How do you create your own certificate?
Part 1 Part 1 of 4: Creating your CA Certificate Download Article
- Generate your CA's private key by issuing the following command. Store this certificate and the password in a safe place.
- Create a certificate signing request.
- Fill out the information as much as possible. ...
- (If you don't know what this is, do not change this. ...
- Inspect your CA certificate. ...
How to create X 509 certificate?
- Provide the Device ID that matches the subject name of your device certificates.
- Select the X.509 CA Signed authentication type.
- Select Save.
How do I generate a self signed certificate?
IT: How To Create a Self Signed Security (SSL) Certificate and Deploy it to Client Machines
- Creating a Self Signed Certificate on IIS. ...
- Exporting the Certificate. ...
- Deploying to Client Machines. ...
- Internet Explorer & Google Chrome – Installing the Certificate Locally. ...
- Firefox – Allowing Exceptions. ...
- Conclusion. ...
- Links
How do I create a custom certificate?
# Via the macOS Keychain App Link copied
- Open the macOS Keychain app
- If required, make sure you’ve selected the System Keychain (older macOS versions default to this keychain)
- Go to File > Import Items…
- Select your private key file (i.e. ...
- Search for whatever you answered as the “Common Name” name above
- Double-click on your root certificate in the list
- Expand the Trust section
See more

How do I know if my certificate is x509?
You can identify a certificate in several ways: by the hash of the certificate, by the issuer and serial number, or by the subject key identifier (SKI). The SKI provides a unique identification for the certificate's subject public key and is often used when working with XML digital signing.
Is x509 a SSL certificate?
SSL/TLS X. 509 certificates are digital files that are used for Secure Sockets Layer (SSL) or Transport Layer Security (TLS). An SSL/TLS certificate is one of the most popular types of X. 509 certificates or a type of public-key certificate which uses the X.
Is PEM x509 format?
PEM (originally “Privacy Enhanced Mail”) is the most common format for X. 509 certificates, CSRs, and cryptographic keys. A PEM file is a text file containing one or more items in Base64 ASCII encoding, each with plain-text headers and footers (e.g. -----BEGIN CERTIFICATE----- and -----END CERTIFICATE----- ).
WHO issues x509 certificate?
ITU-TInformation technology - Open Systems Interconnection - The Directory: Public-key and attribute certificate frameworksStatusIn force (Recommendation)Latest version9.1 October 14, 2021OrganizationITU-TCommitteeITU-T Study Group 176 more rows
Where are x509 certificates stored?
Certificates stores are kept in the system registry under the keys HKEY_LOCAL_MACHINE\Software\Microsoft\SystemCertificates and HKEY_CURRENT_USER\Software\Microsoft\SystemCertificates. Each user has a MY certificate store which contains his/her personal certificates.
Is .PEM and .CRT the same?
crt keeps a signed certificate, whereas . csr is the certificate signing request. Also, . pem just indicates that the content (can be a key, certificate, ...) is Base64 encoded.
Are .CER and .PEM the same?
cer just stands for certificate. It is normally DER encoded data, but Windows may also accept PEM encoded data. You need to take a look at the content (e.g. using the file utility on posix systems) to see what is within the file to be 100% sure.
Is .CRT PEM format?
CRT belongs to the PEM format of certificates that are Base64 ASCII encoded files.
What is in a SSL certificate?
An SSL certificate is a digital certificate that authenticates a website's identity and enables an encrypted connection. SSL stands for Secure Sockets Layer, a security protocol that creates an encrypted link between a web server and a web browser.
Is SSL same as TLS?
Transport Layer Security (TLS) is the successor protocol to SSL. TLS is an improved version of SSL. It works in much the same way as the SSL, using encryption to protect the transfer of data and information. The two terms are often used interchangeably in the industry although SSL is still widely used.
What is x509 authentication service?
X. 509 digital certificate is a certificate-based authentication security framework that can be used for providing secure transaction processing and private information. These are primarily used for handling the security and identity in computer networking and internet-based communications.
