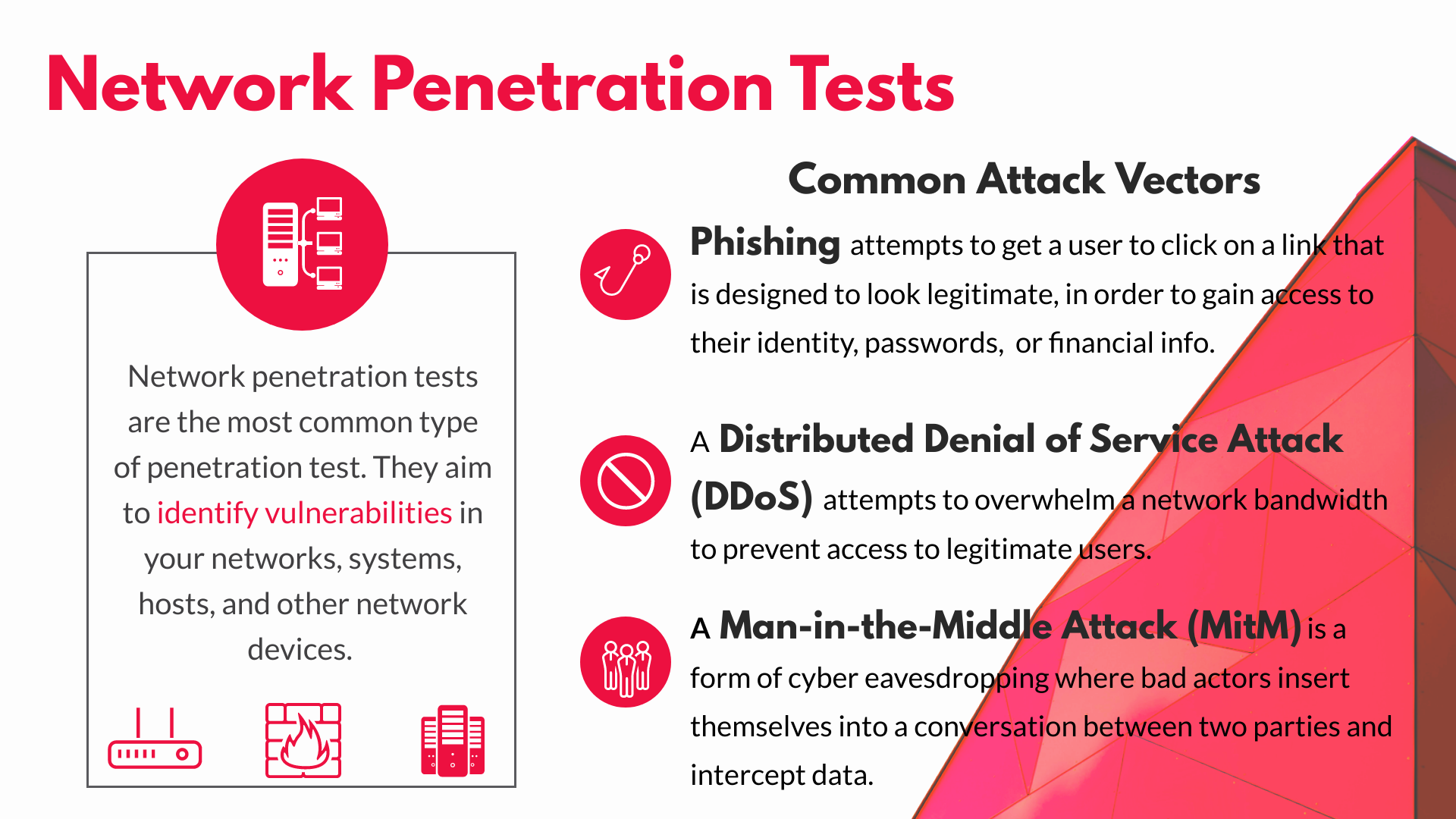
Why is Penetration Testing Required?
- It identifies a simulation environment i.e., how an intruder may attack the system through white hat attack.
