
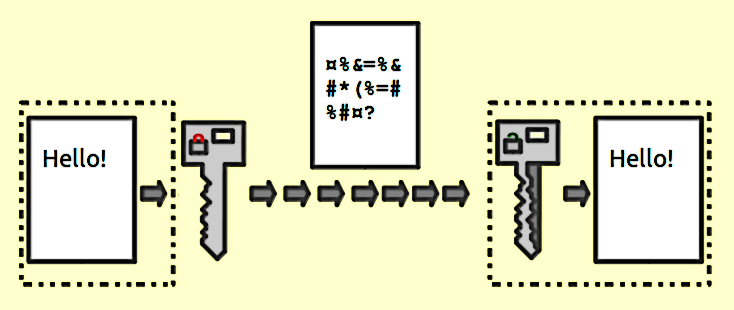
What Is Wireless Encryption and Why Is It Used?
- Not all encryption types are supported on all routers and adapters. ...
- The default encryption key may be located on the bottom of your router or in the manual, depending on the router manufacturer.
- You can locate the encryption key when you log into the router setup page, if you have created your own encryption key. ...
How do I find the wireless encryption key on a router?
Check the checkbox in front of the "Show Characters" option. The Wireless Encryption Key is listed in the field labeled "Network Security Key." Access the Wireless Encryption Key on a Router Step 1 Open a web browser and enter the URL for the Administration interface for the router. This URL may be found in the user manual for the router.
What is a wireless encryption key (WEP)?
WEP requires a Wireless Encryption Key to access the wireless network. The key is encrypted and stored on the router and on any computers that are connected to the router.
How do I find the WEP key for my Device?
Click the "Wireless Settings" link from the main page of the interface and scroll to the "Security Encryption (WEP) Key section. The Wireless Encryption Key is listed in the field labeled "Key 1." The WEP key will be an alpha-numeric string.
What is a wireless network security key (WLAN security key)?
A wireless network security key is the password required to be able to connect your PC to a secured access point (ex: router) on a wireless network.
Method 1: Using Powershell
We can use PowerShell to retrieve all the network passwords stored in your computer and save them to an external note file on your desktop. This is...
Method 2: Using Command Prompt
If you require a little more information regarding a network, we can use the command prompt to find all the details. First, we will list all the sa...
Method 3: Using Wireless Network Properties
We can also retrieve the security key of any network using the Wireless Network Properties. This method can be executed if you are currently connec...
Method 4: Using Your Router
You can also retrieve the password of your wireless network using your router. First, you would need the IP to open the settings of your router usi...
Encryption Type
64-bit: This configuration requires a ten character password when you use a hexadecimal (zero to nine and A-F) digits or eight characters when you use ASCII characters.
Advantages
Automatically configures a wireless network with a network name (SSID) and a strong WPA security key for authentication and data encryption.
Disadvantages
Ad-Hoc mode where wireless devices communicate directly to each other without an access point is not supported.
How Do I Use WPS
PIN (Personal Identification Number) Method: A PIN has to be taken from either a sticker label or the Web interface of the WPS device. This PIN is entered in the access point or client WPS device to make the connection.
What is WPA2 encryption?
WPA2 is still used today as the standard for robust consumer-level wireless encryption. Note. Most routers offer two types of WPA2 encryption, called WPA2-Personal and WPA2-Enterprise. The enterprise version of WPA2 is for corporate settings where an IT department controls company-wide security policies.
What is WPA2 password?
All these methods require a password, also known as an encryption key when you try to connect. If you provide the correct key, a wireless connection is established. I don't know what my key is.
How to access router configuration?
Once you have connected to your wireless router (by a wired connection, or using the default wireless network credentials), you can access your router 's configuration in a web browser. In a browser window, enter your router's IP address in your browser's address bar, and press Enter.
How to connect to a router?
Therefore, to connect to the router, you have two options: 1 Create a wired connection to the router. 2 Reset the router to its factory defaults.
What is WPA2 used for?
WPA2 is an updated version of WPA which was introduced in 2004. It enforces the use of AES and implements some stronger supporting protocols such as CCMP (Counter Cipher Mode). While WPA2 still has some known vulnerabilities, they require significant computing resources, and the attacker must already have access to the local wireless network. WPA2 is still used today as the standard for robust consumer-level wireless encryption.
What are the three types of authentication for consumer Wi-Fi?
The three types of authentication for consumer Wi-Fi are WEP, WPA and WPA2. Most home routers have all three options, but WPA2 is the most secure and should always be used if possible.
How do I connect to my wireless network?
How do I connect to the wireless network? If you forgot the key for connecting to your wireless network, you need to access the router's configuration interface using an Internet browser. Normally, you could do this over the wireless network. But in this case, you can't — because you don't have the password.
Where to find wireless security key?
