The SQL Server Audit enables you to audit the following:
- 1. Object access attempts, such as connection attempts and logins and database management activities.
- 2. Data modification attempts.
- 3. Administrators and users who connect to the Database Engine.
- 4. Database object access attempts.
- 5. User-initiated activities such as creating logins and databases.
How to start and set up SQL Server audit?
- To create a server audit specification, expand the Security folder in Object Explorer
- Right-click Server Audit Specifications
- Select New Server Audit Specification
How to analyze and read SQL Server audit information?
- The SQL Server Service Account must have both Read and Write permission.
- Audit Administrators typically require Read and Write permission. ...
- Audit Readers that are authorized to read audit files must have Read permission.
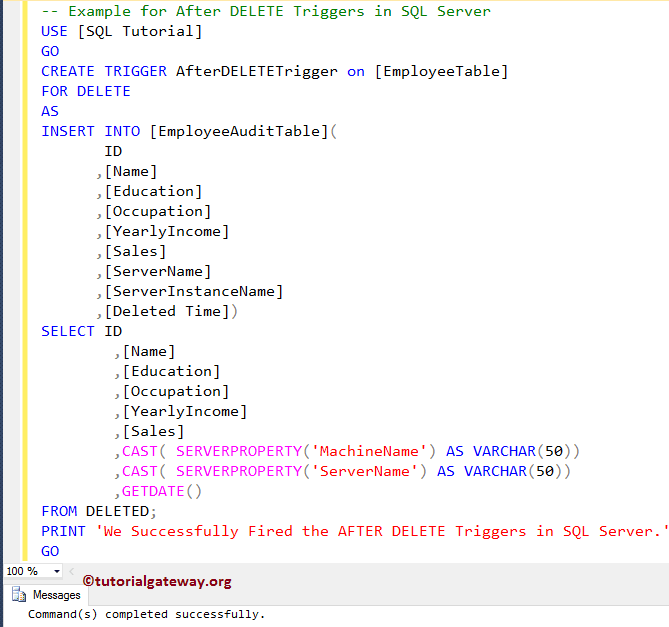
How to create a SQL Server audit trigger?
In this syntax:
- The schema_name is the name of the schema to which the new trigger belongs. ...
- The trigger_name is the user-defined name for the new trigger.
- The table_name is the table to which the trigger applies.
- The event is listed in the AFTER clause. ...
How to audit data changes in SQL Server?
- Start ApexSQL Audit
- Click the ‘Add server’ in the Configure tab to select a server for audit
- Click the ‘Add database’ button to select a database for auditing, and select server or database operations you want to audit.
See more

What is SQL Server Audit?
In environments where SQL Server is used, auditing is a basic requirement for SQL Server security, as well as for compliance standards including ISO27001, PCI DSS, BASEL3, GDPR, IG, HIPAA standards.
What is auditing in SQL Server?
When managing auditing in SQL Server, the basic element is an audit specification object. This object defines the server and database events recorded in the audit report. When defining the objects to be audited, you also define what to write to the SQL audit log file. Audit logs can be written to your own log file, or directly to the Windows Security event log or Windows Application event log.
What is universal audit?
With Universal Audit, data and security teams can use a single tool to continuously monitor data access completely, uniformly and coherently for SQL server and other databases. Universal Audit classifies sensitive data as it’s being accessed, retains an audit of all data access for an infinite amount of time and makes answering questions such as “Who is accessing PII in our SQL server?” or “Who is modifying PHI?” immediate, simple, and thorough.
Why is audit log important?
The SQL audit log is important because it can be used to assess the security of SQL Server databases, as well as to provide you with the information needed for specific compliance standards. By using a central log management system to collect and normalize log data and audit logs, you can gain important insights to ensure your SQL Server instances are secure and do not violate your compliance obligations.
Where are audit events located?
Both audit events and audit action groups are located at the SQL database level. You can create one database audit specification per SQL Server database per audit. Once you send actions to the audit, it records them in a target location.
What are the most important events to track in an audit?