- It helps to find weak areas where an intruder can attack to gain access to the computer’s features and data.
- It supports to avoid black hat attack and protects the original data.
- It estimates the magnitude of the attack on potential business.
How long does it take to do a penetration testing?
How Long Does Penetration Testing Take? The exact amount of time it takes to execute penetration testing will vary from organization to organization depending on many different factors, including network size and complexity. In general, though, it takes roughly one to two weeks to do a thorough exploration.
What does it take to become a penetration tester?
Steps to Becoming a Penetration Tester Get a Degree: A bachelor’s degree in computer science or engineering, cybersecurity, or IT usually suffices to begin a... Build Experience: Penetration testing professionals usually build and hone their skills by working in entry-level IT,... Obtain ...
What is a penetration test and how does it work?
Penetration testing, also known as pen testing, is a staged cybersecurity attack that mimics an actual security incident. The simulated attack can target one or multiple parts of your security system, looking for weak points a malicious hacker could exploit.
When should you do a penetration test?
The question in part will depend on what kind of pen test you do, but there are some broad guidance we would suggest. How often? A penetration test should be conducted on a regular basis, and at least once a year and after any significant change.
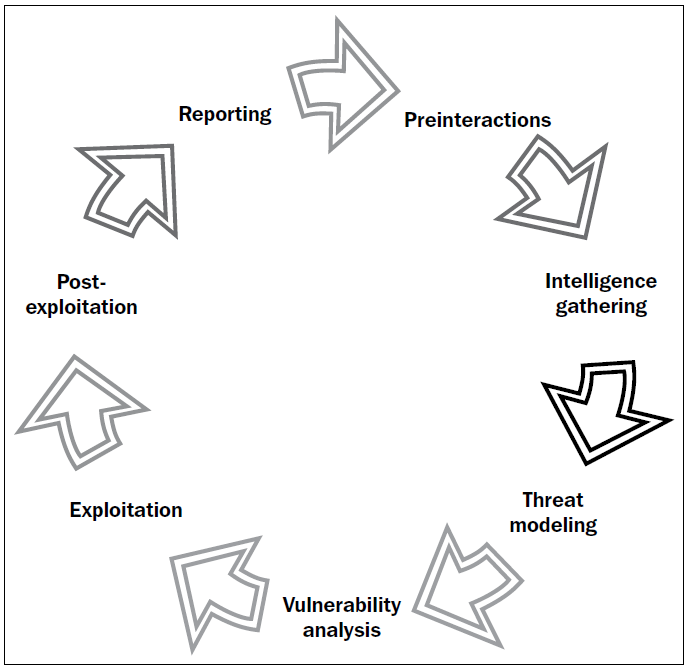
What are the threats attacking my business?
Script Kiddie: A script kiddie is a loose term that relates to a summer student that, in an effort to learn about technologies, may find themselves exploiting and obtaining unauthorized access to various environments. While their underlying motivation may not be malice, they break various laws.
What motivates a hacker to compromise my website?
Understanding the various threats, the motivation to compromise your website depends heavily on the attacker. Targets of opportunity, who do not patch or adopt secure configuration standards, are a target for lower skilled attackers who may compromise your website just because they can.
Why do I need a penetration test?
If you store, process, or transmit Credit-cards, the PCI council may mandate that you do so. If not, there are various regulatory requirements most countries that mandate protection of privacy-related information (PII) via the PIPEDA law in Canada, personal health information (PHI) via the PHIPA law in Canada.
What is penetration testing?
