What are public and private keys?
What is a Public Key?
- Public Keys can be shared with other people on the network
- We can generate addresses from the Public Key
- Public Keys are used by other users on the network to challenge ownership of Bitcoins
- This is a generated Public Key from our Private Key above
What is public key cryptography example?
What is public key cryptography example? Example: Public keys of every user are present in the Public key Register. If B wants to send a confidential message to C, then B encrypt the message using C Public key. …. No other recipient other than C can decrypt the message because only C know C’s private key.
What are cryptography, symmetric and public key algorithms?
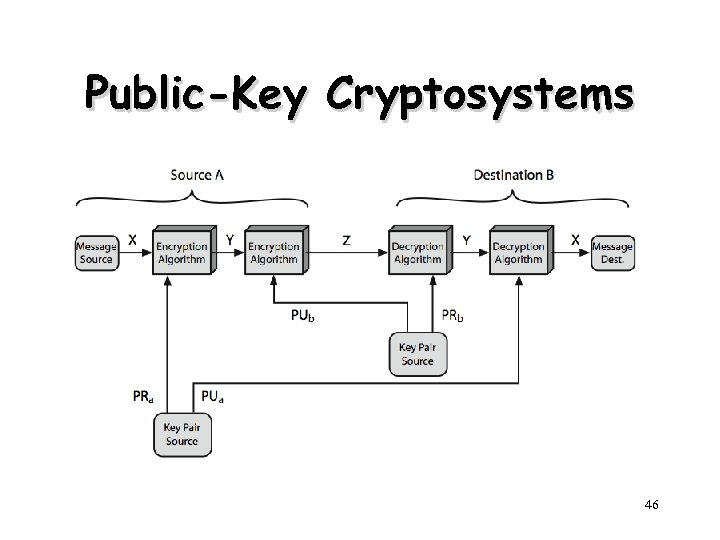
Symmetric key cryptography is also known as shared key cryptography. As the name suggests, it involves 2 people using the same private key to both encrypt and decrypt information. Public key cryptography, on the other hand, is where 2 different keys are used – a public key for encryption and a private key for decryption.
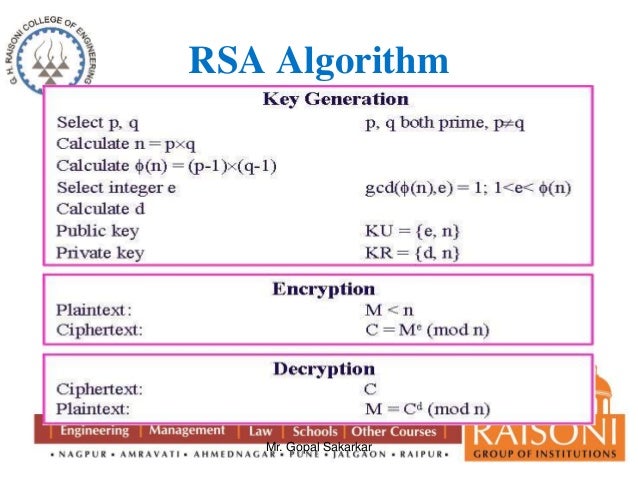
What is a RSA algorithm?
The Rivest-Shamir-Adleman (RSA) encryption algorithm is an asymmetric encryption algorithm that is widely used in many products and services. Asymmetric encryption uses a key pair that is mathematically linked to encrypt and decrypt data.
What is public key and private key with example?
