
What Are the Benefits of Hashing?
- Data Retrieval One of the benefits of hashing is that it uses algorithms to map object data to an integer value. ...
- Digital Signatures Signing documents digitally is a common practice today. Apart from data retrieval, hashing also helps encrypt and decrypt digital signatures used to authenticate message senders and receivers. ...
- Password Security
What is a hash and why is it important?
hashes are important in cryptography to determine if data has been modified or not. theoretically, any bit flip will cause a different hash value to be computed. all data files used as evidence in law are hashed immediately to prove non-corruption. Drive Blockchain Strategy.
What is true about hashing?
Hashing is generating a value or values from a string of text using a mathematical function. Hashing is one way to enable security during the process of message transmission when the message is intended for a particular recipient only. A formula generates the hash, which helps to protect the security of the transmission against tampering.
How to make hashish at home?
- Line your bucket Line a bucket with a bag with the highest number of microns (aka the largest filter hole).
- Fill your bucket Fill the bag with one-third ice and up to 200 grams of cannabis. ...
- Stir the mixture Using a large wooden spoon, agitate the mixture by stirring vigorously for up to 5 minutes. ...
What is a hashing algorithm and how does it work?
What is a Hashing Algorithm and How Does it Work? A hashing algorithm is a mathematical algorithm that converts an input data array of a certain type and arbitrary length to an output bit string of a fixed length. Hashing algorithms take any input and convert it to a uniform message by using a hashing table.
What are the advantages of hashing passwords?
Password hashing add a layer of security. Hashing allows passwords to be stored in a format that can't be reversed at any reasonable amount of time or cost for a hacker. Hashing algorithms turn the plaintext password into an output of characters of a fixed length.
What is the main purpose of hashing?
Hashing is a cryptographic process that can be used to validate the authenticity and integrity of various types of input. It is widely used in authentication systems to avoid storing plaintext passwords in databases, but is also used to validate files, documents and other types of data.
What is an advantage of using a hashing function in cyber security?
Hashing is a one-way function where a unique message digest is generated from an input file or a string of text. No keys are used. The message is encoded in a way that only authorized parties can access it. It's used to prevent unauthorized users from reading data from a file by rendering it into an unreadable form.
What is the main advantage of a hash based indexing structure?
Main advantage is synchronization. In many situations, hash tables turn out to be more efficient than search trees or any other table lookup structure. For this reason, they are widely used in many kinds of computer softwares, particularly for associative arrays, database indexing, caches and sets.
Why is hashing the best data structure?
In a hash table, data is stored in an array format, where each data value has its own unique index value. Access of data becomes very fast if we know the index of the desired data. Thus, it becomes a data structure in which insertion and search operations are very fast irrespective of the size of the data.
Which is better hashing or encryption?
The original information can be easily retrieved if we know the encryption key and algorithm used for encryption. It is more secure in comparison to encryption. It is less secure in comparison to hashing.
How secure is hashing?
The MD5 algorithm is considered harmful today and Google announced the first SHA1 collision in 2017. Both hashing algorithms have been deemed unsafe to use and deprecated by Google due to the occurrence of cryptographic collisions. Google recommends using stronger hashing algorithms such as SHA-256 and SHA-3.
What is the use of hashing in cryptography?
A cryptographic hash function is an algorithm that takes an arbitrary amount of data input—a credential—and produces a fixed-size output of enciphered text called a hash value, or just “hash.” That enciphered text can then be stored instead of the password itself, and later used to verify the user.
What are the advantages of hashing in DBMS?
The advantages of using Static Hashing in the DBMS are as follows: Performance is exceptional for smaller databases. Aids in Storage management. Hash key values help in faster access to the storage addresses.
What are the 3 main properties of hash function?
One of the hardest concepts my students had grasping was secure cryptographic hash functions, partially because of the number theory, but also in differentiating between the three properties of a secure hash function: collision resistance, preimage resistance, and second preimage resistance.
What is hashing with example?
Hashing is an important data structure designed to solve the problem of efficiently finding and storing data in an array. For example, if you have a list of 20000 numbers, and you have given a number to search in that list- you will scan each number in the list until you find a match.
What is a hash function cyber security quizlet?
What is a hash function. A fixed-length string of numbers and letters generated from a mathematical algorithm and an arbitrarily sized message such as an email, document, picture or other type of data.
What is hashing in cyber forensics?
Cryptographic hash function is a function that converts a message of any length to a data of fixed length. The purpose of cryptographic hash is to ensure the integrity of data. Digital forensic tool is a tool to extract evidence data from different storage media, such as hard Drive, Memory, file system etc.
What is hash value in cyber security?
Hashes are the output of a hashing algorithm like MD5 (Message Digest 5) or SHA (Secure Hash Algorithm). These algorithms essentially aim to produce a unique, fixed-length string – the hash value, or “message digest” – for any given piece of data or “message”.
What is a hash in terms of how it is used in network security?