Does x509 certificate contains private key?
An X. 509 certificate consists of two keys, namely a public key and a private key. This key pair, depending upon the application, allows you to sign documents using the private key so that the intended person can verify the signature using the public key related to it.
What is X.509 certificate?
X.509 certificates are used in many Internet protocols, including TLS/SSL, which is the basis for HTTPS, the secure protocol for browsing the web. They are also used in offline applications, like electronic signatures. An X.509 certificate contains a public key and an identity (a hostname, or an organization, or an individual), ...
When was the X.509 issued?
X.509 was initially issued on July 3, 1988, and was begun in association with the X.500 standard. The first tasks of it was providing users with secure access to information resources and avoiding a cryptographic attack « Man-in-the-middle attack ».
What is a certificate chain?
A certificate chain (see the equivalent concept of "certification path" defined by RFC 5280 section 3.2) is a list of certificates (usually starting with an end-entity certificate) followed by one or more CA certificates (usually the last one being a self-signed certificate), with the following properties:
What is RFC 5280?
RFC 5280 (and its predecessors) defines a number of certificate extensions which indicate how the certificate should be used. Most of them are arcs from the joint-iso-ccitt (2) ds (5) id-ce (29) OID. Some of the most common, defined in section 4.2.1, are:
What is the last certificate in the list?
The last certificate in the list is a trust anchor: a certificate that you trust because it was delivered to you by some trustworthy procedure
How does a digital signature work?
Digital signature systems depend on secure cryptographic hash functions to work. When a public key infrastructure allows the use of a hash function that is no longer secure, an attacker can exploit weaknesses in the hash function to forge certificates. Specifically, if an attacker is able to produce a hash collision, they can convince a CA to sign a certificate with innocuous contents, where the hash of those contents is identical to the hash of another, malicious set of certificate contents, created by the attacker with values of their choosing. The attacker can then append the CA-provided signature to their malicious certificate contents, resulting in a malicious certificate that appears to be signed by the CA. Because the malicious certificate contents are chosen solely by the attacker, they can have different validity dates or hostnames than the innocuous certificate. The malicious certificate can even contain a "CA: true" field making it able to issue further trusted certificates.
How to retrieve intermediate certificate?
However, it's also possible to retrieve the intermediate certificate by fetching the "CA Issuers" URL from the end-entity certificate.
How Do I Get an X.509 Certificate?
A critical component of deploying X.509 certificates is a trusted certification authority or agent to issue certificates and publish the public keys associated with individuals' private keys. Without this trusted CA, it would be impossible for senders to know they are in fact, using the correct public key associated with the recipient's private key and not the key associated with a malicious actor intending to intercept sensitive information and use it for nefarious purposes.
What is X.509 PKI?
The most common use case of X.509-based PKI is Transport Layer Security (TLS)/Secure Socket Layer (SSL), which is the basis of the HTTPS protocol, ...
How does digital signature work?
Digital signatures are a specific type of electronic signature that leverages PKI to authenticate the identity of the signer and the integrity of the signature and the document. Digital signatures cannot be altered or duplicated in any way, as the signature is created by generating a hash, which is encrypted using a sender's private key. This cryptographic verification mathematically binds the signature to the original message to ensure that the sender is authenticated and the message itself has not been altered.
How are digital certificates used to establish trust?
To further establish the trust of an identity, multiple digital certificates are often combined to build a hierarchical chain of trust that provides a series of verification layers. As previously mentioned, each must be signed by an issuer CA as part of the X.509 verification process. The CA is named and stored in the root of the certificate. Additional intermediate certificates can be included in the trust chain and must be validated.
What is a trust certificate?
Trust - Digital certificates allow individuals, organizations, and even devices to establish trust in the digital world. As the foundation for all digital identities, X.509 certificates are everywhere and are essential to every connected process from websites to applications to endpoint devices and online documents. For example, without these, we wouldn't be able to trust that www.amazon.com is actually Amazon's website.
What is the validity period of a certificate?