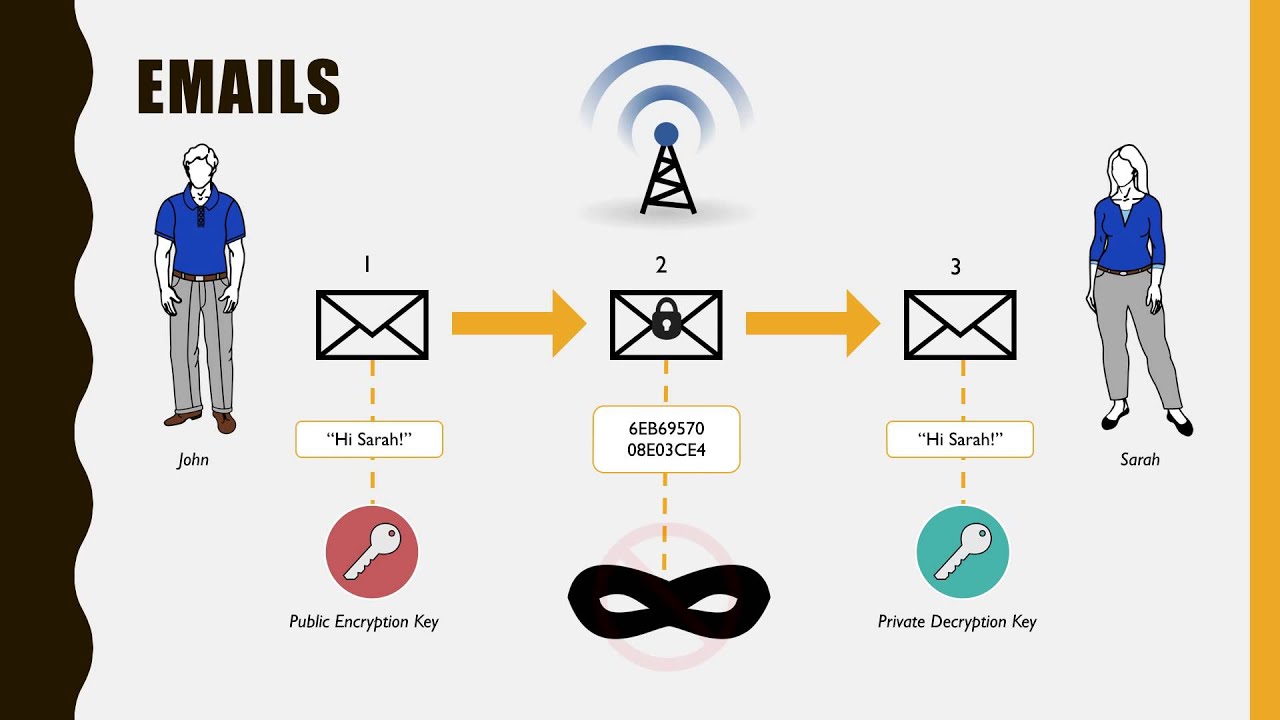
Public and private keys: an example Bob wants to send Alice an encrypted email. To do this, Bob takes Alice's public key and encrypts his message to her. Then, when Alice receives the message, she takes the private key that is known only to her in order to decrypt the message from Bob.
What is private key in cryptography?
A private key, also known as a secret key, is a variable in cryptography that is used with an algorithm to encrypt and decrypt data. Secret keys should only be shared with the key's generator or parties authorized to decrypt the data.
What's the difference between a private and public key?
The public key is used to encrypt data. The private key is used to decrypt data. The public—private key pair have a mathematical relationship, which means that the data encrypted with a public key can only be decrypted with the corresponding private key.
Which is public key cryptography?
Public key cryptography involves a pair of keys known as a public key and a private key (a public key pair), which are associated with an entity that needs to authenticate its identity electronically or to sign or encrypt data. Each public key is published and the corresponding private key is kept secret.
What are the 3 types of encryption keys?
Symmetric, or secret key encryption, uses a single key for both encryption and decryption. Symmetric key encryption is used for encrypting large amounts of data efficiently. 256-bit AES keys are symmetric keys. Asymmetric, or public/private encryption, uses a pair of keys.
What is meant by public key?
In cryptography, a public key is a large numerical value that is used to encrypt data. The key can be generated by a software program, but more often, it is provided by a trusted, designated authority and made available to everyone through a publicly accessible repository or directory.
What are the types of public key?
ExamplesDiffie–Hellman key exchange protocol.DSS (Digital Signature Standard), which incorporates the Digital Signature Algorithm.ElGamal.Elliptic-curve cryptography. ... Various password-authenticated key agreement techniques.Paillier cryptosystem.RSA encryption algorithm (PKCS#1)Cramer–Shoup cryptosystem.More items...
How do you define a private key?
Definition(s): The secret part of an asymmetric key pair that is typically used to digitally sign or decrypt data.
Is PPK public or private key?
PPK files are PuTTY Private Key Files developed by Putty and they serve as storage for the private keys the program generated. These files are used to enable communication securely with another party having the corresponding public key.