You will see the wireless security key under the tab of Security settings and on the field of Key content. This method is useful if you require more details than just the password of the network.
How to find my wireless password?
Navigate to your desktop and locate the file “ WirelessNetworkPasswords.txt ”. Open it. Here you will see two columns: one for the wireless network ID and the other for its password.
How to get password for wireless network?
You can also retrieve the password of your wireless network using your router. First, you would need the IP to open the settings of your router using your computer. This is usually printed on the back of your router or in its box. The IP’s are like:
What is the default password for a device?
The default password and username for most of the devices are “ admin ”. You can always consult your box if you haven’t changed the password yourself. Enter the credentials and get access to the settings page. Once in the Settings, navigate to WLAN settings or Security settings. The options vary from device to device.
Why do people use wireless networks?
Wireless networking is an effective method which homes and businesses use to avoid the costly process of introducing cables in a building . Majority of the users use wireless networks for their internet connection. Only very organizations use cables as the medium for internet traffic. These wireless networks mostly have a network security key ...
Where is the Change adapter option?
Once in the network connections window, click the option of “ Change adapter options ” present at the top right side of the screen.
What Is a Network Security Key?
Every secured network will have a network security key, but not every network uses the same security.
Where is the network key on a Mac?
On Mac, the network key is located in Keychain Access. Here's how you can find it. Select Go and select Utilities, then select Keychain Access . Select login, and scroll through the list of network connections to find your active network.
How to get SSID on iPhone?
Press the CMD and Space keys on your Mac to open the Searchlight utility. In the search field, type keychain access and press Enter . Type the name of your Wi-Fi network (the SSID), then double click on the SSID. Select the Show Password checkbox.
How to show characters in network?
In the Network Connections window, right click on the active Wi-Fi network adapter and select Status . In the Wi-Fi Status window, select Wireless Properties. This will open the Wireless Network Properties window. Select the Security tab, and enable the Show characters checkbox under the Network security key field.
How to find my wifi password on my PC?
The easiest way to find your Wi-Fi password is if you've already connected to the network with your Windows 10 PC. Click the Start menu, and type Network Status. Select the Network status system settings utility. In the Network Status window, select Change adapter options .
What is WPA2 security?
WPA2 (Wi-Fi Protected Access 2): Uses a security protocol with pre-shared key (PSK) authentication. In the case of enterprise users, WPA2 uses an enterprise authentication server. You can check which security method is currently enabled, and find your network security key, by accessing your router.
How to see wifi password without root?
Once you're connected to your Android, you can access and view the contents of the wpa_supplicant.conf file to see your stored Wi-Fi password.
What is 802.1x encryption?
802.1X is an IEEE standard framework for encrypting and authenticating a user who is trying to associate to a wired or wireless network. WPA-Enterprise uses TKIP with RC4 encryption, while WPA2-Enterprise adds AES encryption.
What is WPA2 Enterprise?
WPA2-Enterprise with 802.1X authentication is configured to use a customer-hosted on-premises Custom RADIUS server. The RADIUS server must be configured to allow authentication requests from the IP addresses of the Meraki access points.
How to associate to a wireless network?
To associate to a wireless network, a client must have the correct encryption keys (association requirements). Once associated the wireless client may need to enter information (network sign-on method) before accessing resources on the wireless network. The combinations of encryption and authentication methods that are supported are as follows:
What is 802.1x EAP?
802.1X utilizes the Extensible Authentication Protocol (EAP) to establish a secure tunnel between participants involved in an authentication exchange. The MR supports multiple EAP types, depending on whether the network is using a Meraki-hosted authentication server or a customer-hosted authentication server. The following table shows the EAP types supported by the MR access points:
What is MAC based access control?
MAC-based access control admits or denies wireless association based on the connecting device’s MAC address. When a wireless device attempts to associate, the Meraki AP queries a customer-premise RADIUS server with an Access-Request message. The RADIUS server can admit or deny the device based on the MAC address, responding to the Meraki AP with either an Access- Accept message or an Access-Reject message, respectively.
Which is stronger, WPA2 or WEP?
WPA- and WPA2-Personal (Wi-Fi Protected Access) use stronger encryption than WEP. (WPA-Personal uses TKIP with RC4 encryption, while WPA2- Personal uses AES encryption.) WPA2-Personal is preferred. Though it requires some client-side configuration, a PSK is relatively easy to configure.
Why does WPA2 require identity?
WPA2-Enerprise requires a identity source in order to authenticate users when they connect to the network. The Access points each interface with the identity source at time of the client association. Below are the identiity sources that can be used with WPA2-Enterprise.
What is a wireless security key?
A wireless network security key is the password required to be able to connect your PC to a secured access point (ex: router) on a wireless network. This tutorial will show you different ways on how to find the security key password of your wireless network connection in Windows 10. Contents.
