TCP/IP Suite layer Transport Layer: - TCP/IP Suite includes two protocol at this layer, the transmission control protocol and the user datagram protocol These protocol provides connection or connectionless data transfer services.
Full Answer
Which two protocols operate at the highest layer of TCP/IP protocol stack?
(Choose two.) Which two protocols operate at the highest layer of the TCP/IP protocol stack? (Choose two.) The application layer is the top layer of the TCP/IP protocol stack. Application layer protocols include HTTP, DNS, HTML, TFTP, POP, IMAP, FTP, and SMTP.
How is the TCP/IP suite organized?
This functionality is organized into four abstraction layers and each protocol in the suite resides in a particular layer. The TCP/IP suite is named after its most important protocols, the Transmission Control Protocol (TCP) and the Internet Protocol (IP). Some of the protocols included in the TCP/IP suite are:
Which layer gives TCP/IP its last two letters?
The most widely known protocol in this layer gives TCP/IP its last two letters. IP is a connectionless protocol, meaning that it provides no guarantee that packets are sent or received in the right order, along the same path, or even in their entirety. Reliability is handled by other protocols in the suite, such as in the transport layer.
What are the TCP/IP protocols?
The TCP/IP suite is named after its most important protocols, the Transmission Control Protocol (TCP) and the Internet Protocol (IP). Some of the protocols included in the TCP/IP suite are: ARP (Address Resolution Protocol) – used to convert an IP address to a MAC address.

Which two protocols operate at the top layer of TCP IP?
The Routing Information Protocol (RIP) and the Router Discovery Protocol (RDISC) are two routing protocols for TCP/IP networks.
Which two protocols operate at the top layer of the Tcpap protocol suite choose two?
ARP and PPP are network access layer protocols, and NAT is an internet layer protocol in the TCP/IP protocol suite.
What 2 protocols are at the transport layer in TCP IP?
The two most important protocols in the Transport Layer are Transmission Control Protocol (TCP) and User Datagram Protocol (UDP).
What are the four layers of the TCP IP suite?
4 The TCP/IP Protocol Stack is made up of four primary layers: the Application, Transport, Network, and Link layers (Diagram 1). Each layer within the TCP/IP protocol suite has a specific function.
Which services are provided by the Internet layer of the TCP IP protocol suite choose three?
Answers Explanation & Hints: DNS, DHCP, and FTP are all application layer protocols in the TCP/IP protocol suite.
What are two features of protocols used within the TCP IP protocol stack?
TCP and UDP destination port numbers are dynamically generated by the sending device in order to track the responses to requests. TCP mechanisms retransmit data when an acknowledgment is not received from the destination system within a set period of time.
How many protocols are in the TCP IP suite?
The 4 layers of the TCP/IP model Its protocols include HTTP, FTP, Post Office Protocol 3, Simple Mail Transfer Protocol and Simple Network Management Protocol. At the application layer, the payload is the actual application data.
What are the four layers of the TCP IP model quizlet?
- 4 layers: Application, Transport, Internet, & Network Interface layers.
What are two characteristics of the application layer of the TCP IP model?
Explanation: The application layer of the TCP/IP model is the layer that is closest to the end user, providing the interface between the applications. It is responsible for formatting, compressing, and encrypting data, and is used to create and maintain dialog between source and destination applications.
Which three protocols operate at the application layer of the TCP IP model?
Application Layer protocol:-TELNET: Telnet stands for the TELetype NETwork. ... FTP: FTP stands for file transfer protocol. ... TFTP: ... NFS: ... SMTP: ... LPD: ... X window: ... SNMP:More items...•
Which two protocols operate at the transport layer of the OSI model?
Transport layer protocols, namely, Transmission Control Protocol (TCP) and User Datagram Protocol (UDP), identify applications communicating with each other by means of port numbers.
Which two protocols may Devices use in the application?
IP address.Internet Protocol Suite.
Which three protocols operate at the application layer?
Application Layer Protocols (DNS, SMTP, POP, FTP, HTTP) Study Notes.
What layer of the TCP IP suite makes sure that all the data packets of a message arrive safely at the destination?
What layer of the TCP/IP suite makes sure that all the data packets of a message arrive safely at the destination? Explanation: The transport layer is responsible for managing the delivery of packets.
What is the principal protocol used to stream data across an IP network?
Principal protocol used to stream data across an IP network. The Transmission Control Protocol ( TCP) is one of the main protocols of the Internet protocol suite. It originated in the initial network implementation in which it complemented the Internet Protocol (IP). Therefore, the entire suite is commonly referred to as TCP/IP.
How does TCP sequence work?
TCP uses a sequence number to identify each byte of data. The sequence number identifies the order of the bytes sent from each computer so that the data can be reconstructed in order , regardless of any packet reordering, or packet loss that may occur during transmission. The sequence number of the first byte is chosen by the transmitter for the first packet, which is flagged SYN. This number can be arbitrary, and should, in fact, be unpredictable to defend against TCP sequence prediction attacks .