One of the most important events you should track in auditing is failed login attempts, such as username/password input errors and password expiration , which may indicate malicious access attempts. Always store this information, and ensure alerts are raised to the security team.
What is audit destination?
To define an audit, you need to specify an audit destination, which is essentially a location for the output of the results. An audit is first created in a disabled state. This means it does not automatically audit actions. Once an audit is enabled, the audit destination can receive data from the audit.
What is SQL Server audit?
SQL Server auditing requires two objects: a server audit, and either a server or a database audit specification. It is best to have one server audit for the server audit specification, and a second audit that contains all of the database audit specifications for that server. This gives the DBA an extra level of control over auditing, ...
What is database audit?
A Database Audit Specification can be used to track any DDL statement issued against the database. This gives you a record of who created, altered or dropped any object within the database.
Why audit anything? Who needs it?
Why do we need to be "big brother" over the data? Because we are the Guardians of that Data. Think of SQL Server Auditing as the highly intelligent genetically-modified raccoon that keeps an eye on what is happening. SQL Server audit specifications can be set up at the server and the database level to track the activities in which you may be interested: Creating, altering and dropping logins, database users, DBCC execution, even data operations on certain tables.
What is SQL Server auditing event ID?
First of all you need to know what to look for. All SQL server auditing events are stored with the event ID of 33205, making it extremely easy to filter away the millions of other security log entries that accumulate on any well configured server.
How many characters are in SQL Server audit log?
Beware! SQL server audit log notes are big! The text associated with them can easily run over 1000 characters for a single event. Choosing an appropriate length of time to preserve event information will become extremely important as time goes on. Log forwarders, such as Splunk, usually charge by the number of bytes of data that they store. Archiving and purging becomes an issue.
How to add a user to SQL Server?
On the Local Security Setting tab, click Add User or Group. In the Select Users, Computers, or Groups dialog box, either type the name of the domain account on which SQL Server runs, and then click OK, or click Advanced and search for the account. Click OK. Close the Security Policy tool. Restart SQL Server to enable this setting.
Is there a procedure for SQL Server 2008?
There are additional procedures for SQL Server 2008. Jonathan Kehayias has written an excellent article here to help you with prerequisites for that version of SQL Server. Since the 2008 version is getting pretty old, I figured that it would be better to leave the steps out of this article to save space.
Why choose Astra for SQL Server Audit?
Today, most businesses require cyber security solutions like SQL server audit to protect their confidential data. The cyber security market is growing in terms of both opportunities and challenges. This is why Astra, a leading cyber security solutions company, offers comprehensive cyber security services.
Why is securing SQL Servers important?
For most web users, the idea of data security is often limited to the protection of sensitive financial information, like credit card numbers. It’s easy to see why when data breaches are often in the news. But the truth is that SQL Server security is vulnerable at many levels, and the problem goes beyond sensitive customer information of customers such as credit card data, etc.
What is SQL Server?
SQL Server is widely used for storing and managing data. It can handle large amounts of data, and it is easy to use. It has several components, including the relational database management system (RDBMS), the SQL Server Management Studio, and the SQL Server Agent.
What is SQLi, and How do you fix that?
A SQL injection is an attack on a back-end database that allows an attacker to interfere with the queries the application is making. This is performed by inserting specially-crafted input into an entry field on the website that connects to the database. If the application is not configured to verify that the input is valid, the attacker can execute code on the database server.
How to set up the SQL Server Audit feature?
To be able to create, modify, delete, and enable server audit objects, a user must be granted the ALTER ANY SERVER AUDIT or CONTROL SERVER permission on the SQL Server instance
What permissions are needed to configure database audit specifications?
To be able to configure database audit specifications, a user must be granted the ALTER ANY DATABASE AUDIT, ALTER, or CONTROL permissions on the audited database (AdventureWorks in this example)
What is auditpol.exe?
In Windows Vista and Windows Server 2008, use the audit policy tool (auditpol.exe). The audit policy program exposes a variety of sub-policies settings in the audit object access category. To allow SQL Server to audit object access, configure the application generated setting.
What is audit destination?