Where is the security key on my router?
If you have not changed the security key in your router's wireless settings, or have reset your router back to default, then some wireless router manufacturers set a default security key or password which may be on the bottom of your router or in the router’s documentation. Look for the following terms:
How to check network security key?
(see screenshot below) 3 Click/tap on the Wireless Properties button. (see screenshot below) 4 Click/tap on the Security tab, and check the Show characters box under Network security key to be able to see it. (see screenshot below)
What is a wireless profile?
A wireless (Wi-Fi) network profile contains the SSID (network name), password key, and security information to be able to connect to a wireless network.
How many characters are needed for a WPA2 password?
But it is also crucial to set a solid password for your network. WPA and WPA2 protocols let you set passwords of up to 63 characters. Make your password hard to break by using special characters, lower and uppercase letters and numbers, avoid simple dictionary words.
What is the main vulnerability of WPA2?
At this time the main vulnerability to a WPA2 system is when the attacker already has access to a secured WiFi network and can gain access to certain keys to perform an attack on other devices on the network. This being said, the security suggestions for the known WPA2 vulnerabilities are mostly significant to the networks of enterprise levels, and not really relevant for small home networks.
How does WPA3 protect against dictionary attacks?
WPA3 will protect against dictionary attacks by implementing a new key exchange protocol. WPA2 used an imperfect four-way handshake between clients and access points to enable encrypted connections; it’s what was behind the notorious KRACK vulnerability that impacted basically every connected device. WPA3 will ditch that in favor of the more secure — and widely vetted — Simultaneous Authentication of Equals handshake.
What is WPA Enterprise?
Most modern WPA applications use a pre-shared key (PSK), most often referred to as WPA Personal, and the Temporal Key Integrity Protocol or TKIP (/tiːˈkɪp/) for encryption. WPA Enterprise uses an authentication server for keys and certificates generation.
How long does it take to break into a WPA2 network?
And even though breaking into a WPA/WPA2 secured network through this hole will take anywhere around 2 to 14 hours it is still a real security issue and WPS should be disabled and it would be good if the access point firmware could be reset to a distribution not supporting WPS to entirely exclude this attack vector.
When was 802.11i introduced?
The 802.11i wireless security standard based protocol was introduced in 2004. The most important improvement of WPA2 over WPA was the usage of the Advanced Encryption Standard (AES). AES is approved by the U.S. government for encrypting the information classified as top secret, so it must be good enough to protect home networks.
When did WPA2 come out?
When WPA2 came along in 2004, the Internet of Things had not yet become anything close to the all-consuming security horror that is its present-day hallmark. No wonder, then, that WPA2 offered no streamlined way to safely onboard these devices to an existing Wi-Fi network. And in fact, the predominant method by which that process happens today — Wi-Fi Protected Setup — has had known vulnerabilities since 2011. WPA3 provides a fix.

Wired Encryption Privacy Or Wired Encryption Protocol
- Encryption Type
1. 64-bit: This configuration requires a ten character password when you use a hexadecimal (zero to nine and A-F) digits or eight characters when you use ASCII characters. 2. 128-bit: This configuration requires a 26 character password when you use hexadecimal digits or 14 characte… - Advantages
1. Easy to configure. 2. Widely supported security system. 3. Secures your wireless network better than no encryption at all.
Wi-Fi Protected Access
- Encryption Type
1. TKIP: Temporal Key Integrity Protocol 2. PSK: Pre-shared Key or Personal mode. 256-bit encryption that requires a 64 hexadecimal digit password or a 8 - 63 ASCII character passphrase. 3. EAP: Extensible Authentication Protocol - Advantages
1. Easy to configure. 2. Strong encryption. 3. Easy to manage.
Wi-Fi Protected Setup
- Advantages
1. Automatically configures a wireless network with a network name (SSID) and a strong WPA security key for authentication and data encryption. 2. Supports various Wi-Fi certified 802.11 products, ranging from access points, wireless adapters, Wi-Fi phones, and other electronic devi… - Disadvantages
1. Ad-Hoc mode where wireless devices communicate directly to each other without an access point is not supported. 2. All of the Wi-Fi devices on the network must be WPS certified or compatible, otherwise you won't be able to take advantage of the ease in securing the network. …
Wireless Encryption Methods
I Don't Know What My Key is. How Do I Connect to The Wireless Network?
Accessing The Router Configuration
Logging Into The Router as An Administrator
Viewing and Changing The Encryption Key
- Every router's configuration interface is different. Below is an example of how a router's setup may appear. In your router's configuration interface, look for a section called Wireless, or something similar. You're looking for the page where you can change the wireless network's configuration, including its SSID name and authentication key. If you...
Verify You Can Connect to The Wireless Network