What is XXe (XML eXternal Entity injection)?
XXE (XML External Entity Injection) is a common web-based security vulnerability that enables an attacker to interfere with the processing of XML data within a web application. While XML is an extremely popular format used by developers to transfer data between the web browser and the server, this results in XXE being a common security flaw.
What are XML external entities?
If the document refers to an external DTD, the custom entity whose definition is located outside of the DTD where you’ve declared them are referred to as XML external entities. XML external entity (XXE) injection is a security vulnerability that allows malicious parties to interfere with the application's processing of XML data.
What is XXE vulnerability in XML?
XML external entity injection (also known as XXE) is a web security vulnerability that allows an attacker to interfere with an application's processing of XML data. It often allows an attacker to view files on the application server filesystem, and to interact with any backend or external systems that the application itself can access.
Is there still work to be done on XML eXternal Entity attacks?
There’s still some work to be done. This is an example of a Project or Chapter Page. An XML External Entity attack is a type of attack against an application that parses XML input. This attack occurs when XML input containing a reference to an external entity is processed by a weakly configured XML parser.
See more

What does an XML external entities attack do?
In a nutshell, an XML External Entities attack, or XXE injection, is an attack that takes advantage of XML parsing vulnerabilities. It targets systems that use XML parsing functionalities that face the user and allow an attacker to access files and resources on the server.
What is an XML injection?
XML injection is when user-supplied input isn't escaped or sanitized before it is added to a web application's XML documents; they are processed and executed.
What is XML injection in cyber security?
Description: XML injection XML or SOAP injection vulnerabilities arise when user input is inserted into a server-side XML document or SOAP message in an unsafe way. It may be possible to use XML metacharacters to modify the structure of the resulting XML.
What is XML entity processing?
XML External Entity Processing, or XXE, is a vulnerability where an attacker can abuse the XML 1.0 specification for processing XML Entities to have a server include local or remote data when processing XML.
What are XML entities used for?
What are XML entities? XML entities are a way of representing an item of data within an XML document, instead of using the data itself. Various entities are built in to the specification of the XML language. For example, the entities < and > represent the characters < and > .
How can you prevent the XML external entity vulnerability?
The safest way to prevent XXE is always to disable DTDs (External Entities) completely. Depending on the parser, the method should be similar to the following: factory. setFeature("http://apache.org/xml/features/disallow-doctype-decl", true);
What is entity injection?
XML external entity injection (also known as XXE) is a web security vulnerability that allows an attacker to interfere with an application's processing of XML data.
What is one way to prevent XML injection attacks?
The simplest way to prevent XXE attacks is to configure the XML parser to avoid resolving external references entirely.
What are the 3 basic security requirements in XML?
Integrity and signatures – XML Digital Signature. Confidentiality – XML Encryption. Key Management – XML Key Management Specification (XKMS)
What is XML Internet technology?
XML stands for extensible markup language. A markup language is a set of codes, or tags, that describes the text in a digital document. The most famous markup language is hypertext markup language (HTML), which is used to format Web pages.
How is XML vulnerable?
XML processing modules may be not secure against maliciously constructed data. An attacker could abuse XML features to carry out denial of service attacks, access logical files, generate network connections to other machines, or circumvent firewalls.
What are the two types of entity in XML?
In general, we have three types of entities: internal entities, external entities, and parameter entities.
What is internal and external entity in XML?
Internal Entities: An internal entity (as we saw in above example) is one that is defined locally. Basic purpose of an internal entity is to avoid duplications by using same entity reference multiple times. External Entities: The difference with Internal Entity is; the external entity is defined in an separate file.
What is XML and how does it work?
XML (Extensible Markup Language) is a markup language similar to HTML, but without predefined tags to use. Instead, you define your own tags designed specifically for your needs. This is a powerful way to store data in a format that can be stored, searched, and shared.
What are the 2 main uses of XML?
Metadata applications: XML makes it easier to express metadata in a portable, reusable format. Pervasive computing: XML provides portable and structured information types for display on pervasive (wireless) computing devices such as personal digital assistants (PDAs), cellular phones, and others.