Validity period of the certificate – the start/end date and time it's valid and can be trusted. Subject distinguished name – the name of the identity the certificate is issued to. Subject public key information – the public key associated with the identity.
When was the X.509 standard first published?
The first version of the X.509 standard was published back in 1988 . Looking to formalize the rules for certificate issuance, the Telecommunication Standardization Sector of the ITU (ITU-T) developed a hierarchical system for distinguished names that followed the electronic directory service rules for X.500 and was inspired by the systems used to assign telephone numbers globally but applied to the more flexible organizational requirements of the Internet.
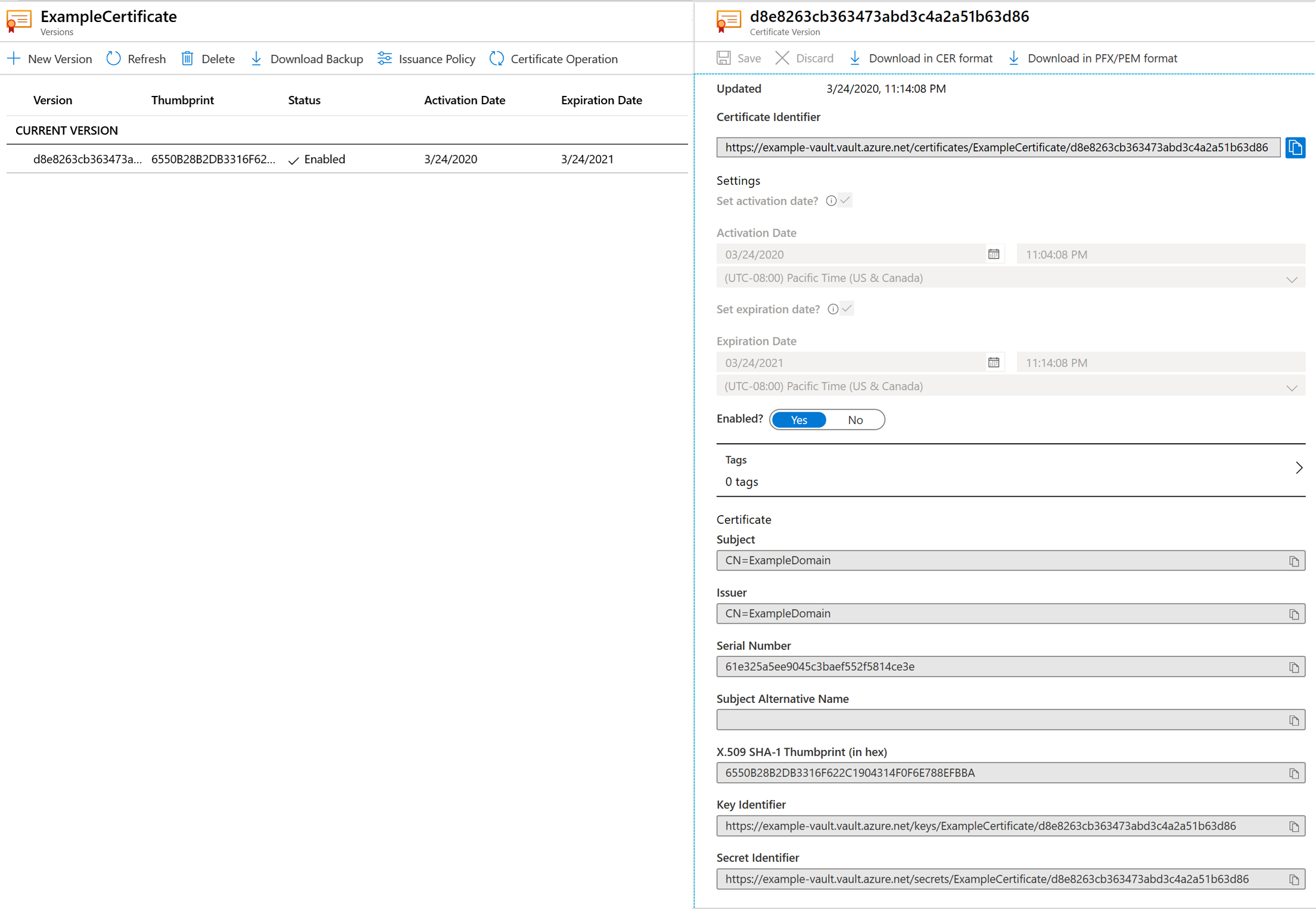
What is an X509 Certificate?
