What is SMB session enumeration?
SMB sessions reflect people connected to file shares or making RPC calls and they can provide invaluable information that can be used to profile users and machines. The SMB session information includes usernames, origin IP addresses, and even idle time.
What tool can you use to enumerate SMB shares?
SMBMap allows users to enumerate samba share drives across an entire domain. List share drives, drive permissions, share contents, upload/download functionality, file name auto-download pattern matching, and even execute remote commands.
What is SMB protocol?
The Server Message Block (SMB) protocol is a network file sharing protocol that allows applications on a computer to read and write to files and to request services from server programs in a computer network. The SMB protocol can be used on top of its TCP/IP protocol or other network protocols.
What is SMB exploit?
This vulnerability allows an attacker to execute code on the target system, making it a serious risk to affected systems that have not been patched. Between older systems that are either unpatched or unable to receive further security patches and newer vulnerabilities being found, SMB is a viable target for attackers.
What is SMB example?
An SMB share, also known as an SMB file share, is simply a shared resource on an SMB server. Often, an SMB share is a directory, but it can be any shared resource. For example, network printers are often shared using SMB.
What is DNS enumeration and why is it important?
DNS enumeration is the process of locating all the DNS servers and their corresponding records for an organization. DNS enumeration will yield usernames, computer names, and IP addresses of potential target systems.
Is SMB protocol still used?
The SMB protocol is one of the most popular protocols for file and resource sharing over networks. And not only with Windows—it has also been widely adopted by other operating systems, such as Linux/Unix and macOS.
Is SMB a security risk?
Unprotected SMB ports on Windows servers are an easy target for hackers to exploit to gain further entry to your internal network. Therefore, it is important for your company to implement the following procedures to help keep your SMB ports safe.
Is SMB used over the Internet?
Port 445 is used by newer versions of SMB (after Windows 2000) on top of a TCP stack, allowing SMB to communicate over the Internet. This also means you can use IP addresses in order to use SMB like file sharing.
Should I block SMB?
You must not globally block inbound SMB traffic to domain controllers or file servers. However, you can restrict access to them from trusted IP ranges and devices to lower their attack surface. They should also be restricted to Domain or Private firewall profiles and not allow Guest/Public traffic.
Should I disable SMB?
While disabling or removing SMBv1 might cause some compatibility issues with old computers or software, SMBv1 has significant security vulnerabilities and we strongly encourage you not to use it.
How can SMB be exploited?
This vulnerability is exploited in two ways: first for an information leak, and second for remote code execution. The bug is first exploited to leak pool information via an out-of-bounds read. To do this, a single packet containing multiple SMBs is sent to the server.
Where can I find SMB shares on a known file server?
How to Find Available SMB Shares on a Known File ServerDetermine the server that you want to query about available shares. ... Ensure that the network/smb/client service is enabled. ... List the available SMB shares on a server. ... If prompted, provide the password for the user that you specified on the SMB server.More items...
What is SMB in Wireshark?
Server Message Block Protocol (SMB) The Server Message Block protocol, or "SMB", is a remote file access protocol originally specified by Microsoft, IBM, and Intel. It's also referred to as the Common Internet File System, or "CIFS".
What is Enum4linux tool?
Enum4linux is an enumeration tool capable of detecting and extracting data from Windows and Linux operating systems, including those that are Samba (SMB) hosts on a network. Enum4linux is capable of discovering the following: Password policies on a target. The operating system of a remote target.
What command is used to monitor connections to the SMB server?
The Get-SmbConnection cmdlet retrieves the connections established from the Server Message Block (SMB) client to the SMB servers.
Why do we enumerate SMB?
We enumerate a SMB server in order to compromise we need to enumerate and find possible vulnerabilities that can be used to exploit the server. In order to do this in an optimized method, we can perform a Vulnerability Scanning. There might be multiple tools to perform this kind of Scanning but here we will be focusing on this NSE script.
What is SMB?
SMB or Server Message Block is the modernized concept of what was used to known as Common Internet File System. It works as an Application Layer Network Protocol. It is designed to be used as a File Sharing Protocol. Different Applications can on a system can read and write simultaneously to the files and request the server for services inside a network. One of the interesting functionalities of SMB is that it can be run atop of its TCP/IP protocol or other network protocols. With the help of SMB, a user or any application or software that is authorized can access files or other resources on a remote server. Actions that can be performed include reading data, creating data, and updating data. The communication between clients and servers is done with the help of something called SMB client request.
What version of SMB is used in Windows Server 2008?