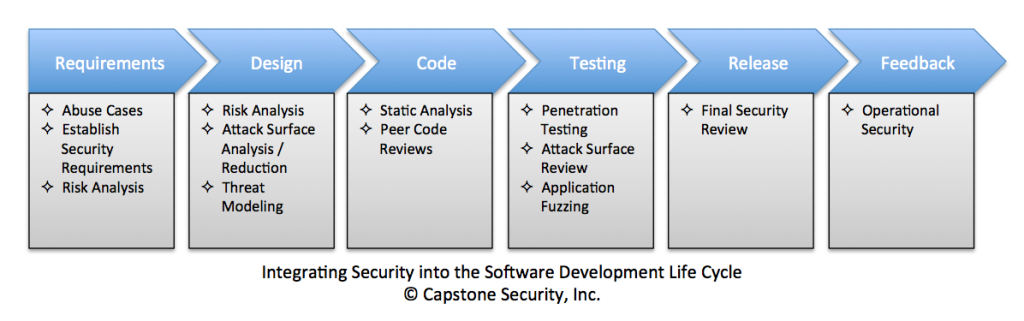
To put it in simple words, Penetration Testing activities consist of “examining” the weaknesses of a corporate IT infrastructure. Once these weak spots have been identified, the person who carries out the activity tries to exploit these vulnerabilities in a very safe way. Vulnerabilities can be found pretty much everywhere in the software:
What is the purpose of a penetration tester?
Obviously, as previously mentioned, the main goal is to test how vulnerable is the network. How deep can the Pentester go?
What is the difference between penetration testing and vulnerability scanning?
When we talk about vulnerability assessment , we mean spotting certain vulnerabilities that remain in a system, Swascan offers an advanced Vulnerability Assessment tool that identifies and solves all vulnerabilities of websites and web applications. On the other hand, penetration test is an authorized attack (which is simulated) on a system to test its security.
What is a black box penetration test?
During a Black Box Penetration Test, the person who carries out the activity ( Pentester) will not have any information any information regarding the Web Application and its source code. This is why this specific methodology often requires a lot of time and the Pentester uses automated tools in order to find vulnerabilities and weak spots. This approach sometimes is referred to as “trial and error”.
Why do pentesters do a spot test?
Usually, Pentesters carry out such tests on the spot because of the need to be close to the wireless network’s signal. This test spots vulnerabilities in terms of: access point wireless, admin credentials and wireless protocols.
Why are vulnerability scanning tools useful?
Vulnerability Scanning tools are very useful to spot vulnerabilities and provide a detailed overview of the customer’s IT infrastructure.
How many people are needed for penetration testing?
Penetration Testing often requires more than one person, we are talking of teams. To conduct a single Penetration Test we can have dedicated teams that we divide in:
What is the purpose of penetration testing?
Another common question regarding what is the primary purpose of Penetration Testing is whether or not it is necessary to perform this type of testing if you are developing a software product. The truth is that performing an automated web vulnerability assessment is often a good idea regardless of whether or not you intend to sell a Web application. Automated vulnerability detection will help you develop a thorough security program by pinpointing specific security issues in your product. However, in some cases you may still need to engage in manual testing in order to discover the primary purpose of Web testing.
What is penetration test?
A Penetration Test is conducted to verify the usability and security of a Web application. The objectives of this type of test are to detect any vulnerabilities in the application, as well as any areas of concern that could result in user or system compromise. Users may not be aware of all the potential threats they may face in the online environment. Through this process, weaknesses and vulnerabilities are identified that could potentially allow hackers and other bad elements to gain unauthorized access to a company’s data or systems.
Why is penetration testing important?
While there is no way to avoid these threats completely, reducing the threat footprint of your business will go a long way towards protecting your sensitive data. This is why penetration testing is important. Pen Testing will let you determine whether or not a particular Web application is suitable for your organization, and whether or not it is protecting your data appropriate ly.
Why do businesses use penetration testing?
A Penetration Test is typically conducted in order to detect weak areas in a Web application and determine whether or not they present a risk to the security of your company.
Why do we do web vulnerability assessments?
The primary purpose of the primary goal of a Web vulnerability assessment is to identify security weaknesses on the client side. Common issues that are typically addressed during these assessments include memory holes, cross-site scripting vulnerabilities, SQL injection vulnerabilities, and application security issues. It is very common for companies to use client side testing as a way of discovering the most severe of security flaws. However, using client side testing is not enough to isolate the flaws that may exist in your Web application. For these reasons, comprehensive and effective testing is necessary to confirm the existence and severity of Web vulnerabilities.
What is penetration testing?
