
What are the most common social engineering techniques?
Top 5 social engineering techniques
- Phishing. Currently, the most common social engineering exploitation method. ...
- Baiting. Similar to phishing, this social engineering technique lures staff members leading to the inadvertent downloading of malware.
- A favour in return. Or Quid professional quo, aim to entice the target victim with a trade. ...
- Pretexting. ...
- Tailgating. ...
What are examples of social engineering techniques?
Social Engineering Attack Techniques
- Surveillance. Surveillance is social engineering 101. ...
- Grooming. Social grooming is often an integral part of a socially engineered attack. ...
- Deepfakes and AI. According to CSO Online, “ deepfakes are fake videos or audio recordings that look and sound just like the real thing ”.
- Psychology of Social Engineering. ...
What are examples of social engineering attacks?
Social Engineering Examples. Some of the largest social engineering attacks in recent years include the following: In 2017, more than a million Google Docs users received the same phishing email which informed them that one of their contacts was trying to share a document with them.
What are common social engineering attacks?
The Lowdown on Common Social Engineering Attacks
- -Tailgating isn’t just for cars. How many times have you been in a situation at a resort where someone has left their pool key back at their room.
- -Baiting. “I’ve never been good at fishing, but we’re referring to cybersecurity in this case.”-me. ...
- -Phishing Emails (they’re tricky) Phishing is extremely common, and for good reason. ...
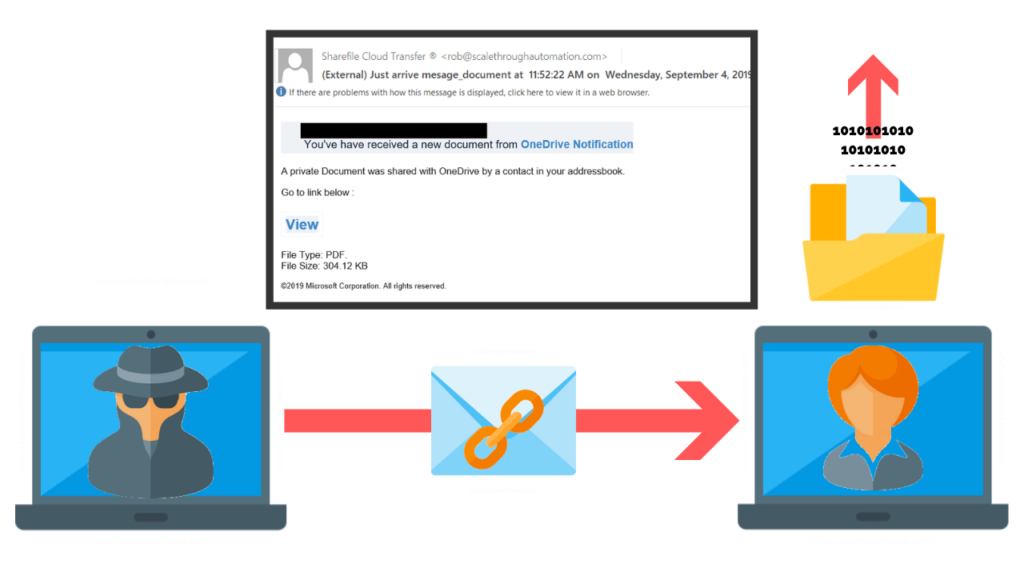
What is whaling vs phishing?
The difference between whaling and spear phishing is that whaling exclusively targets high-ranking individuals within an organization, while spear phishing usually goes after a category of individuals with a lower profile.
What is a whaling attack cyber?
A whaling attack is a method used by cybercriminals to masquerade as a senior player at an organization and directly target senior or other important individuals at an organization, with the aim of stealing money or sensitive information or gaining access to their computer systems for criminal purposes.
What is spearfishing in social engineering?
“Spear phishing” is a type of phishing campaign that targets a specific person or group and often will include information known to be of interest to the target, such as current events or financial documents.
Who are targets of whaling attacks?
A whaling attack, also known as whaling phishing or a whaling phishing attack, is a specific type of phishing attack that targets high-profile employees, such as the chief executive officer or chief financial officer, in order to steal sensitive information from a company.
What is whaling in simple words?
: the occupation of catching and extracting commercial products from whales.
What are the three types of whaling?
There are generally three types of whaling that the Commission regulates: commercial, scientific research, and aboriginal subsistence whaling.
What is the difference between phishing and spearfishing?
Spear phishing is a targeted attack on a specific person or organization, whereas general phishing campaigns are sent to a large volume of people.
What are the 4 types of social engineering?
Social engineering attack techniquesBaiting. As its name implies, baiting attacks use a false promise to pique a victim's greed or curiosity. ... Scareware. Scareware involves victims being bombarded with false alarms and fictitious threats. ... Pretexting. ... Phishing. ... Spear phishing.
What is dumpster diving in social engineering?
