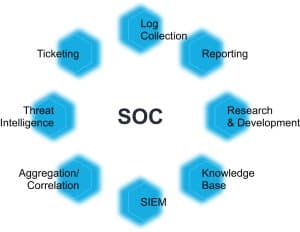
SIEM stands for Security Incident Event Management and is different from SOC, as it is a system that collects and analyzes aggregated log data. SOC stands for Security Operations Center and consists of people, processes and technology designed to deal with security events picked up from the SIEM log analysis.
Is SIEM a SOC?
The SOC and Security Information and Event Management (SIEM) The foundational technology of a SOC is a SIEM, which aggregates device, application logs, and events from security tools from across the entire organization.
How is SIEM used in SOC?
SIEM solutions aggregate data from multiple sources and use data analytics to identify the most probable threats. This enables SOC analysts to focus their efforts on the events most likely to constitute a real attack against their systems.
What is the difference between SOC and cyber security?
A SOC 2 report assesses data management by third-party service providers and focuses on information security processes for specific business units or services. The SOC for Cybersecurity, on the other hand, evaluates the entire organization's cybersecurity risk management program.
What are the 3 types of data in SIEM?
Gartner identifies three critical capabilities for SIEM (threat detection, investigation and time to respond) — there are other features and functionality that you commonly see in the SIEM market, including: Basic security monitoring. Advanced threat detection. Forensics & incident response.
What is SOC example?
An SoC for a sound-detecting device, for example, might include an audio receiver, an analog-to-digital converter (ADC), a microprocessor, memory, and the input/output logic control for a user - all on a single chip.
What are the three pillars of a SOC?
As SOCs implement automation capabilities, so too will attackers, and with increasing sophistication....There are three pillars to the autonomous SOC:Data. ... Analytics. ... Community.
Is SoC a hardware or software?
An SoC consists of hardware functional units, including microprocessors that run software code, as well as a communications subsystem to connect, control, direct and interface between these functional modules.
How many types of SoC are there?
There are four main types: SOC 1, SOC 2, SOC 3, and SOC for Cybersecurity, with subsets of each.
What are the types of SoC?
There are three types of SOC reports: SOC 1, SOC 2, and SOC 3....These reports can play an important role in:Oversight of the organization.Vendor management programs.Internal corporate governance and risk management processes.Regulatory oversight.
What is an example of a SIEM?
Some common SIEM examples you might have heard of include ArcSight ESM (Enterprise Security Management), AT&T Cybersecurity (formerly known as AlienVault), Fortinet, IBM QRadar, McAfee SIEM, and Splunk.
Is SIEM a firewall?
Yes, a SIEM doesn't replace your firewall. A firewall provides your first line of perimeter defense. The firewall allows or denies traffic in or out, while a SIEM analyzes log files.
What is a soar vs SIEM?
While SIEM ingests various log and event data from traditional infrastructure component sources, a SOAR pulls in information from external emerging threat intelligence feeds, endpoint security software and other third-party sources to get a better overall picture of the security landscape inside the network and out.
What role does SIEM play in security operations?
In addition to providing log management capabilities, SIEM has evolved to offer various functions for managing security and compliance. These include user and entity behavior analytics (UEBA) and other AI-powered capabilities.
What is SIEM and how it works?
SIEM solutions allow organizations to efficiently collect and analyze log data from all of their digital assets in one place. This gives them the ability to recreate past incidents or analyze new ones to investigate suspicious activity and implement more effective security processes.
What is the main purpose of SIEM?
Security information and event management (SIEM) technology supports threat detection, compliance and security incident management through the collection and analysis (both near real time and historical) of security events, as well as a wide variety of other event and contextual data sources.
How Splunk can be used in a SOC?
With Splunk software, all SOC personnel have quick access to all of the data and information needed to quickly detect, investigate and remediate threats. Splunk products can be used by a tier 1 analyst to do basic research based on a time period, keyword, IP address or machine name.
What is SOC in SIEM?
The perfect way to overcome most of the above problems that comes with a standardized Siem solution is the implementation of the Security Operations Centre (SOC). It’s a process that integrates many people, a variety of skill sets, and continuous enhancement in alerts and analysis development. It ensures a 24-hour coverage integrated with vulnerability management, threat intelligence, incidence response, and threat hunting. It easily detects threats and launches mitigation where necessary. Purchasing this solution in-house can be a little bit expensive. Most organizations prefer outsourcing this feature through MSSP (Managed Security Service Provider).
What is the biggest issue with implementing Siem?
The biggest issue when it comes to implementing Siem is the quantity of data that will be fed to it. Most Organizations produce huge tons of data each day while devices also produce logs that need to be scrutinized by the Siem security in order to detect threats. Medium-sized organizations generate about a billion data logs and events each day that need to be sent to Siem security for analysis and storage. With a lot of data in place, sifting to narrow down to breached data that has been siphoned off your network by attackers might prove to be a little difficult. If you rely on a regular siem solution you might experience log data issues.
How to identify a breach in Siem?
The best strategy when it comes to identifying breaches is through the creation of alerts. A typical Siem system features standard alerts that can only be generated once the system is set up with the right data logs flocking in. To get alerts on attacks depends solemnly on the quality and quantity of the siem solution. A lot of pre-loaded alerts that come in standard siem solution are blended with both high and low veracity. You will discover that they don’t correlate sometimes and thus all threats from cyberattacks cannot be detected. They hardly execute behavioral analysis and also create alerts on malicious behaviors. This ends up leaving remarkable gaps when it comes to breach detection. Another issue that comes with experiencing alert problems with a standard siem solution is large data volumes being produced. With a lot of data logs generated based on the activities carried out across the organization, thousands of alerts end up being generated. For a typical security team, it’s quite impossible to sort all the alerts even if they're categorized as either profound, high, medium, and low. Most profound and high alerts are normally difficult to go passed through.
What is SOC monitoring?
Monitoring of security and detecting threats is a vital element when it comes to attaining a secure environment for your organization. Siem and SOC gives you a clear picture of what is going on within your organization’s network without being blinded to any type of attack, inside activities, and anomalies. To get such a clear picture, organizations when purchasing Siem security systems, they tend to go for highly-priced Siem software which can easily collect log data, run alert rules, automatically find threats and data breaches. With an exception made by some of the largest organizations, that are well funded and staffed with the best security teams, getting value from just Siem alone might prove to be difficult. Ensure that you make use of your Siem returns on investment by implementing security operations whereby Siem security technology is fully supported by layouts, staff, analysis, and automation.
Can Siem and SOC be combined?
In reality, implementing Siem to solve your organization’s security problem wouldn’t be of much value as compared to combining both Siem and SOC together. With these two working together, advanced threats will be detected easily.