What are the two main types of cryptography?
In general there are three types Of cryptography:Symmetric Key Cryptography: It is an encryption system where the sender and receiver of message use a single common key to encrypt and decrypt messages. ... Hash Functions: There is no usage of any key in this algorithm. ... Asymmetric Key Cryptography:
Is public key symmetric or asymmetric?
Asymmetric encryption is also known as public key cryptography, which is a relatively new method, compared to symmetric encryption. Asymmetric encryption uses two keys to encrypt a plain text. Secret keys are exchanged over the Internet or a large network.
Is a public key a hash?
The public key hash is a hashed version of your public key . It's the version of your public key that you give to other people so that they can send you bitcoins. It's shorter than the original public key, and it may provide an extra layer of security for your bitcoins compared to giving out your public key directly.
Where is the private key?
If you have not yet installed your certificate, then the most likely location of your private key is on the computer or server where you generated the key pair and CSR. When you generated the key pair, you saved two files: one that contains the public key and one that contains the private key.
Why is a private key important?
Your private key is the single most important component of your SSL certificate. It's what gives you the power to authenticate your website to internet users, helps to enable encryption and prevents others from impersonating you.
Is private key same as wallet address?
A Wallet Address can only be used to make transactions into such wallet, so it's safe to share with other people for them to make a transfer to your wallet. On the other hand, your Private Key is the set of numbers and letters that allows you to access your wallet.
What is a private key in crypto?
While a public key can be widely distributed, a private key used in the crypto context is meant to be kept discretely as a password to safeguard your digital assets. Usually, these private keys vary depending on the different types of cryptocurrency, although almost all of them use 256-bit encryption.
How Does Private and Public Keys Work?
Public key cryptography has two primary use cases— identification and confidentiality. In simple words, it can be described in the following way:
What is a crypto wallet?
Cryptocurrency wallets are excellent examples of public and private keys utilization . When considering wallets, a public key is a user’s address, and it gives other network participants a point of access to send tokens to this wallet. But if a user wants to send crypto from one to another, they’ll need their private keys to confirm the transaction.
How many keys are needed for encryption?
Algorithm and Mechanism. In public-key encryption, there must be two separate keys for encryption and decryption. The private key is for the owner only, while the public key is available to anyone. One key is required for transmission between the two parties involved in symmetric key cryptography. The same private key is used both to encrypt ...
What is the purpose of both private and public keys?
Both private and public keys’ goal is to verify that a given transaction was spent by the party who signed it and not forged out of thin air. Though both types of encryption cater a similar purpose, they differ in many ways. Here’s what you need to understand:
What is asymmetric encryption?
Asymmetric Encryption. Unlike symmetric, the encryption and decryption of messages usually involve two keys— Private and Public Key. Public keys are used to verify a transaction after a transaction has been requested. Whereas a private key is to decipher the message or transaction.
What does it mean when a private key is misplaced?
That also means, if the private keys are misplaced, there are no ways to find them. Similarly, if the private key is exposed, any transactions can be granted, and it’s unretrievable because it’s authorized.
What is the key used in public key cryptography?
In public key cryptography, two keys are used, one key is used for encryption and while the other is used for decryption. 3. In private key cryptography, the key is kept as a secret.
Why is private key cryptography symmetric?
In this key is symmetric because the only key is copy or share by another party to decrypt the cipher text. It is faster than the public key cryptography.
What is a public key?
Public Key: In Public key, two keys are used one key is used for encryption and another key is used for decryption. One key (public key) is used for encrypt the plain text to convert it into cipher text and another key (private key) is used by receiver to decrypt the cipher text to read the message. Now, we see the difference between them: S.NO.
Do sender and receiver share the same key?
In this cryptography, sender and receiver need to share the same key. In this cryptography, sender and receiver does not need to share the same key. 6. In this cryptography, the key is private. In this cryptography, public key can be public and private key is private. Attention reader!
Is a private key symmetrical or asymmetrical?
In private key cryptography, the key is kept as a secret. In public key cryptography, one of the two keys is kept as a secret. 4. Private key is Symmetrical because there is only one key that is called secret key. Public key is Asymmetrical because there are two types of key: private and public key. 5.
What is public key cryptography?