Penetration testing is a method of simulating a cyberattack to identify weaknesses in your computer system, network or web applications. It’s known as an ethical hack, as it’s used to improve your cybersecurity.
Why is penetration testing important?
A penetration testing process will enable your business to test where new vulnerabilities occur as your business grows and evolves.
What is a pen test?
A pen test enables companies to see where their vulnerabilities occur and how these weaknesses can be exploited – whether this be through exposing sensitive information , the network or your applications. This test is carried out in a safe environment where the pen tester is working with your company rather than having malicious motivations. It’s a bit like carrying a test of your business continuity plan – you think you have everything in place but even the best plan can be shown to have a gaping hole when a question or challenge that no one has ever considered before, is asked.
Why do companies use pen tests?
Pen tests enable your company to see how your IT team reacts to an attack and their capabilities before a true hacker attacks your system. Identifying skillset gaps in a simulated cyberattack enables your cybersecurity to seek additional training and learn.
What industries require pen testing?
Many industries include penetration testing as part of their compliance legislation, such as healthcare, banking and service providers . Some common regulations that require pen tests to be compliant include
Who should approve cyber security tests?
There are overwhelming benefits in performing regular tests of your cyber defences, but this is task for a professional! Tests should be planned and approved by a senior leader in your organisation who should have board responsibility for your data security.
Are penetration tests worth it for SMEs?
In short, yes! All businesses should be organising pen tests and SMEs are no exception.
What is a penetration test?
A penetration test is an attack on a computer system, network or web application with the purpose of finding security vulnerabilities so preventative measures can be taken.
Why is Pen Testing Important?
Periodic pen testing is a common requirement for compliance obligations, and for good reason. By replicating cybercriminal methods , organizations can find and fix flaws likely to be exploited. That said, be careful. The value in a pentest is diminished when not well executed. Low-cost options aimed at “checking the boxes” for compliance purposes are easy to find, but often leave a company both vulnerable and blind to critical weaknesses.
What is the purpose of penetration testing?
The main objective of a penetration test is to identify security weaknesses in a network, machine, or piece of software. Once that is clear, the vulnerabilities can be eliminated, or the weaknesses can be reduced before hostile parties discover them and exploit them.
Why is penetration testing important?
Acting on the results of a test will help to minimize the risk of penalties or lost business due to non-compliance.
Why Perform Penetration Testing?
A pen test is generally performed to find vulnerabilities and fix them before an attacker does. Sometimes, the IT department is aware of the reported vulnerabilities but still needs an external expert to officially report them so that the management is sure of the vulnerabilities and can fix them properly. Having a second set of eyes to corroborate all the vulnerabilities is always a good security practice. Let’s find out the reasons why performing pen testing is important.
Why is penetration testing important?
1. Meeting compliance: There has been a mandate in the payment card industry to follow the PCI-DSS regulations for an annual and ongoing penetration testing. A pen-test allows the enterprises to mitigate the real risks associated with the network. 2.
What separates a penetration tester from an attacker?
The only thing that separates a penetration tester from an attacker is permission . A pen tester will always have consent from the owner of the computing resources that are being tested and will be accountable to provide a report.
What is testing xperts?
TestingXperts holds a rich expertise in security testing and is catering to diverse business needs. TestingXperts have been serving clients across different industry verticals for more than a decade now. Our web application penetration testing services exposes vulnerabilities in applications and minimizes the risks of the application. Moreover, our efficient pen-testers ensure that the software code of the application is benchmarked for increased quality assurance.
Why is it important to keep notes when doing pen tests?
It is important for the pen-testers to keep comprehensive notes about how the tests were performed so that the results can be validated and if there are any issues that are uncovered can be resolved.
What is a tester provided with?
In addition to this, the testers will be provided with partial knowledge or access to the web application and internal network.
Why do security teams use penetration reports?
3. To verify secure configurations: If the security team of an organization is doing a good job, and are confident of their actions and the final results, the penetration reports verify them. Having an outside entity acts as a confirming agent of whether the security of the system provides a view that is lacking the internal preferences. An outside entity can also measure the team’s efficiency as security operators. It helps in identifying the gaps in the system.