In a nutshell, X.509 digital certificates include SSL/TLS, code signing, document signing and email signing certificates, etc.
What is X509 standard information?
Standard information in an X509 certificate includes: Version — The version of X.509 that applies to the certificate. Serial number — Serial number assigned by certificate authority to distinguish one certificate from other certificates. Algorithm information — The hashing algorithm used by the CA to sign the certificate ...
What are the two types of encryption?
When it comes to types of encryption methods, there are mainly two: symmetric encryption and asymmetric encryption. While there are several notable differences between these encryption methods, the biggest is the number of cryptographic keys used. In symmetric encryption , only one key is used.
What is the validity period of a certificate?
Validity period of the certificate — The period during which certificate is valid to use. Subject distinguished name — The name of the identity the certificate is issued to (individual, organization, domain name, etc.) Subject public key information — The public key of the certificate.
What is digital signature?
Digital Signature. A digital signature is added by certificate authority (CA) to assure users that the certificate in use is genuine. In other words, digital signature provides the proof that the certificate you have been given is the exact certificate issued by a trusted CA to the website in question.
What is the hashing algorithm used by the CA to sign the certificate?
Algorithm information — The hashing algorithm used by the CA to sign the certificate (SHA-2 in almost all cases).
What is verification of identity?
To verify the identity of a website, individual or an organization. In other words, they let users know that the person/organization really is who they say they are.
What is X.509 certificate?
X.509 does not define how certificate contents should be encoded to store in files. However, two commonly used encoding schemas are used to store X.509 certificates in files, DER and PEM. DER (Distinguished Encoding Rules) is a data object encoding schema that can be used to encode certificate objects. DER is the most popular file format ...
What is X509 version 2?
In 1993, X509 version 2 added two new fields: Issuer Unique Identifier and Subject Unique Identifier. These fields are now considered deprecated by the IETF, and should not be used in your certificates. The widespread use of the Internet inspired further development of the hierarchical naming system.
What is SSL/TLS authentication?
During SSL/TLS connections, the server authenticates according to the handshake and record protocols. When initiating the handshake protocol, the server presents a signed X.509 certificate to the client. Only the server needs to be validated in most secure browsing sessions. Client authentication is less common but would require the server to verify the client’s certificate as well.
How many root certificates does Firefox have?
For example, at the current time of writing, the Firefox trust store holds 150 root certificates that are automatically trusted by their web browser. In contrast, Google Chrome uses the underlying OS’s trust store to determine whether a certificate is trusted, with a few exceptions.
What is X.509 used for?
X.509 is most used for SSL/TLS connections to ensure that the client (e.g., a web browser) is not fooled by a malicious impersonator pretending to be a known, trustworthy website.
When was X509 published?
In 1988 , X.509 version 1 was published. The hierarchical arrangement of the distinguished names followed the rules for X.500. These rules were inspired by the systems used to assign telephone numbers globally. In 1993, X509 version 2 added two new fields: Issuer Unique Identifier and Subject Unique Identifier.
Is a root CA a hierarchical or nonhierarchical CA?
However, the certification path structure can be hierarchical (like a tree with a single source root CA) or non-hierarchical (like a forest with many cross-certified root CAs). It’s easier to understand cross certification by imagining international telephone calls. If each country code is represented by a root CA, then cross-certification agreements among the CA would extend the calling reach. When two roots CA sign each other’s certificates, they inherently trust all other certificates in each other’s paths.
