What is WannaCry ransomware?
What Is WannaCry? Infecting more than 230,000 Windows PCs in 150 countries in one day — many of them belonging to government agencies and hospitals — the ransomware known as WannaCry shocked the world with its widespread attack. Avast has blocked more than 176 million WannaCry ransomware attacks and counting.
What is the WannaCry virus and what did it do?
WannaCry hit an estimated 230,000 computers. The malware affected the operations of hospitals, emergency services, petrol stations, and even factories. Some estimates put the financial cost of the attack in the billions. Who created WannaCry?
Why is WannaCry such a significant cyber incident?
Small businesses are also targets of ransomware and can find it harder to survive as they usually have fewer resources than larger companies to recover. While the global WannaCry attack occured in 2017, many other types of ransomware have emerged in the years since. Let's take a look at WannaCry and why it was such a significant cyber incident.
Is WannaCry a phishing worm?
"WannaCry: the ransomware worm that didn't arrive on a phishing hook". Naked Security. Sophos. Archived from the original on 11 July 2017. Retrieved 18 May 2017. ^ Newman, Lily Hay (12 May 2017). "The Ransomware Meltdown Experts Warned About Is Here". Wired. Archived from the original on 19 May 2017.
See more

What does WannaCry virus do?
WannaCry is a ransomware worm that spread rapidly through across a number of computer networks in May of 2017. After infecting a Windows computer, it encrypts files on the PC's hard drive, making them impossible for users to access, then demands a ransom payment in bitcoin in order to decrypt them.
Does WannaCry still exist?
While the majority of the damage occurred in the weeks after May 12, 2017, WannaCry ransomware attacks actually increased 53% from January 2021 to March 2021. While researching my in-depth article WannaCry: How the Widespread Ransomware Changed Cybersecurity, I learned that WannaCry attacks are still found today.
Who made WannaCry virus?
When he was just 22, Marcus Hutchins rose to fame by single-handedly stopping the spread of WannaCry, a ransomware attack that hit hundreds of thousands of computers worldwide and effectively shut down over a dozen UK hospitals. But within months of stopping it, Hutchins was in police custody.
Why is it called WannaCry?
I worry that this is what is happening with the latest Internet contagion, which everyone has referred to as “WannaCry,” a friendly variation on “WanaCryptor,” the name of a piece of down market ransomware that was strapped to the rocket ship known as EternalBlue, a highly effective exploit of a vulnerability in ...
Can WannaCry spread through WIFI?
First, unlike your garden-variety ransomware which spreads via infected email attachments or websites, WannaCry also incorporates elements of a worm. Computer worms, unlike viruses, don't spread by infecting files. Instead, they spread via networks, seeking vulnerabilities in other connected computers.
Why was WannaCry so successful?
WannaCry was so successful because it leveraged an unpatched windows vulnerability. NotPetya did the same.
Can you remove WannaCry?
Have reputable anti-spyware or anti-virus software installed, keep it up-to-date, and scan the operating system with it regularly. If your computer is already infected with WannaCry, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate this ransomware.
How many people died from WannaCry?
Major cyberattacks, like the 2017 WannaCry cyberattack, have shut down major hospital systems — WannaCry took down the United Kingdom's National Health Service, for example. No deaths were directly linked to that attack, but most experts warned it was only a matter of time.
How long did WannaCry last?
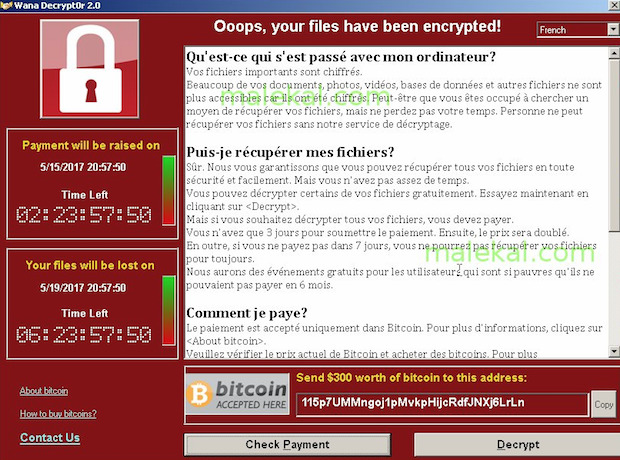
4 daysThe attack was estimated to have affected more than 200,000 computers across 150 countries, with total damages ranging from hundreds of millions to billions of dollars....WannaCry ransomware attack.Screenshot of the ransom note left on an infected systemDate12 May 2017 – 15 May 2017 (initial outbreak)Duration4 daysLocationWorldwide9 more rows
Who defeated WannaCry?