Dumpster diving and social engineering attacks Dumpster diving is a way for attackers to gain information that they use to establish trust. While attackers will also take any computer equipment they find, typically, the primary focus of a dumpster diving attack is to gain information about an organization.
Why is it called whaling?
The term "Whale" is borrowed from the casino industry, where it is used to describe a rich gambler who bets extraordinarily large amounts of money. Just like in the game industry, casinos want to "catch" the most high-betting whales, because they provide a lot of income for comparably little expense.
Who is responsible for whaling?
Japan and Iceland are the only two countries that currently use this provision. Japan has been engaged in scientific whaling since 1987, a year after the IWC moratorium on commercial whaling began. Iceland recently began "scientific whaling" in 2003 before resuming their commerical hunt in 2006.
What is whaling and why is it controversial?
Commercial whaling means hunting whales to sell the things that come from whales, like meat, oil and blubber. It was banned in 1986 by the International Whaling Commission (IWC) - a group whose job it is to look after whale conservation - after some species became almost extinct.
What is whaling in cyber security quizlet?
A whaling attack, also known as whaling phishing or a whaling phishing attack, is a specific type of phishing attack that targets high-profile employees, such as the CEO or CFO, in order to steal sensitive information from a company, as those that hold higher positions within the company typically have complete access ...
What is whaling and why is it important?
Whaling is the process of hunting of whales for their usable products such as meat and blubber, which can be turned into a type of oil that became increasingly important in the Industrial Revolution. It was practiced as an organized industry as early as 875 AD.
What is whaling and why is it controversial?
Commercial whaling means hunting whales to sell the things that come from whales, like meat, oil and blubber. It was banned in 1986 by the International Whaling Commission (IWC) - a group whose job it is to look after whale conservation - after some species became almost extinct.
Is whaling illegal now?
Whaling is illegal in most countries, however Iceland, Norway, and Japan still actively engage in whaling . Over a thousand whales are killed each year for their meat and body parts to be sold for commercial gain. Their oil, blubber, and cartilage are used in pharmaceuticals and health supplements.
What is a whaling attack?
Whaling is a term used to name the operation of targeting executives and other high profile targets such as politicians and celebrities with spear phishing attacks, commonly by creating serious-form well-customized due to the low number of targets in order to increase efficiency.
Why is whaling a play on words?
The term whaling is a play-on-words because an important person may also be referred to as a "big fish." In gambling, for examples, whales describe high-stakes rollers who are given special VIP treatment. - techtarget.com
What is social engineering?
Social Engineering aka SE, is nothing more or less than manipulating individuals into revealing data or acting based on a social engineer commands. It is the art of hacking human beings, the weaker ring in the security chain for the purpose of information gathering, fraud, or gaining system access. I would recommend that you read about this huge section of InfoSec and in the end of this article I will add some good sources.
Is phishing a real threat?
Even though phishing, in general, isn't that complicated, it still represents a real threat . Whaling or high-profile fraud, for instance, continues to grow by 67 percent mainly by email-based campaigns designed to con and steal money and to target finance departments with emails that look like they are coming from a company's chief.
Should companies agree on a conventional method to communicate in order to make it easier to sense intrusion?
In fact, companies should agree on a conventional method to communicate in order to make it easier to sense intrusion. Likewise, more strict email filtering rules should be applied in order to prevent spam email from finding a way into the employees' inboxes.Furthermore, every email should be treated as a potential threat and handled with caution.
How Does Social Engineering Work?
Hackers develop different tactics to support their social engineering pursuits. Most social engineering attacks follow this path:
Why do hackers use social engineering?
To exploit that vulnerability, many hackers engage in social engineering to support their cyberattack efforts and obtain valuable information. Social engineers target humans, rather than technology, to gather useful intel. Hollywood frequently glorifies the savvy con man for his ability to charm and disarm.
What is a quid pro quo?
Quid Pro Quo: The quid pro quo attack is a variation of baiting. Often known as the “something for something” social engineering technique, the quid pro quo attack involves promising a service or benefit for complying with the request of an attacker. For example, a social engineer may promise a free software upgrade to entice a user to download what is actually malware to their system.
What is a baiting attack?
Baiting: Baiting is a social engineering attack where the attacker entices the user with a free item to lure them into clicking on a link. This may come in the form of a free music or movie download lined up with the user’s interests. When the unsuspecting user clicks the link, they become infected with malware.
What happens when you click on a malicious link?
When the unsuspecting user clicks the link, they become infected with malware. Phishing: Phishing is a type of social engineering attack that uses email, phone or text to entice a user to click on a malicious link. The communication appears to be from a legitimate source connected to the user.
What is tailgating in social engineering?
Tailgating: This social engineering tactic is a physical attack. With tailgating, a hacker gains access to restricted areas of a building by following an approved employee into the building and piggybacking on their credentials. In these cases, the social engineer often pretends to be an employee or even a delivery person.
How to prevent social engineering attacks?
The best form of prevention against social engineering attacks is end-user training. Teaching your employees how to recognize social engineering tactics and avoid them is of the utmost importance.
