedureOpen the command line.Create a new private key in the PKCS#1 format. openssl genrsa -des3 -out key_name .key key_strength. For example: openssl genrsa -des3 -out private_key. ... Create a certificate signing request (CSR). The request is associated with your private key and is later transformed into a certificate.
How do I find my public key certificate?
Chrome 54 and below: If you're using Chrome then click on the green bar to the left of the 'https:' in the address bar, for the VeriSign website the green bar says Symantec Corperation [US] , this will open a pop up. On the pop up click 'Certificate Information'. This will open another pop up.
What do you mean by public key?
In cryptography, a public key is a large numerical value that is used to encrypt data. The key can be generated by a software program, but more often, it is provided by a trusted, designated authority and made available to everyone through a publicly accessible repository or directory.
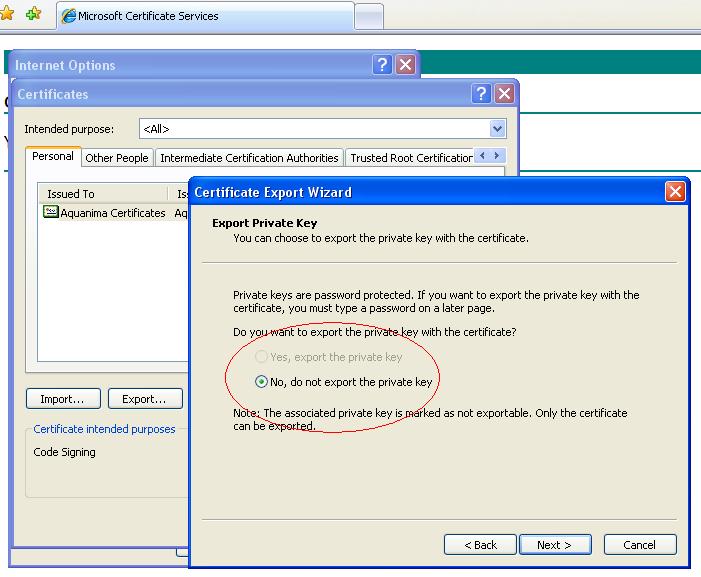
How do I export a public key from a certificate?
16.4 Exporting a Private/Public Key PairClick Security > Certificates.On the Certificates page, click the certificate.On the Certificate Details page, click Export Private/Public Keypair.Select a format for the key: ... Specify the password in the Encryption/decryption password field, then click OK. ... Click OK.
How do I know if my certificate is public or private?
In the Certificate windows that appears, you should see a note with a key symbol underneath the Valid from field that says, "You have a private key that corresponds to this certificate." If you do not see this, then your private key is not attached to this certificate, indicating a certificate installation issue.
What is Private Key?
Private Key is the secret key used to encrypt and decrypt messages between communicators. It’s a form of symmetric encryption, i.e., the same key is utilized for both encryption and decryption purposes.
How does asymmetric encryption work?
An asymmetric encryption functions on the basis of both public and private key. The messenger encrypts the message using the public key, and the receiver can access the message after decrypting it with their private key. Security is ensured because only the person with the relevant private key can decode the message.
What is the strongest industry standard?
The strength and security of both public and private keys are decided by the key size, i.e., the bit-length. Currently, the strongest industry standard is a 2048-bit RSA key.
What is savvy security?
Welcome to Savvy Security, a blog focused on providing practical cybersecurity advice for website owners and small businesses. Our team brings you the latest news, best practices and tips you can use to protect your business...without a multi-million dollar budget or 24/7 security teams.
Does a loss in private key affect the system?
This is essentially a combination of both private and public key, so a loss in private key doesn’t affect the system. Example: A encrypts sensitive information into ciphertext using the private key and shares it with B. In order to access the information, B must decrypt the ciphertext into plain text using their copy of the private key.
How does Diffie Hellman work?
Here’s how it works. With Diffie-Hellman, both parties exchange randomly generated bits of data. There’s a logarithmic function that takes place and both parties are able to use that data, despite passing it insecurely, to derive the same secure session key. No encryption takes place in its passing, as you see in RSA, hence it’s not technically public key encryption.
How much does a wildcard certificate cost?
We offer wildcard certificates from the leading CAs, including Comodo CA, Sectigo, Thawte, GeoTrust, and RapidSSL starting for as little as $52.95 per year.
How does RSA work?
With RSA, there are two functions being performed simultaneously. The client first encrypts a bit of information using the public key and sends it to the server, which decrypts it using the private key. Both parties use that information to derive the session key (a symmetric, private key that will be used to communicate).