What is XML and why it is needed?
XML stands for Extensible Markup Language. It is a text-based markup language derived from Standard Generalized Markup Language (SGML). XML tags identify the data and are used to store and organize the data, rather than specifying how to display it like HTML tags, which are used to display the data.
What are the 3 types of physical vulnerabilities?
Measuring Physical Vulnerability for population Population vulnerability can be subdivided into direct physical population vulnerability (injury, casualties, and homelessness) and indirect social vulnerability and capacity.
Is XML file secure?
XML encryption can be used to assure data confidentiality of transmitted messages. You can encrypt an entire message or choose to encrypt only certain elements of the message. However, using XML encryption (either separately from XML digital signatures or in conjunction) can have potential security implications.
How XML external entity XXE attacks are performed?
An XML External Entity attack is a type of attack against an application that parses XML input. This attack occurs when XML input containing a reference to an external entity is processed by a weakly configured XML parser.
What is XML healthcare?
Extensible markup language (XML) in health care: integration of structured reporting and decision support.
What does an LDAP injection do?
An LDAP injection attack exploits security loopholes caused by unsanitized user input data. In other words, LDAP injections create malformed queries to gain access in order to potentially change data in a directory. LDAP queries contain special characters such as asterisks, brackets, ampersands and quotes.
What are HTML injections?
HTML Injection also known as Cross Site Scripting. It is a security vulnerability that allows an attacker to inject HTML code into web pages that are viewed by other users.
What is SQL injection used for?
SQL injection, also known as SQLI, is a common attack vector that uses malicious SQL code for backend database manipulation to access information that was not intended to be displayed. This information may include any number of items, including sensitive company data, user lists or private customer details.
What is parameter entity?
Parameter entities are only used in Document Type Definitions (DTDs). A parameter entity starts with the % character. This character instructs the XML parser that a parameter entity (not a general entity) is being defined.
What is XXE injection?
An XML External Entity (XXE) attack (sometimes called an XXE injection attack) is a type of attack that abuses a widely available but rarely used feature of XML parsers. Using XXE, an attacker is able to cause Denial of Service (DoS) as well as access local and remote content and services. XXE can be used to perform Server Side Request Forgery (SSRF) iducing the web application to make requests to other applications. In some cases, XXE may even enable port scanning and lead to remote code execution. There are two types of XXE attacks: in-band and out-of-band (OOB-XXE).
How to avoid XXE vulnerabilities?
The best way to avoid XXE vulnerabilities is to completely disable document type definitions (DTDs) in your XML parser. If this is not possible, you must disable external entities and external document type declarations for your parser.
What is XML format?
XML (Extensible Markup Language) is a very popular data format. It is used in everything from web services (XML-RPC, SOAP, REST) through documents (XML, HTML, DOCX) to image files (SVG, EXIF data). To interpret XML data, an application needs an XML parser (also known as the XML processor).
Why is XXE a vulnerability?
XXE vulnerabilities are caused by the configuration of XML parsers. XML parsers that work with web servers often allow you to use XML entities from external sources. An attacker may abuse this mechanism to include malicious content or access sensitive information.
What is the problem with XXE?
The primary problem for an attacker using XXE is how to access text files with XML-like content ( files that contain XML special characters such as &, <, and >). XML already has a workaround for this problem. There are legitimate cases when you may need to store XML special characters in XML files. Special XML characters in CDATA (Character Data) tags are ignored by the XML parser.
Why do attackers use XML?
Attackers can use XML entities for much more than reducing application availability. This is because you do not have to define XML entities in the XML document. In fact, XML entities can come from just about anywhere – including external sources (hence the name XML External Entity). This is where XXE becomes a type of a Server Side Request Forgery (SSRF) attack.
What is XML data?
XML is a software and hardware-independent tool for storing and transporting data via the internet or a corporate network. It doesn’t do anything; it is just a way of storing information in tags so that it can be shared in a structured and consistent manner. Like spoken language, you need to speak the same language to understand one another.