Hashing is an algorithm performed on data such as a file or message to produce a number called a hash (sometimes called a checksum). The hash is used to verify that data is not modified, tampered with, or corrupted. In other words, you can verify the data has maintained integrity.
How to maintain balance in hashing?
There are two ways of maintaining this balance. Controlling speed by selecting the space to be allocated for the hash table. Controlling space by choosing a speed of recovery.
What did Luhn predict would make searching faster?
In 1953 Luhn had the idea to put all the information in a bucket. He predicted that this would make searching faster. And this information can consist of numbers as well as text.
What are the two inventions of Luhn?
The two other great inventions of Luhn are KWIC and SDI systems.
Who invented the hazing algorithm?
Hans Peter Luhn invented Hashing. He was a conscientious scientist in IBM researching the field of Computer Science and Information Science. There is one more famous algorithm he contributed- the Luhn algorithm. Luhn was born in Germany but after the war, he had to move to the United States as he was working in the textile field. While in the textile field he invented Lunometer which is still used. A Luminometer is a thread counting device.
Can a password be modified?
Hashed passwords cannot be modified, stolen, or jeopardized. No well-recognized and efficient key or encryption scheme exists that can be misused. Also, there is no need to worry if a hash code is stolen since it cannot be applied anywhere else. Two files can be compared for equality easily through hashing.
What Is Hashing?
Hashing is a one-way function that maps data of any size to a fixed-length hash value. It’s different from encryption because it doesn’t scramble the data — it creates a unique fingerprint.
How Does Hashing Work?
The hashing function is usually based on cryptographic principles and uses an algorithm to create the hash value. The algorithm can be either symmetric or asymmetric.
Benefits of Hashing
Hashing is best suited for storing passwords because it’s faster than encrypting and decrypting them.
The Bottom Line
Hashing is a one-way function that produces a unique fingerprint for each piece of data. It’s perfect for storing passwords because it’s quick and easy to replace or update the file if you lose it.
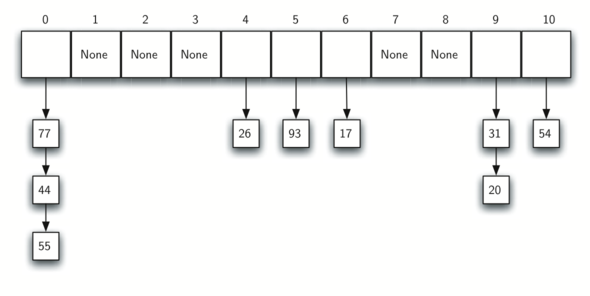
What Is Hashing?
- Hashing is an algorithm that calculates a fixed-size bit string value from a file. A file basically contains blocks of data. Hashing transforms this data into a far shorter fixed-length value or key which represents the original string. The hash value can be considered the distilled summary of …
Types of Hashing
- There are many different types of hash algorithms such as RipeMD, Tiger, xxhash and more, but the most common type of hashing used for file integrity checks are MD5, SHA-2 and CRC32. MD5- An MD5 hash function encodes a string of information and encodes it into a 128-bit fingerprint. MD5 is often used as a checksum to verify data integrity. However, due to its age, MD5 is also k…
Using Hashing in 2BrightSparks Software
- In the backup and synchronization software, SyncBackPro/SE/Free, hashing is mainly used for file integrity checks during or after a data transfer session. For example, a SyncBack user can turn on file verification (Modify profile > Copy/Delete) or use a slower but more reliable method (Modify profile > Compare Options) which will enable hashing to check for file differences. Different has…
Summary
- In conclusion, hashing is a useful tool to verify files are copied correctly between two resources. It can also be used to check if files are identical without opening and comparing them. To find out more about hashing, please visit the Wikipedia page.
What Is Hashing?
- Hashing is a one-way function that maps data of any size to a fixed-length hash value. It’s different from encryption because it doesn’t scramble the data — it creates a unique fingerprint. Hashing is commonly used to verify the integrity of files, verify the identity of people in an organization. As a result, it can ensure that the data stored on your hard drive hasn’t been corrup…
How Does Hashing Work?
- The hashing function is usually based on cryptographic principles and uses an algorithm to create the hash value. The algorithm can be either symmetric or asymmetric. Symmetric hashing algorithms, also known as private-key algorithms, use one secret key, called the private key, for both encryption and decryption. So, if you know the private key, you can decrypt the data. This i…
Benefits of Hashing
- Hashing is best suited for storing passwordsbecause it’s faster than encrypting and decrypting them. It’s also easy to replace a lost or corrupted password file if you use it to store the passwords. Many companies don’t have a dedicated computer or operating system for their password database. So, they have to use their primary operating system to ...
The Bottom Line
- Hashing is a one-way function that produces a unique fingerprint for each piece of data. It’s perfect for storing passwords because it’s quick and easy to replace or update the file if you lose it. Do you use it in your organization? Would you like to learn more? Feel free to leave comments below. We would be happy to continue the discussion.