
Symmetric encryption algorithms are used (combined with an encryption key) to do two main things:
- Encrypt. Convert readable text (plaintext) into unreadable, encrypted text (ciphertext).
- Decrypt. Convert the ciphertext back to plaintext.
How many keys is required for symmetric key encryption?
The encryption is called “symmetric” because it uses a single key for both encryption and decryption. In comparison, asymmetric key encryption, also called public key cryptography, uses two separate keys to encrypt and decrypt messages. A key is a random string of binary digits or bits created specifically to scramble and unscramble data.
Which encryption algorithm is the strongest?
What is the Strongest Encryption Today?
- RSA. The RSA or Rivest-Shamir-Adleman encryption algorithm is one of the most powerful forms of encryption in the world.
- AES. The Advanced Encryption Standard is actually commonly paired with RSA as its symmetric partner. ...
- The Future Champions. ...
- Unbreakable. ...
Does a PKI use symmetric or asymmetric encryption?
PKI merges the use of both asymmetric and symmetric encryption. Both symmetric and asymmetric encryption have their own strengths and best use case scenarios, which is what makes the combination of both so powerful in Public Key Infrastructure .
What are some examples of symmetric and asymmetric encryption?
What are some examples of symmetric and asymmetric encryption? Symmetric encryption uses a single shared key for both encryption and decryption. Asymmetric encryption uses two keys – public key and private key. Usually the data is encrypted using the public key and the cipher text is decrypted using the private key.

What is symmetric encryption used for?
Here, asymmetric encryption is used to establish the encrypted communication between the two users, and symmetric encryption is used for communication duration.
What are the principles of symmetric encryption?
Symmetric encryption is a type of encryption where only one key (a secret key) is used to both encrypt and decrypt electronic data. The entities communicating via symmetric encryption must exchange the key so that it can be used in the decryption process.
What are the two principal requirements for the secure use of symmetric encryption?
What are the two principal requirements for the secure use of symmetric encryption? (1) a strong encryption algorithm; (2) Sender and receiver must have obtained copies of the secret key in a secure fashion and must keep the key secure.
What is the main advantage of symmetric encryption?
Advantages and Disadvantages of Symmetric Key Encryption The benefit of symmetric key encryption is that it is fast and convenient to set up. Plus, this method is simple and easy to understand, so everyone can easily master it. The single disadvantage: the receiver must get the secret key from the sender.
Which two items are used in a symmetric encryption?
To put this in the simplest terms possible, symmetric encryption is a type of encryption that uses the same key to encrypt and decrypt data. Both the sender and the recipient have identical copies of the key, which they keep secret and don't share with anyone.
What are the 5 elements of a symmetric encryption scheme?
There are five main components of a symmetric encryption system: plaintext, encryption algorithm, secret key, ciphertext, and the decryption algorithm.
What are the 2 basic functions used in encryption algorithms?
Substitution and transposition are the two basic functions used in encryption algorithms.
Does symmetric encryption uses public key?
Symmetric encryption uses a private key to encrypt and decrypt an encrypted email. Asymmetric encryption uses the public key of the recipient to encrypt the message. Then if the recipient wants to decrypt the message the recipient will have to use his/her private key to decrypt.
What are the key principles of security?
The Principles of Security can be classified as follows:Confidentiality: The degree of confidentiality determines the secrecy of the information. ... Authentication: Authentication is the mechanism to identify the user or system or the entity. ... Integrity: ... Non-Repudiation: ... Access control: ... Availability:
What is the main strength and weakness of symmetric encryption?
Symmetric encryption is also called “secret key” encryption because the key must be kept secret from third parties. Strengths of this method include speed and cryptographic strength per bit of key; however, the major weakness is that the key must be securely shared before two parties may communicate securely.
What are the benefits of encryption?
Five business benefits of using data encryptionTotal data protection. A comprehensive encryption solution offers enterprises complete peace of mind as it safeguards data whether in transit or at rest. ... Keeping compliant. ... Secure data transfer. ... Maintaining data integrity. ... Protection over multiple devices.