What is XML external entity injection?
Now that’s been cleared up, we can begin explaining how attackers can target XML software vulnerabilities to harm web applications.
Types of XXE attacks
XXE attacks range in type and motive. They can be aimed at retrieving files if your applications are using components with known vulnerabilities or if there is insufficient logging & monitoring, broken access control, or broken authentication. The file’s contents could result in sensitive data exposure of almost any data you store or send.
What is an XML external entity attack?
An XML External Entity attack is a type of attack against an application that parses XML input. This attack occurs when XML input containing a reference to an external entity is processed by a weakly configured XML parser. This attack may lead to the disclosure of confidential data, denial of service, server side request forgery, port scanning from the perspective of the machine where the parser is located, and other system impacts.
What is XML 1.0?
The XML 1.0 standard defines the structure of an XML document. The standard defines a concept called an entity, which is a storage unit of some type. There are a few different types of entities, external general/parameter parsed entity often shortened to external entity, that can access local or remote content via a declared system identifier. ...
Where is tainted data allowed?
Tainted data is allowed within the system identifier portion of the entity, within the document type declaration (DTD).
Can XML be validated?
Since the whole XML document is communicated from an untrusted client, it’s not usually possible to selectively validate or escape tainted data within the system identifier in the DTD. Therefore, the XML processor should be configured to use a local static DTD and disallow any declared DTD included in the XML document.
Where is XML stored?
Data in XML is stored in tags and usually in a parent-child structure. Look at the following example:
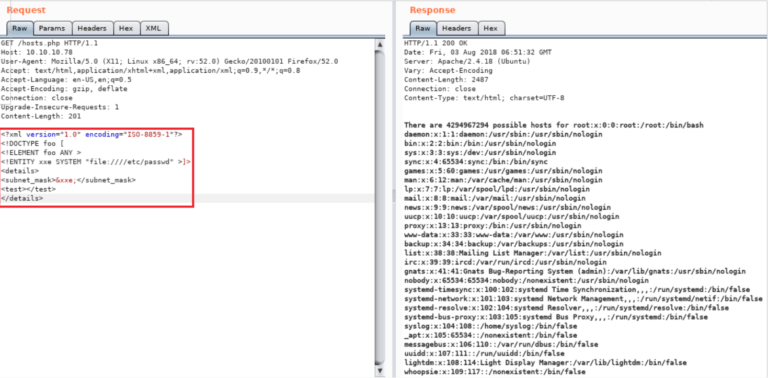
What can XXE injections do?
Hackers can use XXE injections to get access to system files that can hold sensitive information such as passwords, application details, security configuration, etc. And once the hacker gets access to the server, they can also change the configuration.
What are XXE vulnerabilities?
XXE vulnerabilities exist in web applications that use XML for data exchange. We’ve seen a few examples of XML structure and how data is stored. Suppose a web application is using XML data; if it is, an attacker can interfere with the request and manipulate it. Attackers can inject malicious code in XML, similar to SQL injection or command injection, to obtain the desired results.
Why are XXE vulnerabilities so dangerous?
XXE vulnerabilities are very dangerous because they give the hacker access to the backend system. What exactly a hacker can do by exploiting this vulnerability varies based on use case and configuration. Let’s look at a few scenarios.
How to prevent XXE vulnerability?
The main entry point for XXE injections is DTDs. The easiest way to prevent XXE vulnerability is by disabling DTDs for your application. Disabling DTDs might not be suitable for all scenarios. If that’s your case and you don’t want to do it, you can use input validation to prevent malicious injections.
What is a DTD in XML?
XML has a feature called Document Type Definition (DTD), which has the information about the structure of the XML document. The elements within these DTD documents are called entities. Entities are defined inside the DOCTYPE header, and they’re mainly used to fetch data from remote external systems.
What is the language used to exchange data?
When you have a web application, there’s an exchange of data. One of the languages that can be used for this exchange of data is Extensible Markup Language (XML). XML focuses on storing and organizing data rather than focusing on how to display data on the application.