An audit destination can be a file (a *.sqlaudit file), security log, or application log. For writing into a file and application log, no specific permissions are needed. To be able to write into a security log, the following requirements must be met. Otherwise, there will be an error and no events will be recorded
What is queue delay?
Queue delay – sets the number of milliseconds before the audit information is processed into a target file. When set to 0, the process is synchronous
Can only one server audit exist per audit object?
Note that only one server audit specification can exist per an audit object. If you try to create the style=”margin:0px auto;display:block” second server audit specification for the same audit, you’ll get the following error message:
Can SQL Server audit be done?
Configuring and enabling the SQL Server Audit feature and its components can be done via T-SQL and SQL Server Management Studio options. The auditing is more granular than with SQL Server Change Tracking and Change Data Capture. The events are divided into groups and only a whole group of events can be audited. In the next part of this series, we will show how to read the audited information
Which editions support database level audit specifications?
Keep in mind that only Enterprise / Developer editions support database level audit specifications.
What is audit_change_group?
The AUDIT_CHANGE_GROUP event is raised to alert on creation, modification or deletion of audit events. So in this case there will be two audits – one that audits the security events in the system and the other will be auditing if admins are tampering with the first audit.
What is the hardest part of security auditing?
The hardest part of Security Auditing is to define what should be audited and how. The security breaches around a SQL Server instances may occur in several areas: from SSIS packages saved on disk, to system users and administrators who can read and even modify data. There a lot of different attack vectors to monitor. A good place to start is to determine the legislative requirements for your installation, which will depend on the nature of the data. Generally, there is a requirement to track and log events that occur on the Database Engine in sufficient detail to aid a forensic analysis of any data-breach that occurs.
How many actions are audited?
There are over 500 actions that are audited, and we can see how many actions are triggered in our Audit by running the following query:
Where is SQL Server data stored?
Finally, another challenge is to choose a way to deal with the large volume of data generated by the security auditing. The data can be stored in logs (SQL Server instance logs, Operating system logs), it can also be stored in log files on disk. Ideally, the data can be stored in ring buffers and consumed by external components and so on, but all this needs to be planned around the audit retention interval that is required.
Does HKLM need to restart SQL Server?
Of course, a SQL Server instance restart is needed.
Is SQL Audit available in SQL Server?
The work of setting up an audit log has been made much easier by Microsoft’s introduction of SQL Audit functionality. It has been available in SQL Server since SQL2008 and it was slightly improved in SQL2012. In this article first show how to set up the current security context, and then we’ll show you how to set up SQL Audit and apply it to all the databases in an instance.
Why Audit anything? Who Needs It?
What Does Auditing Give You?
- You can receive output as a flat file. This may have advantages for some. However, the log file can only be read through Management Studio or with a built-in function named sys.fn_get_audit_file. Therefore, it is limited in its usefulness. I prefer to have the audit information placed into the Windows Security Event Log. These logs may be written to if SQL Server has the …
How to Set Up SQL Server Auditing
- SQL Server auditing requires two objects: a server audit, and either a server or a database audit specification. It is best to have one server audit for the server audit specification, and a second audit that contains all of the database audit specifications for that server. This gives the DBA an extra level of control over auditing, since the DBA can deactivate all database auditing by deactiv…
Understanding The Audit Output
- First of all you need to know what to look for. All SQL server auditing events are stored with the event ID of 33205, making it extremely easy to filter away the millions of other security log entries that accumulate on any well configured server. Beware! Ensure that the systems administrator has increased the size of your security log to accumulate an appropriate number of entries so th…
Utilizing The Audit
- Picture this: The development team is hard at work on a critical project. All of a sudden the application crashes in the middle of a test. The report is that a stored procedure has gone missing. What happened? The developers pull out the problem resolution flowchart where every path ends at "Blame the Database and Call the DBAs." And you, the trusty DBA, are armed. You s…
Conclusion
- This article is intended to be a primer to explain the power and basic implementation of SQL Server auditing. With a small amount of applied effort, you can install a worthwhile and effective tool to help you keep tabs on your servers and their databases.