What is the same for all private key systems?
The one thing that remains the same with all private key systems is that the same key can both encrypt and decrypt. Private key encryption is sometimes called symmetric encryption.
Why is public key cryptography important?
That’s because public key cryptography is kind of like the gatekeeper, it needs to be sufficiently robust to protect the website and the connections it’s making. Public key cryptography is primarily used for two things: Authentication. Key Exchange. These are both performed during the handshake.
Why is public key used in cryptography?
It can be used to encrypt while the private key can be used to decrypt. The public key is also capable of verifying signatures left by the private key. Public/Private key pairs are generally much larger than their symmetric counterparts. That’s because public key cryptography is kind of like the gatekeeper, it needs to be sufficiently robust ...
What is a session key?
Both parties use that information to derive the session key (a symmetric, private key that will be used to communicate). When the client encrypts that data, the pre-master secret, it will also authenticate the server when it proves it has the corresponding private key to decrypt it with.
What is PKI encryption?
PKI cryptographic algorithms use the public key of the receiver of an encrypted message to encrypt data, and the related private key and only the related private key to decrypt the encrypted message. Similarly, a digital signature of the content, described in greater detail below, is created with the signer's private key.
How does a digital signature work?
A digital signature is used as confirmation that a message has not been altered and as confirmation of the message sender's identity. This digital signature is dependent on your private key and the message contents. Using the message as input and your private key, cryptographic algorithms create the digital signature. The contents of the message are not changed by the signing process. A recipient can use your public key (after checking your certificate's validity, issuing CA, and revocation status) to determine whether the signature corresponds to the message contents and to determine whether the message was sent by you.
How to determine if a certificate is still valid?
Assuming the certificate consumer trusts the issuing CA for your certificate, the certificate consumer must determine whether the certificate is still valid by comparing the certificate's beginning and ending dates with the current time and by checking that your certificate in not on the CA's list of revoked certificates.
What is a PKI?
The Public/Private Key Pair. PKI requires the use of public/private key pairs. The mathematics of public/private key pairs is beyond the scope of this documentation, but it is important to note the functional relationship between a public and a private key. PKI cryptographic algorithms use the public key of the receiver ...
What is the CA before a certificate is issued?
Before issuing your certificate, the CA verifies your identity. When the certificate is issued, your identity is bound to the certificate, which contains your public key. Your certificate also contains the CA's digital signature (which can be verified by anyone who receives your certificate).
What is certificate services?
Certificate Services is one foundation for the Public Key Infrastructure (PKI) that provides the means for safeguarding and authenticating information . The relationship between a certificate holder, the certificate holder's identity, and the certificate holder's public key is a critical portion of PKI. This infrastructure is made up of the following parts:
What is chain of signed certificates?
A chain of signed certificates allows trust to be transferred to other CAs as well. This allows parties who use different CAs to still be able to trust certificates (provided there is a common CA in the chain, that is, a CA that is trusted by both parties).
What is a public key certificate?
A public key certificate is a digitally signed document that serves to validate the sender's authorization and name. It uses a cryptographic structure that binds a public key to an entity, such as a user or organization. The digital document is generated and issued by a trusted third party called a certification authority.
How does a public key certificate work?
Public key certificates form a part of a public key infrastructure ( PKI) system that uses encryption technology to secure messages and data. A public key certificate uses a pair of encryption keys, one public and one private.
What are the different types of certificates?
Transport Layer Security/Secure Sockets Layer (TLS/SSL) certificates. These certificates are the core of transport layer security ( TLS) protocol, which is an updated version of SSL.
Advantages and disadvantages of public key certificates
The main advantage of using public key certificates is that they enable secure authentication. The integrity of the public key certificate is guaranteed by the CA.
Why would an application not handle a .crt file if it wants a client certificate?
A certificate is just a public key, and thus by definition public. A client certificate is no different - just a public key by a person, machine or other "client", that is signed by some authority.
What is a PFX file?
PFX or P12 use binary file encoding. With PFX, you can store multiple certificates with associated private keys and optional certificate chains. Hence it is a container. why, for example, an application expecting a "client certificate" blows up when you give it a .crt file.
What are the different types of file types?
What are all those different file types? 1 .pem: A .pem is a de-facto file format called Privacy-Enhanced Mail. A PEM file can contain a lot of different things, such as certificates, private keys, public keys and lots of other things. A file being in PEM format says nothing about the content, just like something being Base64-encoded says nothing about the content. 2 .crt, .cer: This is another pseudo-format that is commonly used to store certificates. These can either be in the PEM or in the DER format. 3 .p12, .pfx: These are interchangable file extensions for the PKCS#12 format. Technically, PKCS#12 is the successor to Microsoft's PFX format, but they have become interchangable. PKCS#12 files are archives for cryptographic material. Again, what kind of material this contains is completely up to the user.
