The Identity Provider (IdP) generates a private key and a public key. It signs the assertion with the private key. The public key is shared with the Service Provider (SP) which uses it to verify the SAML response and then log the user in.
How do I set up SAML SSO with Google?
To set up SSO using the SAML instance where Google is the service provider (SP), you need to generate a set of public and private keys and an X.509 certificate that contains the public key. The public keys and certificates must be generated with either the RSA or DSA algorithm and registered with Google.
How do I create public and private keys for SSO?
To create public and private key pairs, you can use OpenSSL, the Certificate Creation tool and the Pvk2pfx tool in .NET, Keytool in Java, or Java Cryptography Architecture. For details, see Generate Keys and Certificates for SSO. Upload your verification certificate.
What is the primary key used for SAML signatures?
However, only the primary key is used by Anypoint Platform to sign SAML 2.0 AuthnRequests and SLO requests; the primary key must be configured in your IdP to validate the signatures. If you are migrating from the default Anypoint Platform SSO certificate to a new certificate, you must update the Assertion Consumer Service (ACS) URL in your IdP.
How to set up single sign on (SSO)?
Set up SSO via a third party Identity provider SAML key and verification certificate Next: Signing in with SSO Create and upload the key and verification certificate
Which of the following will store the public and private keys in SAML?
Assuming SAML signing has been implemented, the keypair (private/public key) for SAML encryption and signing is stored in the AM keystore, which differs depending on which version you are using. AM uses a JCEKS keystore as its default keystore. The default location is: /path/to/am/keystore.
What is the function of the signing private key?
Using the private key. For digital signatures, the owner of the key pair uses their private key to encrypt the signature. In this way, anyone with access to the public key can decrypt the signature and verify that it was signed by the private key owner.
How does SAML encryption work?
In summary, when encrypting SAML v2. 0 messages, the sender uses the receiver's public key (exposed in the receiver's metadata) to encrypt the request. The receiver decrypts it with its private key. As with signing, providers also expose in their metadata the algorithms that they can use to encrypt assertion content.
What are the role of public key and private key?
Private key is used for both encrypting and decrypting the sensitive data. It is shared between the sender and receiver of encrypted data. Public key is used only for the purpose of encrypting the data. The private key mechanism is faster.
What is public key and private key with example?
Public and private keys: an example Bob wants to send Alice an encrypted email. To do this, Bob takes Alice's public key and encrypts his message to her. Then, when Alice receives the message, she takes the private key that is known only to her in order to decrypt the message from Bob.
What encryption does SAML use?
The IdP encrypts the SAML assertion with a random symmetric key which in turn is encrypted with the SP's public key. The SP uses its private key to decrypt the symmetric key which in turn is used to decrypt the SAML assertion. This ensures that only the SP can decrypt the SAML assertion.
How SAML works for SSO?
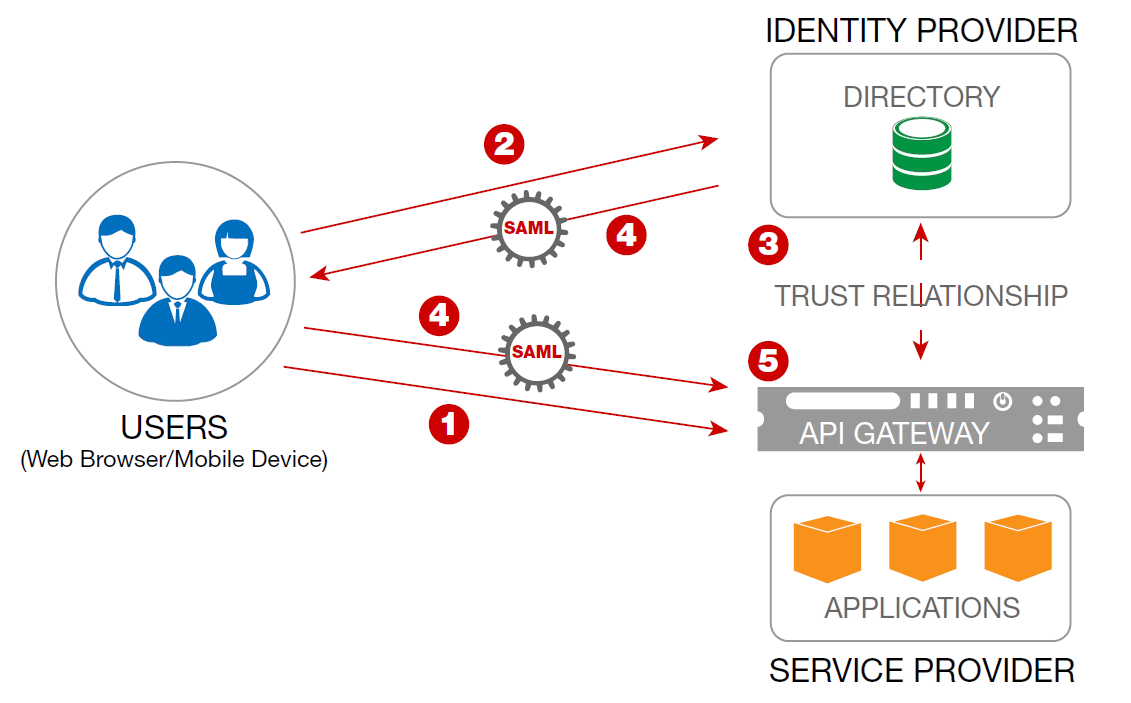
SAML SSO works by transferring the user's identity from one place (the identity provider) to another (the service provider). This is done through an exchange of digitally signed XML documents. Consider the following scenario: A user is logged into a system that acts as an identity provider.