How does TCP work?
TCP uses a number of mechanisms to achieve high performance and avoid congestion collapse, where network performance can fall by several orders of magnitude. These mechanisms control the rate of data entering the network, keeping the data flow below a rate that would trigger collapse.
Why does TCP use flow control?
TCP uses an end-to-end flow control protocol to avoid having the sender send data too fast for the TCP receiver to receive and process it reliably. Having a mechanism for flow control is essential in an environment where machines of diverse network speeds communicate. For example, if a PC sends data to a smartphone that is slowly processing received data, the smartphone must regulate the data flow so as not to be overwhelmed.
What is a 16 bit checksum?
The 16-bit checksum field is used for error-checking of the TCP header, the payload and an IP pseudo-header. The pseudo-header consists of the source IP address, the destination IP address, the protocol number for the TCP protocol (6) and the length of the TCP headers and payload (in bytes).
What is cumulative acknowledgment protocol?
In a pure cumulative acknowledgment protocol, the receiver can only send a cumulative ACK value of 2,000 (the sequence number immediately following the last sequence number of the received data) and cannot say that it received bytes 3,000 to 10,999 successfully. Thus the sender may then have to resend all data starting with sequence number 2,000.
What is the maximum segment size?
The maximum segment size (MSS) is the largest amount of data, specified in bytes, that TCP is willing to receive in a single segment. For best performance, the MSS should be set small enough to avoid IP fragmentation, which can lead to packet loss and excessive retransmissions. To try to accomplish this, typically the MSS is announced by each side using the MSS option when the TCP connection is established, in which case it is derived from the maximum transmission unit (MTU) size of the data link layer of the networks to which the sender and receiver are directly attached. Furthermore, TCP senders can use path MTU discovery to infer the minimum MTU along the network path between the sender and receiver, and use this to dynamically adjust the MSS to avoid IP fragmentation within the network.
When is TCP preferred?
TCP is the preferred protocol when a function requires lower network overhead.
What is an advantage to using a protocol that is defined by an open standard?
An open standard protocol is not controlled or regulated by standards organizations.
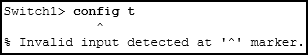
What happens when the transport input ssh command is entered on the switch vty lines?
The switch requires a username/password combination for remote access.
How does the service password-encryption command enhance password security on Cisco routers and switches?
It requires encrypted passwords to be used when connecting remotely to a router or switch with Telnet.
What characteristic describes antispyware?
a tunneling protocol that provides remote users with secure access into the network of an organization
What is one main characteristic of the data link layer?
It generates the electrical or optical signals that represent the 1 and 0 on the media.
What does DHCPv6 request do?
It must send a DHCPv6 INFORMATION-REQUEST message to request the address of the DNS server. It must send a DHCPv6 REQUEST message to the DHCPv6 server to request permission to use this address. It must send an ICMPv6 Neighbor Solicitation message to ensure that the address is not already in use on the network.
What are the protocols used in TCP/IP?
The TCP/IP suite is named after its most important protocols, the Transmission Control Protocol (TCP) and the Internet Protocol (IP). Some of the protocols included in the TCP/IP suite are: 1 ARP (Address Resolution Protocol) – used to associate an IP address with a MAC address. 2 IP (Internet Protocol) – used to deliver packets from the source host to the destination host based on the IP addresses. 3 ICMP (Internet Control Message Protocol) – used to detects and reports network error conditions. Used in ping. 4 TCP (Transmission Control Protocol) – a connection-oriented protocol that enables reliable data transfer between two computers. 5 UDP (User Datagram Protocol) – a connectionless protocol for data transfer. Since a session is not created before the data transfer, there is no guarantee of data delivery. 6 FTP (File Transfer Protocol) – used for file transfers from one host to another. 7 Telnet (Telecommunications Network) – used to connect and issue commands on a remote computer. 8 DNS (Domain Name System) – used for host names to the IP address resolution. 9 #N#HTTP (Hypertext Transfer Protocol) – used to transfer files (text, graphic images, sound, video, and other multimedia files) on the World Wide Web.
What is the name of the protocol used to associate an IP address with a MAC address?
Some of the protocols included in the TCP/IP suite are: ARP (Address Resolution Protocol) – used to associate an IP address with a MAC address.
What is UDP protocol?
UDP (User Datagram Protocol) – a connectionless protocol for data transfer. Since a session is not created before the data transfer, there is no guarantee of data delivery. FTP (File Transfer Protocol) – used for file transfers from one host to another.
What is the name of the protocol used to transfer files between computers?
DNS (Domain Name System) – used for host names to the IP address resolution. HTTP (Hypertext Transfer Protocol) – used to transfer files (text, graphic images, sound, video, and other multimedia files) on the World Wide Web.
What is the difference between IP and ICMP?
IP (Internet Protocol) – used to deliver packets from the source host to the destination host based on the IP addresses. ICMP (Internet Control Message Protocol) – used to detects and reports network error conditions. Used in ping.