What does a DER-encoded certificate look like?
The DER-encoded SSL/TLS certificate for www.ssl.com is shown below (click to view):
How to contact SSL secure?
Thank you for choosing SSL.com! If you have any questions, please contact us by email at [email protected], call 1-877-SSL-SECURE, or just click the chat link at the bottom right of this page. You can also find answers to many common support questions in our knowledgebase.
What does checking certificate file extension do?
Once you’ve got your certificate files, checking the certificate file extension will allow you to know what’s in the file, and which file fits best your needs.
What is the extension for a Tomcat certificate?
If I’m installing on a Windows server or Java Tomcat server was chosen, you should receive a file with .cer, .p7s or .p7b file extension. Those should be equally accepted by a server designed to use such certificate files. The file extension may vary between different certificate issuer companies.
What file extensions are used in SSL activation?
If Any other server (ex. Apache) was selected during SSL activation, the Certificate Authority’s email should contain files with .crt and .ca-bundle file extensions.

Overview
In cryptography, X.509 is an International Telecommunication Union (ITU) standard defining the format of public key certificates. X.509 certificates are used in many Internet protocols, including TLS/SSL, which is the basis for HTTPS, the secure protocol for browsing the web. They are also used in offline applications, like electronic signatures.
An X.509 certificate binds an identity to a public key using a digital signature. A certificate contai…
History and usage
X.509 was initially issued on July 3, 1988, and was begun in association with the X.500 standard. The first tasks of it was providing users with secure access to information resources and avoiding a cryptographic man-in-the-middle attack. It assumes a strict hierarchical system of certificate authorities (CAs) for issuing the certificates. This contrasts with web of trust models, like PGP, where anyone (not just special CAs) may sign and thus attest to the validity of others' key certifi…
Certificates
X.509 certificates bind an identity to a public key using a digital signature. In the X.509 system, there are two types of certificates. The first is a CA certificate. The second is an end-entity certificate. A CA certificate can issue other certificates. The top level, self-signed CA certificate is sometimes called the Root CA certificate. Other CA certificates are called intermediate CA or subordinate CA certificates. An end-entity certificate identifies the user, like a person, organizati…
Certificate chains and cross-certification
A certificate chain (see the equivalent concept of "certification path" defined by RFC 5280 section 3.2) is a list of certificates (usually starting with an end-entity certificate) followed by one or more CA certificates (usually the last one being a self-signed certificate), with the following properties:
1. The Issuer of each certificate (except the last one) matches the Subject of the next certificate in the list
Sample X.509 certificates
This is an example of a decoded X.509 certificate that was used by wikipedia.org and several other Wikipedia websites. It was issued by GlobalSign, as stated in the Issuer field. Its Subject field describes Wikipedia as an organization, and its Subject Alternative Name (SAN) field for DNS describes the hostnames for which it could be used. The Subject Public Key Info field contains an ECDSA public key, while the signature at the bottom was generated by GlobalSign's RSA private key.
Security
There are a number of publications about PKI problems by Bruce Schneier, Peter Gutmann and other security experts.
• Use of blocklisting invalid certificates (using CRLs and OCSP),
• CRLs are notably a poor choice because of large sizes and convoluted distribution patterns,
PKI standards for X.509
• PKCS7 (Cryptographic Message Syntax Standard — public keys with proof of identity for signed and/or encrypted message for PKI)
• Transport Layer Security (TLS) and its predecessor SSL — cryptographic protocols for Internet secure communications.
• Online Certificate Status Protocol (OCSP) / certificate revocation list (CRL) — this is to check certificate revocation status
PKIX Working Group
In 1995, the Internet Engineering Task Force in conjunction with the National Institute of Standards and Technology formed the Public-Key Infrastructure (X.509) working group. The working group, concluded in June 2014, is commonly referred to as "PKIX." It produced RFCs and other standards documentation on using and deploying X.509 in practice. In particular it produced RFC 3280 and its successor RFC 5280, which define how to use X.509 in Internet protocols.