Why is symmetric encryption faster?
Symmetric cryptography is faster to run (in terms of both encryption and decryption) because the keys used are much shorter than they are in asymmetric cryptography. Additionally, the fact that only one key gets used (versus two for asymmetric cryptography) also makes the entire process faster.
What is an example of symmetric encryption?
Blowfish, AES, RC4, DES, RC5, and RC6 are examples of symmetric encryption. The most widely used symmetric algorithm is AES-128, AES-192, and AES-256. The main disadvantage of the symmetric key encryption is that all parties involved have to exchange the key used to encrypt the data before they can decrypt it.
Which of the following are the types of symmetric encryption?
Symmetric Algorithm List: The 3 Most Common Symmetric Algorithm TypesData Encryption Standard (DES) First up on our list is the data encryption standard. ... Triple Data Encryption Algorithm (TDEA) ... Advanced Encryption Standard (AES)
Which of the following statements is correct about the symmetric encryption?
Answer 2 is correct. As there is only one key in the symmetrical encryption, this must be known by both sender and recipient and this key is sufficent to decrypt the secret message.
What is the difference between symmetric and asymmetric encryption?
The basic difference between these two types of encryption is that symmetric encryption uses one key for both encryption and decryption, and the asymmetric encryption uses public key for encryption and a private key for decryption.
How Does Symmetric Encryption Work?
To understand how symmetric cryptography works, you need to know what the components are that are involved in the process:
How does HTTPS work?
The way that HTTPS works is that we use asymmetric encryption to first authenticate the website server and to exchange symmetric session keys. This is part of a process known as the TLS handshake — of which there are three versions (TLS 1.0, TLS 1.2 and TLS 1.3).
Why is symmetric encryption faster than asymmetric encryption?
The reason for the change to symmetric encryption is that it’s faster and less resource-intensive than asymmetric encryption when you’re encrypting massive quantities of data.
What type of encryption is used to authenticate a key?
There’s also another type of encryption that’s close in name but is different in terms of what it does: asymmetric encryption. We mentioned it earlier, but just know that asymmetric encryption is what makes it possible to authenticate and exchange symmetric keys via public channels (such as the internet).
What is the key used to send a message?
The sender uses an encryption key (usually a string of letters and numbers) to encrypt their message. The encrypted message, called ciphertext, looks like scrambled letters and can’t be read by anyone along the way. The recipient uses a decryption key to transform the ciphertext back into readable text.
What is a DES key?
Data Encryption Standard (DES) — DES is a type of block cipher that encrypts data in 64-bit blocks and using a single key that is one of three sizes (64-bit, 128-bit and 192-bit keys). However, one of every 8 bits is a parity bit, meaning that a single-length key that’s 64 bits is really like using a 56-bit key. Although DES is one of the earliest symmetric encryption algorithms, it’s viewed as insecure and has been deprecated.
What is AES 128 encryption?
The recipient uses a decryption key to transform the ciphertext back into readable text. This is an example of using AES 128 encryption. In the example above, we used the same key for encryption and decryption, which means this is symmetric encryption.
What is stream data encryption?
Stream data encryption involves the use of an additive cipher whereby each bit of information is changed using the corresponding bit of a pseudorandom secret keystream (a sequence of numbers generated on the basis of a key) that has the same length as the encrypted message.
Why do we use symmetric encryption?
Many modern services use symmetric encryption to exchange data, often in combination with asymmetric encryption. For example, instant messengers use such ciphers to secure correspondence (with the symmetric encryption key typically being delivered in asymmetrically encrypted form), and video services do likewise to secure streams of audio and video. In the Transport Layer Security ( TLS) protocol, symmetric encryption ensures the confidentiality of transmitted data.
What are the two types of encryption?