SMB 2.0 / SMB2: This version used in Windows Vista and Windows Server 2008.
How does SMB work?
Client computers using SMB connect to a supporting server using NetBIOS over TCP/IP, IPX/SPX, or NetBEUI. The initial establishment of the connection is required for exchanging information. Subsequent data transport is regulated by the provisions of the TCP protocol. SMB functions as a request-response or client-server protocol . Once the connection is established, the client computer or program can then open, read/write, and access files similar to the file system on a local computer.
What is NSE port 445?
This NSE script attempts to determine the operating system, computer name, domain, workgroup, and current time over the SMB protocol (ports 445 or 139). It is achieved by initiating a session with the anonymous account (or with a proper user account, if one is given; it likely doesn’t make a difference); in response to a session starting, the server will send back all this information.
What is nmap script?
This nmap script attempts to retrieve the target’s NetBIOS names and MAC address. By default, the script displays the name of the computer and the logged-in user; if the verbosity is turned up, it displays all names the system thinks it owns. It also shows the flags that we studied in nmblookup tool.
What is SMB_enumshares?
The smb_enumshares module enumerates any SMB shares that are available on a remote system. It requires the IP Address of the target server or machine followed by the set of credentials that can be used to access the share.
What tool can be used to identify whether an SMB server is running on the target host?
Port scanning tools such as Nmap can be used to identify whether an SMB server is running on the target host:
How to find SMB version?
The SMB version can also potentially be identified by using the auxiliary/scanner/smb/smb_version Metasploit module.
What tool can be used to intercept SMB traffic?
If this fails, a connection can be initiated using Nmap or any tool capable to connect to SMB shares and the traffic can be intercepted using Wireshark, which will reveal the hostname of the machine, the SMB version, the operating system version, and other useful information:
What is server message block?
Server Message Block is a network protocol used to provide shared access to files, printers, and serial ports between nodes on a network. SMB servers can be accessed through various command-line tools such as SMBClient or through file browsing tools. This service runs on either port 139 or port 445 by default.
What is NSE in networking?
The Nmap Scripting Engine (NSE) allows users to write (and share) simple scripts (using the Lua programming language ) to automate a wide variety of networking tasks.
Why is SMB1 so insecure?
SMB1 was the first implementation of SMB. It used 16-bit packet and small data buffers, which greatly limited performance, it did not have any encryption for data in transit whatsoever, which is why it is so insecure. In addition to this, it is highly susceptible to MITM (man-in-the-middle) attacks.
How does SMB2 improve performance?
SMB2 improved performance by increasing packets to 32-bit and 128-bit for files , furthermore unnecessary data that was transmitted when performing operating via SMB was substantially reduced. Security was improved to prevent MITM attacks through packet signing although still no built-in encryption support.
What does SMB stand for in pentest?
Before learning how to enumerate SMB , we must first learn what SMB is . So let’s get started. SMB stands for server message block.
How to enumerate service?
There are many ways to enumerate the service itself. The quickest way is to use a tool called enum4linux. However I have noticed that sometimes the output is not very pleasing. Other tools which I feel better are smbclient and smbmap. I will also show how to manually access smb folder , but sometimes that fails. So primarily , you should be well versed with smbclient and smbmap , they are much more reliable.
What are the security flaws in SMB?
The first obvious flaw is using default credentials or easily guessable and sometimes even no authentication for access of important resources of the server. Admins should make sure to use strong passwords for users who want to access resources using SMB.
What port does a syslog run on?
It primarily runs on port 445 or port 139 depending on the server . It is actually natively available in windows, so windows users don’t need to configure anything extra as such besides basic setting up. In linux however ,it is a little different.
What is the -H argument in a file?
The -H argument is for hostname and the -R is recursive switch, meaning it will go through each directory and list out the files. Although I must tell you that it’s working now only because anonymous login is allowed, i.e. in a real life , you’d probably need a username and password.
Can you download files from a TMP disk?
Yay , we got a shell in tmp disk. Now we can download or upload files into the share. As you can see , this is actually useful for both system administrators and pentesters. That’s why, the best way to start your ethical hacking career is to first be a system or network admin. It becomes easier down the lane if you start from there.
Can you retrieve files using smbmap?
Now you can actually retrieve the files using smbmap as well, I’ll leave that as an exercise. But what if we wanted a full fledged command prompt like a ftp prompt? That’s very much possible with smbclient. Lets try to do that.
What is SMBclient?
smbclient - ftp-like client to access SMB shares
What is SMB port?