What does a client certificate do?
An application that wants a client certificate usually wants to use that certificate for something, such as to authenticate the client to a server. In order to do that, one needs the certificate and the corresponding private key.
Why is a certificate called a public certificate?
Certificate is often called as public certificate, because it contains only public key and public information. Possessing the public certificate only doesn't prove certificate ownership. Only possession of private key that is associated with public key embedded in public certificate can prove certificate ownership.
What is PKCS#12?
Technically, PKCS#12 is the successor to Microsoft's PFX format, but they have become interchangable. PKCS#12 files are archives for cryptographic material. Again, what kind of material this contains is completely up to the user.
What is private key?
Private key is raw key material without any extra information. For example, from private key you can't extract information about owner of the key, or a certificate this private key is associated with. Certificate is often called as public certificate, because it contains only public key and public information.
Why are trusted certificates called trusted certificates?
Part of the reason they’re called trusted certificate authorities is because we inherently trust that they keep this root safe.
Why is certificate issuance important?
Certificate issuance is a critical part of securing interactions on the internet because certificates cryptographically tie an identity to a public key. Certificates are commonly used in SSL encryption, to authenticate people and devices, and to legitimize documents and code. A feature of a good certificate authority is ‘ubiquity’.
How does the root validate certificates?
So how does it validate certificates in that state? The root is used to create intermediate certificates, which have the same measure of trust afforded to the root because they are validated by it. At the same time, they are accessible by the public and so can validate certificates in the root’s stead. If an intermediate certificate is compromised, the root is always available as a backup.
Why are CAs stored in a secure facility?
The measures CAs go to in order to protect the root are extreme. They’re usually stored in a secure facility, powered off, and air-gapped so that there is no possible network connection and no potential for theft.
Why is control over certificate expiration important?
Control over certificate expiration is an important feature to organizations that have a cyclical or time-sensitive nature. It would be a disaster if certificates expired in the middle of the week at a university, disconnecting every person and every device.
What is a CA?
What’s a Public Certificate Authority? A Public CA is, unsurprisingly, a certificate authority that provides services to the general public. Any organization providing CA services to you that you’re not affiliated with is a public CA. Most public CAs are companies that have garnered the trust of the public at large.
What is a good certificate authority?
A feature of a good certificate authority is ‘ubiquity’. They need to be compatible with as many versions of operating systems and internet browsers as possible so that they can provide uninterrupted validation of certificates to all users across any device or service.
How do I get it?
The Private Key is generated with your Certificate Signing Request (CSR). The CSR is submitted to the Certificate Authority right after you activate your Certificate. The Private Key must be kept safe and secret on your server or device because later you’ll need it for Certificate installation.
What does the Private Key look like?
It looks like a block of encoded data, starting and ending with headers, such as —–BEGIN RSA PRIVATE KEY—– and —–END RSA PRIVATE KEY—–.
How to get a PEM file?
To get it in plain text format, click the name and scroll down the page until you see the key code. Alternatively, click the green arrow icon on the right. This will download a PEM file, containing your Private Key, Certificate, and CA-Bundle files (if they were previously imported to the server).
How to find the SSL certificate on my domain?
Click Domains > your domain > SSL/TLS Certificates. You’ll see a page like the one shown below. The key icon with the message “Private key part supplied” means there is a matching key on your server.
How to find private key?
If you can’t find the Private Key in the previously mentioned folders, use your computer’s search function and enter the file name (i.e., example_com_key.zip). If you still can’t find the Private Key, you will need to get your SSL reissued. Because the in-browser CSR generation method creates the Private Key directly on your device, there’s no way of restoring it if it’s lost. This is why it’s essential to save your Private Key and back it up if you choose this method.
What is PKI in security?
Public Key Infrastructure (PKI) security is about using two unique keys: the Public Key is encrypted within your SSL Certificate, while the Private Key is generated on your server and kept secret. All the information sent from a browser to a website server is encrypted with the Public Key and gets decrypted on the server-side with the Private Key.
Where is the private key stored in WHM?
WHM stores your Private Keys and CSR codes in the SSL Storage Manager menu. On the homepage, click SSL/TLS >> SSL Storage Manager. To view the Private Key, click the magnifier icon next to the relevant key in the Key column.