Should SAML be encrypted?
If the SAML response contains claims and assertions that contain private data, and the receiver of the response will be holding onto the SAML assertion for an indefinite period or passing the SAML assertions through intermediate parties you do not trust, then yes, the SAML assertions should be encrypted and the ...
What is private key in digital signature?
The sender's private key encrypts the data -- this is the digital signature -- and the receiver uses the public key to decrypt it and verify it matches the attachment. The public key and private key in digital signatures are mathematically related but cannot be generated from each other.
What is the use of private key in SSL?
Anyone can have access to your public key, and it verifies that the SSL certificate is authentic. A private key is a block of encoded text which, together with the certificate, verifies the secure connection between two machines. It must not be publicly accessed, and it shouldn't be sent to the CA.
What is the use of private key in certificate?
The private key is a separate file that's used in the encryption/decryption of data sent between your server and the connecting clients. A private key is created by you — the certificate owner — when you request your certificate with a Certificate Signing Request (CSR).
What is the meaning of private key Mcq?
Explanation: Private key algorithm is used for encryption of messages and public key algorithm is used for encryption of session keys. 10.
How to configure token encryption?
From the Azure portal, go to Azure Active Directory > App registrations. Select All apps from the dropdown to show all apps, and then select the enterprise application that you want to configure. In the application's page, select Manifest to edit the application manifest.
Where are encryption certificates stored?
Encryption certificates are stored on the application object in Azure AD with an encrypt usage tag. You can configure multiple encryption certificates and the one that's active for encrypting tokens is identified by the tokenEncryptionKeyID attribute.
Does Azure AD require tokens?
Azure AD requires token request/response exchanges to take place over encrypted HTTPS/TLS channels so that communications between the IDP, browser, and application take place over encrypted links. Consider the value of token encryption for your situation compared with the overhead of managing additional certificates.
What is SAML in security?
Security Assertion Markup Language, or SAML, is a standardized way to tell external applications and services that a user is who they say they are. SAML makes single sign-on (SSO) technology possible by providing a way to authenticate a user once and then communicate that authentication to multiple applications.
What is SAML 2.0?
SAML 2.0 is the modern version of SAML , and it has been in use since 2005. SAML 2.0 combined several versions of SAML that had previously been in use. Many systems support earlier versions, such as SAML 1.1, for backwards compatibility, but SAML 2.0 is the modern standard.
What is single sign-on (SSO)?
Single sign-on (SSO) is a way for users to be authenticated for multiple applications and services at once. With SSO, a user signs in at a single login screen and can then use a number of apps. Users do not need to confirm their identity with every single service they use.
What is a SAML assertion?
A SAML assertion is the message that tells a service provider that a user is signed in. SAML assertions contain all the information necessary for a service provider to confirm user identity, including the source of the assertion, the time it was issued, and the conditions that make the assertion valid.
What is an identity provider?
Identity provider: An identity provider (IdP) is a cloud software service that stores and confirms user identity, typically through a login process. Essentially, an IdP's role is to say, "I know this person, and here is what they are allowed to do." An SSO system may in fact be separate from the IdP, but in those cases the SSO essentially acts as a representative for the IdP, so for all intents and purposes they are the same in a SAML workflow.
What is SAML interoperability?
This is called "interoperability": the ability for different machines to interact with each other, despite their differing technical specifications. SAML is an interoperable standard — it is a widely accepted way to communicate a user's identity to cloud service providers.
What is authentication in a login?
Authentication refers to a user's identity: who they are and whether their identity has been confirmed by a login process.
What is SAML single sign on?
SAML single sign-on uses cryptographically signed tokens known as Assertions. They are signed by your Identity Provider system (Ping Federate or Active Directory Federation Services, for example). Glance checks the signature to make sure the token is valid before accepting it. Your Identity Provider uses the secret key from an internal encryption certificate to sign Assertions. When you provision SAML at Glance, you give our system the public key from that certificate.
What is the API key for Glance?
Each Glance customer account has an API key. It is used to generate LoginKeys to grant access to Glance. You may change your API key. If you do, Glance rejects future LoginKeys generated with the old API Key.