Marcus HutchinsAt 22, he single-handedly put a stop to the worst cyberattack the world had ever seen. Then he was arrested by the FBI.
How much money did WannaCry make?
$386,905 may not seem like much of a payday considering the number of devices infected and the damage caused by the attack, and it's not. Further, the attackers will need to convert that total to real money, and a considerable amount will be lost in that process.
How much damage did WannaCry cause?
Within a day, WannaCry had spread around the world, infecting more than 230,000 computer systems in 150 countries and costing approximately $4 billion in financial losses.
Who did WannaCry target?
WannaCry is a ransomware cryptoworm cyber attack that targets computers running the Microsoft Windows operating system. It was initially released on 12 May 2017. The ransomware encrypted data and demanded ransom of $300 to $600, paid in the cryptocurrency Bitcoin.
How was WannaCry detected?
The WannaCry kill switch functionality was soon accidentally discovered by security researcher Marcus Hutchins, who on May 12, registered a domain found in the ransomware's binary code.
How was WannaCry transmitted?
The way WannaCry spreads is by using corporate networks to jump to other Windows systems. Unlike phishing attacks, computer users don't have to click on a link or open an infected file.
What type of malware is iloveyou?
ILOVEYOU is also known as the "love letter virus" and the "love bug worm." Although commonly referred to as a computer virus, ILOVEYOU is actually a worm.
What is WannaCry vulnerability?
WannaCry spread using the Windows vulnerability referred to as MS17-010, which hackers were able to take advantage of using the exploit EternalBlue. The NSA discovered this software vulnerability and, rather than reporting it to Microsoft, developed code to exploit it.
What is WannaCry in computer?
Welcome to WannaCry, in which hackers lock up your files and demand payment in order to decrypt them. If you’ve seen this message on your computer, then you’ve either been infected with WannnaCry or a similar form of ransomware.
Where does WannaCry come from?
Though it’s not 100% certain who made WannaCry, the cybersecurity community attributes the WannaCry ransomware to North Korea and its hacker arm the Lazarus Group. The FBI along with cybersecurity researchers found clues hidden within the background of the code that suggested these origins.
What is ransomware?
As the name suggests, ransomware refers to malicious software that encrypts files and demands payment — ransom — in order to decrypt them. WannaCry remains one of the most well-known strains of ransomware out there. Why? Well, there are a few reasons why WannaCry is so notorious: 1 It’s wormable, meaning it was able to spread between computers and networks automatically (without requiring human interaction). 2 WannaCry relied on a Windows exploit that made millions of people vulnerable. 3 It resulted in hundreds of millions (or even billions) of dollars in damage. 4 The ransomware strain spread fast and furiously, only to be halted just as quickly. 5 Its catchy (and apt) name also made it memorable; wouldn’t you wanna cry too if you found all your important files locked up?
What is ransomware malware?
As the name suggests, ransomware refers to malicious software that encrypts files and demands payment — ransom — in order to decrypt them. WannaCry remains one of the most well-known strains of ransomware out there.
How much did WannaCry cost?
Though WannaCry demanded $300 in bitcoin (or $600 after the deadline passed) from a single user, the costs in damages were far higher. About 330 people or organizations made ransomware payments, which totaled 51.6 bitcoins (worth approximately $130,634 at the time of payment). That was the amount paid to the hackers, but the real cost of WannaCry was much greater.
How does WannaCry work?
WannaCry behaves like a worm, meaning it can spread through networks. Once installed on one machine, WannaCry is able to scan a network to find more vulnerable devices. It enters using the EternalBlue exploit and then utilizes a backdoor tool called DoublePulsar to install and execute itself.
