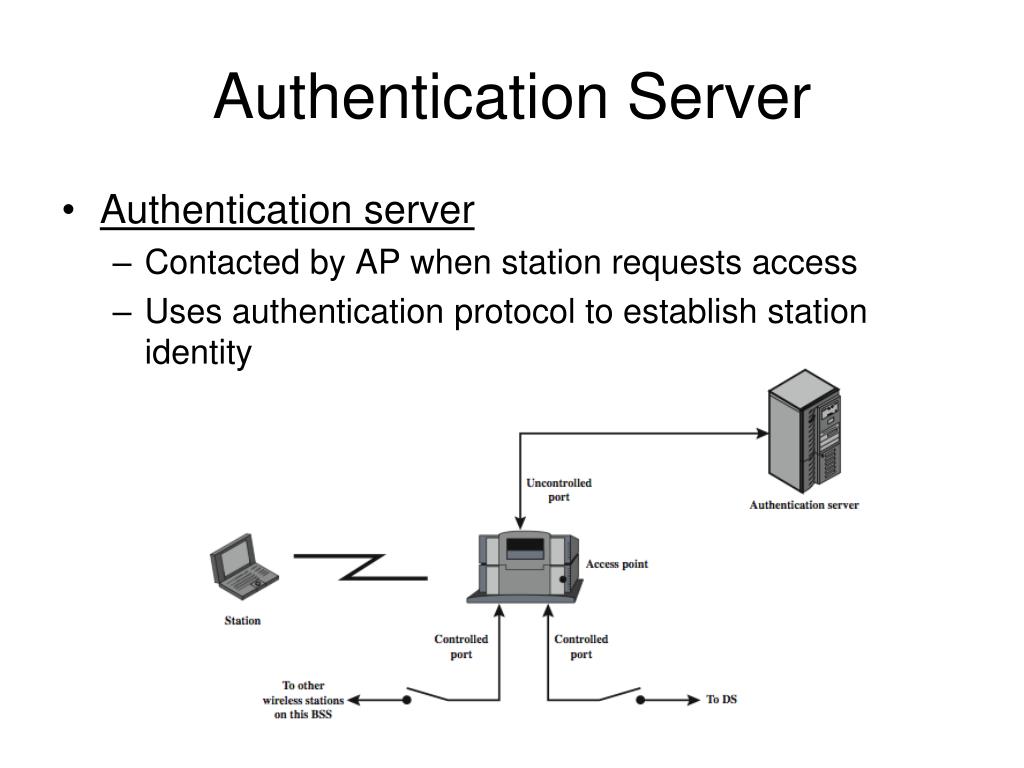
An authentication server is a type of network server that validates and authenticates remote users or IT nodes connecting to an application or service. It ensures that only authorized and authenticated nodes are provided access to the server, application, storage or any other IT resources behind the authentication server. Advertisement
Full Answer
How is the Server authenticated in SSH?
Using SSH Key for authentication
- Generating SSH Key Pair. Generate the SSH key pair on the local server using OpenSSH. ...
- Configuring one or multiple SSH/SFTP Users for Your Key. After generating a key pair, the next step is to configure the server machine for SSH and SFTP users for the ...
- Logging in. Note: If you do not specify a username, SSH uses the currently logged in user. ...
What is an example of authentication?
There are three types of authentication factors typically classified as follows:
- Something you know, for example, a password
- Something you have, for example, a smartphone
- Something you are, for example, biometric authentication
Are MC Auth servers down?
There could be a chance where authentication servers really are down and to check that visit http://pingserverstatus.com/minecraftauth.php check if it's down on your location or ask your friends if they are also experiencing this issue. The thread will soon be updated with more possible solutions.
What is an authenticated external user?
“An external user is authenticated when they have an identity account that can be Microsoft 365, or a different provider like Gmail. These people can work on your documents as well as be part of your M365 groups.
What is meant by server authentication?
An authentication server is an application that facilitates the authentication of an entity that attempts to access a network. Such an entity may be a human user or another server. An authentication server can reside in a dedicated computer, an Ethernet switch, an access point or a network access server.
How do servers authenticate?
In authentication, the user or computer has to prove its identity to the server or client. Usually, authentication by a server entails the use of a user name and password. Other ways to authenticate can be through cards, retina scans, voice recognition, and fingerprints.
What is server authentication and client authentication?
Client certificates tend to be used within private organizations to authenticate requests to remote servers. Whereas server certificates are more commonly known as TLS/SSL certificates and are used to protect servers and web domains.
What is server authentication in SSL?
When using SSL to secure communications, the SSL authentication mechanism known as Server Authentication is used. This is the minimum amount of security provided by SSL and allows the client to validate that the Server is what it says it is.
