What is the effect of configuring an ACL with only ACEs that deny traffic?
- The ACL will permit any traffic that is not specifically denied.
- The ACL will block all traffic.
- The ACL must be applied inbound only.
- The ACL must be applied outbound only.
Full Answer
Should ACL be applied inbound or outbound?
The ACL must be applied outbound only. Because there is a deny any ACE at the end of every standard ACL, the effect of having all deny statements is that all traffic will be denied regardless of the direction in which the ACL is applied. 23. Which type of ACL statements are commonly reordered by the Cisco IOS as the first ACEs?
What is the ACL and how does it work?
The ACL will permit any traffic that is not specifically denied. The ACL will block all traffic.* The ACL must be applied inbound only. The ACL must be applied outbound only.
What does the ACL permit or block?
The ACL will permit any traffic that is not specifically denied. The ACL will block all traffic. The ACL must be applied inbound only. The ACL must be applied outbound only.
What is the purpose of reordering the Aces in the ACLS?
The ACEs that have host criteria such as in the statement permit host 192.168.10.5, are reordered as the first statements because they are the most specific (have the most number of bits that must match). 24. A network administrator is configuring an ACL to restrict access to certain servers in the data center.
What is ACL in network administrator?
Where to place extended ACLs?
What IP address does a network administrator need to configure?
What sequence number to add new deny ACE?
Does the ACL perform as designed?
About this website

What is the result of configuring an ACL with only aces that deny traffic?
Explanation: Because there is a deny any ACE at the end of every standard ACL, the effect of having all deny statements is that all traffic will be denied regardless of the direction in which the ACL is applied.
Is the quickest way to remove a single ace from a named ACL?
What is the quickest way to remove a single ACE from a named ACL? Use the no keyword and the sequence number of the ACE to be removed.
Which configuration would an outbound ACL placement be preferred over an inbound ACL placement?
In which configuration would an outbound ACL placement be preferred over an inbound ACL placement? Explanation: An outbound ACL should be utilized when the same ACL filtering rules will be applied to packets coming from more than one inbound interface before exiting a single outbound interface.
How does ACLs filter traffic?
These type of ACLs, filter traffic based on upper layer session information. They react to sessions originated inside the router to whether permit outbound traffic or restrict incoming traffic. The router recognizes the outbound ACL traffic and creates a new ACL entry for the inbound.
What is considered a best practice when configuring ACLs?
Place identical restrictions on all vty lines. Remove the vty password since the ACL restricts access to trusted users. Apply the ip access-group command inbound.
What is the difference between a standard and extended ACL?
ACL Details and Examples Standard Access lists match only based on the source IP address of the packet. Extended Access lists can match on source and destination address, in addition to port, protocol, and many other fields.
Which two statements are generally considered to be best practices in the placement of ACLs choose two?
Place standard ACLs close to the source IP address of the traffic. Place extended ACLs close to the destination IP address of the traffic.
Which statement describes the difference between inbound and outbound ACL operation?
Which statement describes a difference between the operation of inbound and outbound ACLs? Inbound ACLs are processed before the packets are routed while outbound ACLs are processed after the routing is completed.
When applying an ACL What is the difference between using the access group command and the access class command?
Access-group is used to bind a access-list with a particular interface. access-class is used to bind a access-list to VTY lines. in order to restrict access through telnet.
Which three parameters can ACLs use to filter traffic?
The criteria used by the router to determine whether packets can traverse the network is made by configuring ACLs. With access control lists, we can filter traffic based on; destination and source layer 3 address, destination and source port number, as well as the protocol in use.
What is the importance of configuring the access control list ACL )?
ACLs can also provide traffic flow control, restrict contents of routing updates, and decide which types of traffic are forwarded or blocked. Normally ACLs reside in a firewall router or in a router connecting two internal networks. You can set up ACLs to control traffic at Layer 2, Layer 3, or Layer 4.
What are the two main types of access control lists ACLs?
There are two types of ACLs: Filesystem ACLs━filter access to files and/or directories. Filesystem ACLs tell operating systems which users can access the system, and what privileges the users are allowed. Networking ACLs━filter access to the network.
How Can an ace be removed from a named ACL?
You can delete any ACE from any ACL (named or numbered) by using the ip access-list command to enter the ACL's context, and then using the no < seq-# > command, see Deleting an ACE from an existing ACL. Deleting the last ACE from an ACL leaves the ACL in memory.
What type of ACL offers greater flexibility and control over network?
Question: What type of ACL offers greater flexibility and control over network access? Explanation: The two types of ACLs are standard and extended. Both types can be named or numbered, but extended ACLs offer greater flexibility.
Which two packet filters could a network administrator use on an IPv4?
Which two packet filters could a network administrator use on an IPv4 extended ACL? (Choose two.) Explanation: Extended access lists commonly filter on source and destination IPv4 addresses and TCP or UDP port numbers. Additional filtering can be provided for protocol types.
When to use outbound ACL?
An outbound ACL should be utilized when the same ACL filtering rules will be applied to packets coming from more than one inbound interface before exiting a single outbound interface. The outbound ACL will be applied on the single outbound interface. 2.
What is the only filter that can be applied with a standard ACL?
The only filter that can be applied with a standard ACL is the source IP address. An extended ACL can use multiple criteria to filter traffic, such as source IP address, destination IP address, type of traffic, and type of message. 3.
Where to place ACLs?
Place standard ACLs close to the source IP address of the traffic.
Where to place standard ACLs?
Place standard ACLs close to the destination IP address of the traffic.*
What is ACL in network administrator?
A network administrator is configuring an ACL to restrict access to certain servers in the data center. The intent is to apply the ACL to the interface connected to the data center LAN. What happens if the ACL is incorrectly applied to an interface in the inbound direction instead of the outbound direction?
Where to place extended ACLs?
Place extended ACLs close to the source IP address of the traffic.
What IP address does a network administrator need to configure?
A network administrator needs to configure a standard ACL so that only the workstation of the administrator with the IP address 192.168.15.23 can access the virtual terminal of the main router. Which two configuration commands can achieve the task
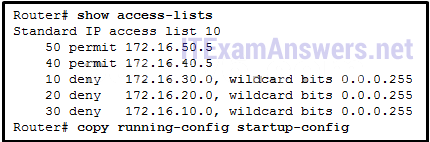
What sequence number to add new deny ACE?
Manually add the new deny ACE with a sequence number of 5.
Does the ACL perform as designed?
The ACL does not perform as designed.*
What is ACL in network administrator?
A network administrator is configuring an ACL to restrict access to certain servers in the data center. The intent is to apply the ACL to the interface connected to the data center LAN. What happens if the ACL is incorrectly applied to an interface in the inbound direction instead of the outbound direction?
Where to place extended ACLs?
Place extended ACLs close to the source IP address of the traffic.
What IP address does a network administrator need to configure?
A network administrator needs to configure a standard ACL so that only the workstation of the administrator with the IP address 192.168.15.23 can access the virtual terminal of the main router. Which two configuration commands can achieve the task
What sequence number to add new deny ACE?
Manually add the new deny ACE with a sequence number of 5.
Does the ACL perform as designed?
The ACL does not perform as designed.*