In public key cryptography, the message sender encrypts the message with the public key and sends it to a recipient. The message recipient receives it and decrypts it with the private key that only he or she has. Since only the recipient needs a private key in this encryption system, it doesn't have to be sent, thus increasing its security. In public key cryptography, only the recipient — not even the sender — can decrypt the message.
How does private key work in cryptography?
In private key cryptography, the sender encrypts the message using the private key and sends it to the recipient. For the recipient to decrypt the message, they'll need the sender to provide the same private key through a well-secured channel, thus reducing the security of such cryptographic systems.
What is public key encryption?
This encryption system is much more complex, using the private key only to decrypt the message. To encrypt the same message, a separate public key derived from the public key is used. If a person knows the private key, they can calculate the public key. However, knowing only the public key isn't enough to calculate the private key. That's why the public key doesn't need to be kept secret since knowing it doesn't allow encrypted information to be decrypted.
What are the two types of encryption?
Decryption is the conversion of an encrypted message back to its original form. An algorithm and key are used for both encryption and decryption, and there are two methods of encryption and decryption: symmetric and asymmetric encryption. Symmetric encryption, also called private key encryption, has been known to humanity for a very long time. On the other hand, asymmetric encryption, also called public key encryption, appeared only in the 1970s and became really widespread as the Internet developed.
Why is the public key not kept secret?
If a person knows the private key, they can calculate the public key. However, knowing only the public key isn't enough to calculate the private key. That's why the public key doesn't need to be kept secret since knowing it doesn't allow encrypted information to be decrypted.
What is the key element of blockchain?
The key element of any blockchain project is the cryptography used to protect data. Without it, no transactions are protected. The cryptocurrencies we all know are built on so-called public key cryptography. In this article, we'll look at the difference between public key cryptography and private key cryptography, discuss each system's advantages and disadvantages, and answer other questions on this topic.
What is a private key?
Private keys are simply extremely large and random numbers. Public Keys are ( x, y) points on an Elliptic Curve, generated by using the Private Key as a scalar. Private and Public Key cryptography derives its security from the Discrete Log Problem, given the starting value and the end value, it’s difficult to deduce the scalar (Private Key) ...
What is the public key on an elliptic curve?
The Public Key is an ( x ,y) co-ordinate on an Elliptic Curve. The Public Key would be any point on this curve. Elliptic Curve. The Private Key is used as a scalar (A ll this means is that Private Key Number is used as a multiplier)
Can you deduce a scalar from a public key?
By knowing the starting position ( G) and the final position ( Public Key) we cannot deduce the scalar ( Private Key ), given we are dealing with extremely large numbers
What is the difference between a private key and a public key?
The following are some of the important differences between Private Key and Public Key. Private Key is used to both encrypt and decrypt the data and is shared between the sender and receiver of encrypted data. The public key is only used to encrypt data and to decrypt the data , the private key is used and is shared.
What is a private key?
The private key is used to both encrypt and decrypt the data. This key is shared between the sender and receiver of the encrypted sensitive information. The private key is also called symmetric being common for both parties. Private key cryptography is faster than public-key cryptography mechanism.
What is the public key used for?
Public Key. The public key is used to encrypt and a private key is used decrypt the data. The private key is shared between the sender and receiver of the encrypted sensitive information. The public key is also called asymmetric cryptography.
What is the public key mechanism?
The public key mechanism is called asymmetric being two keys for different purposes. 5. Sharing. The private key is to be shared between two parties. The public key can be used by anyone but the private key is to be shared between two parties only. 6.
Is a private key public or private?
The private key is kept secret and not public to anyone apart from the sender and receiver. The public key is free to use and the private key is kept secret only. The private key mechanism is called symmetric being a single key between two parties.
Why is public key encryption used?
The public key is then used to encrypt data that can be decoded/ decrypted only with the help of the corresponding private key. This means that knowing / having the public key alone won’t get you the private key; it’s why this method is called asymmetric encryption and is known to be the safer option.
What is the key in cryptography?
A lot of cryptography techniques rely on information known to both parties, the sender and the recipient. This information is called as the key. Suppose a girl, say Alice and a boy, say Bob, have an understanding between them that dog shall be denoted by the word horse, that is dog = horse.
How is encryption made possible?
