
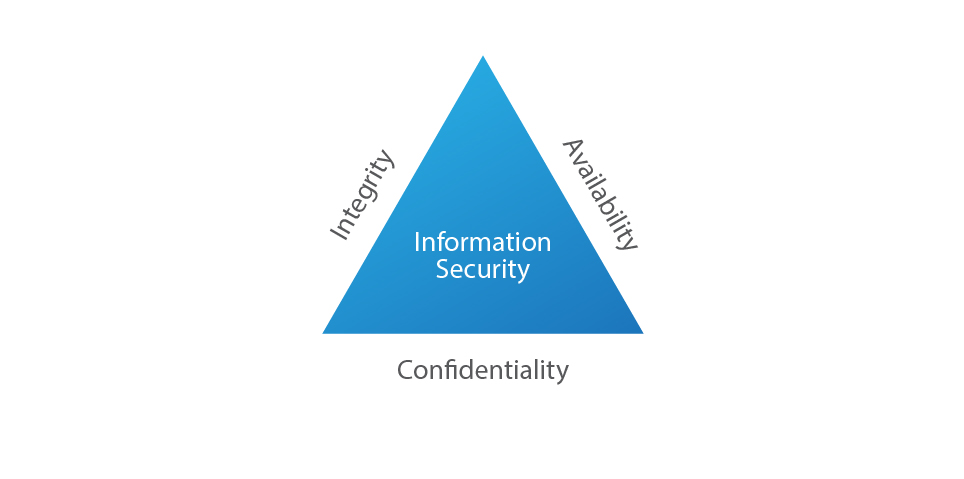
Information security is considered as safeguarding three main objectives:
- Confidentiality: Data and information assets must be confined to people who have authorized access and not disclosed to others
- Integrity: Keeping the data intact, complete and accurate, and IT systems operational
- Availability: An objective indicating that information or system is at disposal of authorized users when needed.
What are the principles of information security?
Information security principles The basic components of information security are most often summed up by the so-called CIA triad: confidentiality, integrity, and availability.
What are the basics of computer security?
The key concept of Cyber Security?
- Confidentiality. It defines the rules that limit access to information. ...
- Integrity. This assures that the data is consistent, accurate, and trustworthy over its time period. ...
- Availability. Availability in terms of all necessary components like hardware, software, networks, devices, and security equipment should be maintained and upgraded.
What are the basics of security?
and Social Security Disability Insurance (SSDI). These initiatives provide financial assistance for senior citizens and those living with disabilities. SSI is designed to provide basic financial ...
What are basic security concepts?
Basic Security Concepts . Three basic security concepts important to information on the internet are confidentiality, integrity, and availability. Concepts relating to the people who use that information are authentication, authorization, and nonrepudiation. When information is read or copied by someone not authorized to do so, the result is ...

What are the three aspects of information security?
The CIA triad refers to an information security model made up of the three main components: confidentiality, integrity and availability.
What are the 4 aspects of security?
An effective security system comprises of four elements: Protection, Detection, Verification & Reaction. These are the essential principles for effective security on any site, whether it's a small independent business with a single site, or a large multinational corporation with hundreds of locations.
What is the two major aspects of information security?
While confidentiality, integrity, and authenticity are the significant concerns of an information security manager, privacy is the essential aspect of information security for web users. Authenticity − Authentication defines that users are who they request to be.
What are the 5 components of information security?
It relies on five major elements: confidentiality, integrity, availability, authenticity, and non-repudiation.
What is the main aspect of security?
It includes the protection of the hardware, software, and all the associated interfaces of the system. Some common security requirements include managing user accounts, controlling passwords and system access.
What is the most important aspect of security?
Visibility, mitigation, prioritization, and encryption — these are the most important elements to security right now.
What are the two aspects of information privacy?
There are two categories of technology to address privacy protection in commercial IT systems: communication and enforcement.
What are the technical aspect of implementation in information security?
Physical security Shredding paper records. Locking office doors. Implementing access control using key cards or biometrics. Using video surveillance.
What are the three types of security?
There are three primary areas or classifications of security controls. These include management security, operational security, and physical security controls.
What are the different types of information security?
What Are the Types of Information Security?Application Security. ... Cloud Security. ... Cryptography. ... Infrastructure Security. ... Incident Response. ... Vulnerability Management. ... Phishing. ... Brute-Force Attacks.More items...•
What is information security?
Information security is a broader category of protections, covering cryptography, mobile computing, and social media. It is related to information assurance, used to protect information from non-person-based threats, such as server failures or natural disasters.
What is the goal of infrastructure security?
Due to this, an important goal of infrastructure security is to minimize dependencies and isolate components while still allowing intercommunications. Cloud security.
What is Infosec?
Information security (InfoSec): The Complete Guide. Information security (InfoSec) enables organizations to protect digital and analog information. InfoSec provides coverage for cryptography, mobile computing, social media, as well as infrastructure and networks containing private, financial, and corporate information.
What is the purpose of Infosec?
The main objectives of InfoSec are typically related to ensuring confidentiality, integrity, and availability of company information.
Why is Infosec important?
Authored by Exabeam. Information security (InfoSec) is critical to ensuring that your business and customer information is not manipulated, lost, or compromised. Information security practices can help you secure your information, ensuring that your secrets remain confidential and that you maintain compliance.