What is WannaCry malware?
WannaCry was an attack that exploited a flaw in Windows in order to extort money from users and gained notoriety around the world.
How do I know if my computer has been infected by WannaCry?
So if you’re using a Mac you don’t have to worry about it. The only exception is that if you were using Boot Camp or a virtual machine to run Windows on your Mac. In those circumstances, if you were running an old version of Windows, it was possible to be infected.
What is WannaCry exploit?
WannaCry used an exploit developed by the US National Security Agency called Eternal Blue and which was released into the wild by a group of hackers called The Shadow Brokers. Eternal Blue exploited a vulnerability in Windows’ implementation of the SMB networking protocol and only worked on older Windows computers.
How to remove a virus from a computer?
1. Click on the Start menu. 2. Type Windows Defender into the search box. 3. Double-click Defender to run a scan. 4. If it finds anything, use Defender to remove it. If you can’t run Defender or it can’t remove the virus, the next step is to run a third party antivirus tool and use that to scan your PC and remove the virus.
Is WannaCry a ransomware attack?
There’s no direct equivalent, since WannaCry exploited a vulnerability in Windows. However, there have been and will be again ransomware attacks that affect Macs. For example, in 2016, a ransomware attack known as Patcher was distributed via BitTorrent, disguised as a tool to crack the authentication in Adobe Premiere CC and Microsoft Office 2016.
How many computers were hit by the worm?
Despite Microsoft releasing an emergency patch, and the discovery of a kill switch that stopped computers that were infected spreading the worm, meaning that the attack only lasted a few days, it was estimated that more than 200,000 computers in 150 countries were hit.
Does WannaCry affect Windows?
The WannaCry virus only affected Windows computers . However, Macs running Windows in Boot Camp or in a virtual machine could have seen those copies of Windows affected. The virus exploited a vulnerability in Windows implementation of SMB and encrypted files on the infected computer, demanding a ransom to unencrypt them.
How many computers did WannaCry infect?
WannaCry hit an estimated 230,000 computers. The malware affected the operations of hospitals, emergency services, petrol stations, and even factories. Some estimates put the financial cost of the attack in the billions.
What is an exploit in WannaCry?
An exploit is an unpatched system vulnerability that a cybercriminal can take advantage of for malicious activity. The flaw WannaCry exploits is in how Windows manages SMB (Server Message Block) protocol. In a nutshell, the SMB protocol allows network nodes to communicate. Although Microsoft patched the vulnerabilities in 2017, threat actors are using SMB vulnerabilities even today for Trojan and ransomware attacks because many Windows users don’t download updates.
Why was WannaCry so successful?
Ransomware like WannaCry typically works by encrypting your files or locking your system. It then demands payment in the shape of a cryptocurrency like Bitcoin because such currencies are more complex to trace than electronic money transfers, checks, or cold hard cash. However, WannaCry has some characteristics that make it different from a typical ransomware attack that you read about today.
What sectors were hardest hit by WannaCry?
The WannaCry attack spread so rapidly and infected so many computers worldwide that many industries were affected. These include:
Who created WannaCry?
The United States officially blames North Korea for the WannaCry attack, and it even indicted three North Koreans for the malware and the 2014 Sony Pictures Entertainment hack. Interestingly, the NSA (National Security Agency) may have also played a role in the WannaCry attack, albeit inadvertently.
What does WannaCry do if not paid?
WannaCry demands $300 in Bitcoin after locking a system. Later, it doubles the extortion fee. It also threatens to delete your data permanently within three days. Here at Malwarebytes, we recommend you don’t pay ransomware gangs, partially because it’s encouraging more ransomware gangs looking for a quick way to get rich. Additionally, there’s no guarantee that you’ll unlock your files or your computer. For example, not every victim of WannaCry got their files back after paying the fee, possibly due to a flaw in the ransomware itself.
What are some good ransomware mitigation strategies?
For the devices you use at home, use antivirus/anti-malware software that defends against all kinds of malicious software, including ransomware protection. For businesses, strategies to mitigate ransomware include:
Who Was Behind the WannaCry Cyber Attack?