Symmetric encryption algorithms are divided into two types by their operating principle: block ciphers. stream ciphers. Block algorithms encrypt data in fixed-length blocks (64, 128, or another number of bits, depending on the algorithm).
Why do we need the same key for the algorithm to work?
Because the message sender and recipient need the same key for the algorithm to work, it has to be transmitted somehow. And if that is done over an unprotected channel, it can be intercepted. In practice, many systems solve this problem by using an asymmetric algorithm to encrypt the key.
What happens when an algorithm replaces letters with numbers?
For example, if the algorithm replaces letters with numbers, the sender of the message and its recipient must have the same mapping table. The former encrypts the message with it, the latter decrypts.
Which is faster, symmetric or asymmetric?
Symmetric algorithms are less resource-heavy and faster than their asymmetric counterparts. Most symmetric ciphers are presumed to be resistant to attacks using quantum computers, which in theory pose a threat to asymmetric algorithms.
Is symmetrical algorithm reliable?
As such, modern symmetric algorithms are considered reliable only if they meet the following requirements: The output data does not repeat statistical patterns in the source data (per the example above, the most frequent symbols in the source and in the cipher should not coincide).
How Does Symmetric Key Encryption Work?
Modern computers don’t store data as alphabetic letters , instead, they keep everything as bits. Every character you type can be represented by an ASCII code, which is a combination of 8 bits.
What Are the Categories of Symmetric Key Encryption?
Symmetric key ciphers are broken down into two main categories – block ciphers and stream ciphers. The two ciphers have different data encryption processes and operating environments.
What Are Symmetric Key Encryption’s Advantages?
Security: Symmetric key encryption is essentially unbreakable and requires users to keep track of only one key. In fact, the US government encrypts classified information with this method — specifically, the aforementioned AES implementation The most secure AES cipher has a 256-bit key size. Even with supercomputers, an attacker trying to brute force through the encryption will need millions of years to crack it.
How is a keystream generated?
The keystream is generated by providing the encryption key and a seed to an internal algorithm (or keystream generator) which is an internal software . The seed is also called a nonce, which is a unique and randomly generated number that the cipher will use only once.
How to send encrypted text?
To send an encrypted message, a user would need to take their plaintext message and symmetric key as the input for the XOR. After comparing the two input bits via the XOR, the user will obtain the ciphertext as the output bit. Recipients can decrypt the message by reversing the encryption process. For decryption, recipients take the ciphertext and symmetric key as input for the XOR, and generate the original plaintext.
How does a sender use a cipher?
The sender uses this key to encrypt their messages through an encryption algorithm, called a cipher, which converts plaintext to ciphertext. The designated recipients then use the same key to decrypt the messages by converting the ciphertext back to plaintext.
What is symmetric encryption?
Symmetric key encryption, also called private key cryptography, is an encryption method where only one key is used to encrypt and decrypt messages. This method is commonly used in banking and data storage applications to prevent fraudulent charges and identity theft as well as protect stored data.
How does WhatsApp work?
The client who wants to initiate a session, retrieves from the Whatsapp server the public keys for the recipient. Using these keys, the initiator encrypts the first message and sends it to the recipient. This message contains the parameters for establishing a symmetric session key. The recipient uses his own private key to decrypt the message. “Once a session has been established, clients exchange messages that are protected with a Message Key using AES256 in CBC mode for encryption and HMAC-SHA256 for authentication.” The encrypted session needs to be re-created only when the device is changed or when the application software is re-installed.
What is symmetric encryption?
In symmetric encryption, the sender and receiver use a separate instance of the same key to encrypt and decrypt messages. Symmetric encryption heavily relies on the fact that the keys must be kept secret. Distributing the key in a secure way is one of the primary challenges of symmetric encryption, which is known as the “ key distribution problem. ” The key that is the vital component in symmetric cryptography and we cannot afford to lose it or misplace it. If the individual keys are misplaced, the message can be decrypted by malicious actors.
What is the purpose of cryptographic algorithms?