In modern times, encryption has been made possible by using algorithms that have a key to encrypt and decrypt information. These keys convert the messages and data into “digital gibberish” through encryption and then return them to the original form through decryption.
What is the process of converting information into unintelligible text?
Cryptography then consists of two parts: encryption and decryption . For the longest time, cryptography mainly referred to encryption, which is the process of converting ordinary information (the information that needs to be passed on securely) into unintelligible text, also called ciphertext. But in modern times, cryptography is also about the second half of decryption , which is basically the reverse, in that it entails converting the unintelligible ciphertext back to into ordinary text or plaintext.
Why is cryptography used?
It’s not surprising that cryptography has been and continues to be used to protect sensitive information such as military information and conversely, to further espionage. The early 20th century saw not one but two World Wars; maintaining secrecy of information was crucial at such times.
How do Alice and Bob begin the process of asymmetric encryption?
If they are using asymmetric key encryption, this is how the process shall unfold: Both Alice and Bob begin by generating a set of public and private keys. They then swap public keys with each other (Alice sends her public key to Bob and vice versa).
What is cryptography in science?
What is Cryptography? Cryptography, also known as cryptology, is, simply put , the art of writing and solving codes. It involves the practice and study of techniques used for secure communication in the presence of third parties.
What is public key cryptography?
Public key cryptography uses a pair of keys to encrypt and decrypt data to protect it against unauthorized access or use. Network users receive a public and private key pair from certification authorities. If other users want to encrypt data, they get the intended recipient’s public key from a public directory.
What is the difference between public key and private key?
Public key cryptography requires each user to be responsible for protecting his private key, whereas private key systems require users to share secret keys and perhaps even trust third parties for transmission. With the secret key system, it is possible for senders to claim the shared secret key was compromised by one of the parties involved in ...
Why is public key cryptography important?
Public key cryptography remains the most secure protocol (over private key cryptography) because users never need to transmit or reveal their private keys to anyone, which lessens the chances of cyber criminals discovering an ...
Why is public key encryption used?
Typically, public key encryption is the cryptography method of choice when there is a multi-user environment and it is necessary to ensure confidentiality through key distribution and digital signatures for verifying user identities.
What is the RSA key used for?
This key is used to encrypt the message, and to send it to the recipient. When the message arrives, the recipient decrypts it using a private key, to which no one else has access. The Rivest-Sharmir-Adleman (RSA) algorithm is the cryptography system that is used for public key cryptography, which is commonly used when sending secure, ...
Is private key encryption faster than public key encryption?
Several private key cryptography methods are a great deal faster than the public key encryption method that currently is available. One way of overcoming this challenge with public key cryptography is to combine it with secret key systems to offer the security advantages of the public key system and the speed of the secret (private) key system.
What Is A Public and Private Key?
Cryptography Methods Used in Cryptocurrencies
- When it comes to cryptography in cryptocurrency, there are several methods, and that includes symmetric encryption, asymmetric encryption, and hashing.
How Do Private and Public Keys Work?
- Public key cryptography has two primary use cases— identification and confidentiality. In simple words, it can be described in the following way: 1. A sender gets an addressee’s public key. 2. The sender uses this key to encrypt information. 3. The sender sends the encrypted information to an addressee. 4. The addressee uses his or her private key to decrypt the data. Let’s say, Alex (send…
The Differences Between Public Keys and Private Keys
- Both private and public keys’ goal is to verify that a given transaction was spent by the party who signed it and not forged out of thin air. Though both types of encryption cater a similar purpose, they differ in many ways. Here’s what you need to understand:
Benefits and Limitations of Public and Private Key Encryption
- There is no perfection for any methodologies or encryption, and that includes the public and private keys. Here are the pros and cons:
When to Choose A Public Or Private Key?
- The choice of the encryption method varies depending on your preference and convenience. Symmetric encryption is beneficial if you value speed and data protection over the rest. For example, the Advanced Encryption Standard (AES) adopted symmetric encryption algorithm is used by many big companies and entities like Apple and Microsoft. Besides, if you focus on dat…
Closing Thoughts
- As we move towards the digitized sphere, data storage and security have increasingly become important. Public key encryption helps users maintain reasonable security practices as nobody knows the private key paired with the open public key. It is advantageous when to avoid potential interceptions and cyber frauds. However, all you need is to ensure your private key secure and in…