SMB short for server message block is a protocol for sharing resources e.g (printers,files). It is commonly known to be found on port 445 or port 139. This protocol is available on windows by default. Note: In Linux we must install a samba server because linux doesn't use the smb protocol.
What does smbmap -h do?
smbmap -H [ip/hostname] will show what you can do with given credentials (or null session if no credentials). See examples in the previous section.
What does exit do?
exit takes care of any password request that might pop up, since we’re checking for null login
Can you check smb version in PCAP?
When in doubt, we can check the smb version in PCAP. Here’s an example Unix Samba 2.2.3a:
Is Samba server secure?
Samba servers seem to be notorious for being insecure. A quick google search will reveal many exploits for smb. Patch it!
Why SMB Enumeration is important?
SMB is used to communicate over TCP/IP in a network. It is a client-server protocol used for file sharing, printers, serial ports and other resources on a network.
How many Nmap SMB scripts are there?
There are 35 Nmap SMB scripts as part of the NSE. We will be going through the most common ones only in this article. While complete list can be seen using below command and can be used on need basis:
Why is Nmap SMB a go-to protocol?
Because of it’s not so “Secure” history, it’s always been a go-to protocol for any threat actor or ethical hackers. With tools like the Nmap SMB Scripts it makes it even easier for attackers to perform SMB Enumeration. And also, it’s not surprising that we still have legacy End Of Life (EOF) operating systems running in various public and private sector organizations.
Why is SMB a hot target?
SMB protocol commonly known as Server Message Block protocol has been a hot target among threat actors for many years because of its complexity and open nature. This protocol was prone to plethora of attacks from SMB Null Sessions to Eternal Blue. It is the reason we are about to cover all things related to SMB Enumeration and go in-depth with Nmap SMB Scripts also known as the Nmap Scripting Engine (NSE).
What is nmap used for?
By design, nmap comes with various scripts that can be used to detect various vulnerabilities or CVEs. Specifically for SMB, we can use nmap to detect below CVEs:
How many SMB ports are there?
A quick query in Shodan confirms that there are 1,428,194 publicly accessible SMB ports and as it can be easily conceived that not everyone will be doing their housekeeping, lefts many of them a hot target to attack.
What is SMB protocol?
SMB is used to communicate over TCP/IP in a network. It is a client-server protocol used for file sharing, printers, serial ports and other resources on a network. SMB can allow other applications and users to access files or execute command on a remote server.
What is Automated Enumeration#N#Enum4Linux?
Automated Enumeration#N#Enum4Linux is a great tool for SMB Scanning. Enum4Linux checks all SMB Enumeration types with#N#-A (do all enumeration) parameter. Enum4Linux checks for null session, share listing, domain info,#N#password policy and etc.
What is SMB in Windows?
Introduction#N#What is SMB?#N#SMB (Server Message Block) is a network protocol for accessing files, printers and other devices#N#on the network. Server Message Block provides file sharing, network browsing, printing services,#N#and interprocess communication over a network. Most usage of SMB involves computers#N#running Microsoft Windows, where it was known as “Microsoft Windows Network” before the#N#introduction of Active Directory. SMB uses TCP 139 and TCP 445 ports by default. Latest SMB#N#version is SMBv3. SMB has been the subject of numerous vulnerabilities from past to present.#N#Lets talk about some of these.
Is SMB signing available?
avoid issues like tampering of packets and “man in the middle” attacks. SMB signing is available
Can we write malicious code on the target?
We can write a malicious code on the target. Let’s check it on the target.
What is acccheck in Kali Linux?
We will use a tool called acccheck for this purpose. It is a password dictionary attack tool that targets windows authentication via the SMB protocol. We will see more about password cracking later. First I will try it with the user “user”. In Kali Linux, most of the password dictionaries are present in “usr/share/dirb” directory. So I specify a dictionary which consists of most common passwords used.
What is enumeration in a network?
Enumeration is the process of collecting information about user names, network resources, other machine names, shares and services running on the network. Although little bit boring, it can be very helpful for the success of the hack in real time. In our previous parts, we have performed scanning and banner grabbing. So we already know what services are running on the target machine. They include FTP, telnet, SMTP and SMB etc. We can perform enumeration on all these services.
What happens when you get the correct password on a scanner?
Once the tool gets the correct password, it stops the scan and displays a success message as shown below. Voila … the password of the user “user” is “user” only.
What is enum4linux?
The first tool we will use is enum4linux. As the name suggests, it is a tool used for enumeration of Linux. To see all the options of this tool, just type “ enum4linux -h “. Using this tool, first let us see the users of the SMB service. Open terminal and type command “ enum4linux -U 192.168.25.129 ” as shown below.