Linguistic analysis of the ransom notes indicated the authors were fluent in Chinese and proficient in English as versions of the notes in those languages seemed human-written while other languages seemed to be machine-translated.
How Does WannaCry Work?
When executed, WannaCry checks to see if the kill switch domain is available. If it is unavailable the ransomware encrypts computer data and then attempts to exploit EternalBlue to spread to more computers on the Internet and on the same network.
Who Was Affected by WannaCry?
The scale was WannaCry was unprecedented with estimates of around 200,000 computers infected across 150 countries, with Russia, Ukraine, India and Taiwan the most affected according to Kaspersky Lab.
What Was the Reaction to WannaCry?
Much of the media attention around WannaCry was due to the fact that the National Security Agency (NSA) had discovered the vulnerability and used it to create an exploit for its own offensive work, rather than report it to Microsoft. Edward Snowden said if the NSA had "privately disclosed the flaw used to attack hospitals when they found it, not when they lost it, the attack may not have happened."
How to prevent WannaCry?
Here’s how to prevent attacks like WannaCry and minimize their impact if they do occur: 1 No single point of failure: Whether it's ransomware, hardware failure, database error, or something else. If your data is important, then it should be backed up, at least one other secure location. 2 Automate provisioning process: If an asset is taken down by ransomware or anything else, you should be able to return it to a working state as soon as possible. 3 Patch everything: Keep your systems up-to-date to avoid known exploits.
What is WannaCry 2.0?
WannaCry is also known as WannaCrypt, WCry, Wana Decrypt0r 2.0, WanaCrypt0r 2.0 and Wanna Decryptor. Once installed, WannaCry installed a backdoor in infected systems. WannaCry exploited a known vulnerability in older Windows systems called EternalBlue, which was found by the United States National Security Agency (NSA).
Why was WannaCry so successful?
While EternalBlue was quickly patched, much of WannaCry's success was due to organizations not patching or using older Windows systems. Quick patching and the discovery of kill switch domains prevented infected computers from spreading WannaCry.
What Is WannaCry Ransomware?
WannaCry ransomware is a crypto ransomware worm that attacks Windows PCs. It’s a form of malware that can spread from PC to PC across networks (hence the "worm" component) and then once on a computer it can encrypt critical files (the "crypto" part). The perpetrators then demand ransom payments to unlock those files. The name was derived from strings of code detected in some of the first samples of the virus.
What is the WannaCry exploit?
Dubbed EternalBlue, the exploit was eventually shared by a cybercriminal hacking group online in April 2017, and it allowed WannaCry's creators to trick Windows systems into running its code using the Server Message Block protocol. The way WannaCry spreads is by using corporate networks to jump to other Windows systems.
How Does a WannaCry Attack Work?
Once WannaCry is on a computer system, it searches for dozens of specific file types , including Microsoft Office files and picture, video and sound files . Then it executes a routine to encrypt the files, which can only be decrypted using an externally delivered digital key.
Where Did WannaCry Originate, and Is It Still Active?
In May 2017, WannaCry spread panic across corporate networks worldwide as it quickly infected more than 200,000 computers in 150 countries. Among those systems, the National Health Service of the U.K. was disrupted, Spain's Telefónica telecom service was threatened and banks in Russia were compromised. While the virus seemed to appear all at once, researchers later traced earlier versions to a North Korean organization known as the Lazarus Group.
What is WannaCry program?
The WannaCry program has several components. There's a primary delivery program that contains other programs, including encryption and decryption software. Once WannaCry is on a computer system, it searches for dozens of specific file types, including Microsoft Office files and picture, video and sound files.
How many WannaCry ransomwares were detected in 2021?
One report noted a 53% increase in WannaCry ransomware in March 2021 compared to January of this year, while another stated that WannaCry was the top ransomware family used in the Americas in January with 1,240 detections. More noteworthy: the latest variants being used by hackers no longer include a kill-switch URL.
What ransomware attack was the most widespread?
The 2017 WannaCry ransomware attack was one of the most widespread computer infections ever, and WannaCry attacks continue today.