What are the 3 types of authentication?
Authentication factors can be classified into three groups: something you know: a password or personal identification number (PIN); something you have: a token, such as bank card; something you are: biometrics, such as fingerprints and voice recognition.
What is authentication example?
Authentication with Username and Password Username and password combination is the most popular authentication mechanism, and it is also known as password authentication. A well-known example is accessing a user account on a website or a service provider such as Facebook or Gmail.
Is SSL same as TLS?
Transport Layer Security (TLS) is the successor protocol to SSL. TLS is an improved version of SSL. It works in much the same way as the SSL, using encryption to protect the transfer of data and information. The two terms are often used interchangeably in the industry although SSL is still widely used.
What is server authentication error?
Error: SMTP server authentication error Some of the most common issues include the following: Invalid username and password. Unsupported encryption. Unsupported authentication method. User account is disabled.
How does a server authenticate client certificate?
SSL-enabled client software always requires server authentication, or cryptographic validation by a client of the server's identity. The server sends the client a certificate to authenticate itself. The client uses the certificate to authenticate the identity the certificate claims to represent.
Why is authenticated SSL Necessary?
Websites need SSL certificates to keep user data secure, verify ownership of the website, prevent attackers from creating a fake version of the site, and convey trust to users.
How do I install server authentication certificate?
To import a server authentication certificate to the Default Web SiteOn the Start screen, typeInternet Information Services (IIS) Manager, and then press ENTER.In the console tree, click ComputerName.In the center pane, double-click Server Certificates.In the Actions pane, click Import.More items...•
Why do we need server certificate?
Server certificates are used to authenticate server identity to the client(s). Client certificates are used to authenticate the client (user) identity to the server. Server certificates encrypt data-in-transit. No encryption of data takes place in case of Client certificates.
How does server authenticate itself during the handshake protocol?
The server sends the client a certificate to authenticate itself. The client uses the certificate to authenticate the identity the certificate claims to represent.
What is the most common form of identification and authentication?
PasswordsPasswords are the most common methods of authentication. Passwords can be in the form of a string of letters, numbers, or special characters.
What is LDAP authentication?
LDAP user authentication is the process of validating a username and password combination with a directory server such MS Active Directory, OpenLDAP or OpenDJ. LDAP directories are standard technology for storaging user, group and permission information and serving that to applications in the enterprise.
How do you secure a REST API and how do you authenticate it?
There are various authentication methods for REST APIs, ranging from basic credentials and token encryption to complex, multilayered access control and permissions validation.Basic authentication. ... API keys. ... HMAC encryption. ... OAuth 2.0. ... OpenID Connect. ... Choosing a REST API authentication approach.
What Does Authentication Server Mean?
An authentication server is a type of network server that validates and authenticates remote users or IT nodes connecting to an application or service. It ensures that only authorized and authenticated nodes are provided access to the server, application, storage or any other IT resources behind the authentication server.
What is the purpose of an authentication server?
Typically, validating the identity and granting access of connecting nodes is the prime objective of an authentication server. These nodes can be general end-user, computer, server or an application. An authentication server requires each node to provide valid authentication credentials before they are authorized access.
Why is server authentication important?
The server authentication is important because browsers encrypt the data using the public key that’s tied to an SSL server certificate. When the data reaches the server, it can be decrypted by a unique, cryptographically paired private key, which is safely stored on the server.
Why Is a Server Authentication Certificate Needed?
To better understand the importance and necessity of a server authentication certificate, let’s consider the following hypothetical scenario:
How Do the SSL Server Certificate Authentication Procedures Work?
When someone buys an SSL server authentication certificate, the CA doesn’t automatically issue the certificate for the requested website. There are a few additional steps that must be completed both on the requester’s end and the CA’s end.
What is the public key of an SSL certificate?
The public key sent by the applicant is attached to the SSL certificate. When a user tries to open a website on the browser, the server sends its SSL certificate (which contains a public key) to the client. The SSL server certificate is signed with the CA’s private key from its root (or intermediate root) certificate.
What is SSL certificate?
What Is an SSL Server Authentication Certificate? An SSL server certificate is an X.509 digital certificate based on the public key infrastructure (PKI). Here, the identity of the server (instead of the client) is validated.
Can SSL certificates be trusted?
The certificates that make this possible are called self-signed certificates. However, using a self-signed SSL certificate is like signing your own driving license — its trustworthiness is questionable, and it won’t be trusted by the browsers.
Is SSL the same as TLS?
It also facilitates encryption for the data in transit. Note: An SSL server certificate is also the same thing as a TLS certificate, HTTPS certificate, and web encryption certificate! These are just different names for the same certificate.