Cryptosystems use a set of procedures known as cryptographic algorithms, or ciphers, to encrypt plain text messages into cipher text or encrypted messages or decrypt cipher text messages into plain text. Auguste Kerckhoff in 1883 stated that encryption algorithms should be made public and the “keys” be kept secret, which is Kerckhoff’s Principle.
Why is symmetric encryption not suitable for long sessions?
It is not suitable for long sessions because of the processing power it takes to keep it going. Use Cases of Symmetric Encryption. Banking Sector. Due to the better performance and faster speed of symmetric encryption, symmetric cryptography is typically used for bulk encryption of large amounts of data.
How does public key encryption work?
Also known as asymmetric encryption, public key cryptography is used as a method of assuring the confidentiality, authenticity and non-repudiation of electronic communications and data storage . Public-key encryption uses two different keys at once, a combination of a private key and a public key. The private key must remain confidential to its respective owner, while the public key is made available to everyone via a publicly accessible repository or directory. To decode an encrypted message, a computer must use the public key, provided by the originating computer, and its own private key. Although a message sent from one computer to another won't be secure since the public key used for encryption is published and available to anyone, anyone who picks it up can't read it without the private key.
What are the disadvantages of symmetric encryption?
The most important disadvantages of symmetric encryption are the key distribution problem and the key management problem. When the number of connected users grows, so does the number of required keys. Management of an increasing number of secret keys becomes a “key management problem.”. Further, symmetric cryptography ensures only ...
Why won't symmetric encryption work?
When connecting to a website on the public internet it becomes more complicated and symmetric encryption, by itself, won’t work because you don’t control the other end of the connection. How do you share a secret key with each other without the risk of someone on the internet intercepting it in the middle? In November 1976, a paper published in the journal IEEE Transactions on Information Theory by Diffie and Hellman, titled " New Directions in Cryptography ," addressed this problem and offered up a solution: public-key encryption.
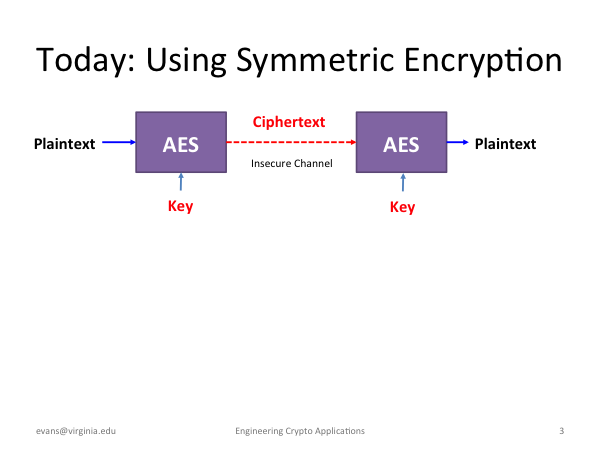
How Symmetric Algorithms Work
Types of Symmetric Encryption Algorithms
- Symmetric encryption algorithms are divided into two types by their operating principle: 1. block ciphers 2. stream ciphers Block algorithms encrypt data in fixed-length blocks (64, 128, or another number of bits, depending on the algorithm). If the whole message or its final part is smaller than the block size, the algorithm adds its own symbols, known aspadding. Current block algorithms i…
Pros and Cons of Symmetric Encryption
- Symmetric algorithms are less resource-heavy and faster than their asymmetric counterparts. Most symmetric ciphers are presumed to be resistant to attacks using quantum computers, which in theory pose a threat to asymmetric algorithms. The Achilles heel of symmetric encryption is the key exchange. Because the message sender and recipient need the same key for the algorithm t…
Scope of Application For Symmetric Encryption
- Many modern services use symmetric encryption to exchange data, often in combination with asymmetric encryption. For example, instant messengers use such ciphers to secure correspondence (with the symmetric encryption key typically being delivered in asymmetrically encrypted form), and video services do likewise to secure streams of audio and video...