What does SMB stand for?
SMB stands for Server Message Block. Its mainly used for providing shared access to files, printers and miscellaneous communications between nodes on a network. It also provides an authenticated inter-process communication mechanism. It is a predecessor of Common Internet File system (CIFS). To know more about SMB please go here.
Is SMB a workgroup?
As we can see above, this system is part of a workgroup. Know the difference between domain and workgroup. We can see below that it has listed all the SMB users present on the target.

Introduction
SMB Versions
- Before diving into the various methods using to collect information from SMB, it is important to understand the iterations SMB went through over the years and why some of them are known to be highly insecure: 1. SMB1 was the first implementation of SMB. It used 16-bit packet and small data buffers, which greatly limited performance, it did not have any encryption for data in transit …
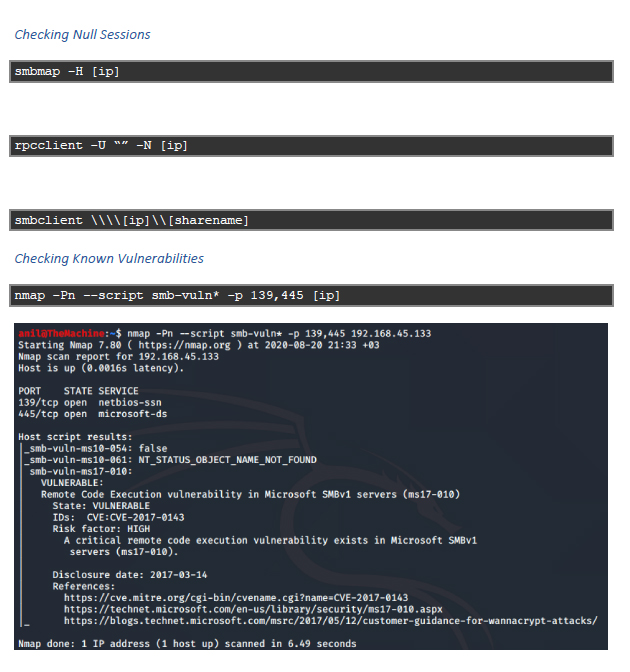
Identifying An SMB Server
- Port scanning tools such as Nmap can be used to identify whether an SMB server is running on the target host: The scan has identified that the remote server is running SMB on port 139/445.
Identifying Smb/Os Version
- A fundamental step in enumerating SMB is to identify the version that the server is running on, as this will help in determining whether any known exploit for that version can be abused to obtain remote code execution. One way to do this is to use the -sV flag in Nmap, although this will often fail as most versions SMB do not display the version nu...
Identifying Known Vulnerabilities
- Tools such as SearchSploit can then be used to identify known vulnerabilities: Alternatively, vulnerablity databases such as CVE, NVD and VULDBcan be consulted.
Null Session Attack
- A null session allows users to remotely authenticate to SMB by using an empty username and password. This usually only allows access to the hidden share called IPC$ (which stands for interprocess communication), but additional shares could have been configured to use this method. Null sessions could be used to gather more information about the host and its network, …
Nmap Scripts
- The Nmap Scripting Engine (NSE) allows users to write (and share) simple scripts (using the Lua programming language) to automate a wide variety of networking tasks. Nmap comes with several SMB-related scripts such as: 1. smb-enum-shares – Enumerates SMB shares in an SMB server. 2. smb-brute – Performs brute-force password auditing against SMB servers. 3. smb-system-inf…
Common Credentials
- A few common passwords or usernames (if unknown) such as admin, administrator, root, test, etc. should be tried if null sessions are disabled on the remote SMB server. This is safer than brute-forcing and it should always be tried when possible. In the example above, a connection was established as the test by using a password of “test”. An SMB authentication can also be pe…
Bruteforcing Credentials
- A brute-force attack consists of an attacker submitting a number of passwords or usernames with the purpose of identifying the correct combination to access a given system. Network cracking tools such as Hydracan be used to perform bruteforce attacks against online services such as FTP, HTTP, SMB etc. In this specific case, it will be a dictionary attack, meaning hydra will use …
Packet Sniffing
- Packet sniffing is the practice of gathering, collecting, and logging some or all packets that pass through a computer network, regardless of how the packet is addressed. Because data transmitted over older versions of SMB (version 1) on port 139,445 is unencrypted, an attacker could intercept traffic on the network and identify the credentials being used to perform the authe…