What is security operations?
Security operations —includes real-time monitoring, analysis, and triage of threats. Cyber risk and cyber intelligence —includes maintaining current knowledge of security threats and keeping executive and board teams informed of the potential impacts of risks.
What is the purpose of encryption?
Cryptography. Cryptography uses a practice called encryption to secure information by obscuring the contents. When information is encrypted, it is only accessible to users who have the correct encryption key. If users do not have this key, the information is unintelligible.
What is information security?
Information security consists of various practices and sub-disciplines. It aims to keep your data from unauthorized access and maintain its integrity , hinder any malware from rooting in your devices and networks, retain the important information when needed, provide a smooth and safe flow of information between networks and devices, ...
Why is information security important?
That is why, information security practices are more important than ever. As of today, many experts would agree that information is the most valuable asset a company can have. As a result, hundreds of attacks targeting companies from various industries happen every day. Information security measures aim to protect companies from a diverse set ...
Why is availability important in a CIA triad?
Availability gains additional importance because of the malicious attacks that aim to hinder authorized users from accessing the data. In addition to the CIA Triad, there are two additional components of the information security: Authenticity and accountability. Authenticity refers to the state of being genuine, verifiable or trustable.
What does integrity mean in a document?
It means that the information is visible to the authorized eyes only. Keeping the information from unauthorized viewers is the first step to the information security. This component gains importance especially in fields that deal with sensitive information like social security numbers, addresses and such. Integrity means the ‘originality’ of the ...
What is integrity in science?
Integrity means the ‘originality’ of the information. This component aims to make sure that the information is intact and unaltered. As a result, assuring that the information is not altered by mistake, malicious action or even a natural disaster falls within the scope of integrity.
What happens when you fail to protect your data?
When the measures you take to keep your data safe fail to protect you, a data breach happens. In other words, an outsider gains access to your valuable information. As a consequence, your company may lose business or hard earned trust of the public. Hence, keeping your data safe is keeping your company safe and information security procedures are ...
What is the definition of confidentiality?
Confidentiality refers to the concealment. It means that the information is visible to the authorized eyes only.
The Importance of Information Security
Organizations have recognized the importance of having roadblocks to protect the private information from becoming public, especially when that information is privileged. The 2017 Cybersecurity Trends Report provided findings that express the need for skilled information security personnel based on current cyberattack predictions and concerns.
Jobs In Information Security
Interested in being a part of an information security team but unsure of where your skills could be best used? Exploring the different types of jobs available in information security can help you find an IT occupation that not only interests you but will put your information security expertise to the test. The salaries noted, courtesy of the U.S.
Information Security Principles
The NIST said data protections are in place "in order to ensure confidentiality, integrity, and availability" of secure information. These principles, aspects of which you may encounter daily, are outlined in the CIA security model and set the standards for securing data.
How to Get Into Information Security
While a bachelor's degree is usually needed, (like a bachelor's in computer science or information security degree for example) to work as an information security analyst, some employers also prefer analysts with an MBA in IT. Gaining experience as a computer or networks systems administrator is also attractive to many businesses, according to BLS.
What is information security?
Information security system is the process of protecting and securing the data from unauthorized access, disclosure, destruction or disruption. An organization that attempt to compose a operating ISP must have well-defined objectives regarding security And strategy.
What is the foremost necessary factor that a security skilled should bear in mind?
The foremost necessary factor that a security skilled should bear in mind is that his knowing. The protection management practices would allow him to include them into the documents. He’s entrusted to draft, and that could be a guarantee for completeness, quality and work ability.
What is the meaning of integrity in IT?
Keeping the information intact, complete and correct, and IT systems operational; Integrity is the trustworthiness of data or resources in the prevention of improper and unauthoriz changes the assurance that information is sufficiently accurate for its purpose.
What are the measures to maintain data integrity?
Measures to maintain data integrity may include a checksum (a number produced by a mathematical function to verify that a given block of data is not changed) and access control (which ensures that only the authorized people can update, add, and delete data to protect its integrity).
What is security policy?
It means inferior workers is typically certain to not share the small quantity of data they need unless explicitly approved. Conversely, a senior manager might have enough authority to create a choice what information is shared and with whom, which implies that they’re not tied down by an equivalent data security policy terms. That the logic demands that ISP ought to address each basic position within the organization with specifications which will clarify their authoritative standing. Authenticity refers to the characteristic of a communication, document, or any data that ensures the quality of being genuine or corrupted. The major role of authentication is to confirm that a user is genuine, one who he / she claims to be. Controls such as bio metrics, smart cards, and digital certificates ensure the authenticity of data, transactions, communications, or documents.
What is the role of authentication?
The major role of authentication is to confirm that a user is genuine, one who he / she claims to be. Controls such as bio metrics, smart cards, and digital certificates ensure the authenticity of data, transactions, communications, or documents. The user should prove access rights and identity.
What is the definition of confidentiality?
1. Confidentiality. Data and information assets should be confine to individuals license to access and not be disclose to others; I Confidentiality assurance that the information is accessible those who are authorize to have access. Confidentiality breaches may occur due to improper data handling or a hacking attempt.
What is information security?
Information Security is basically the practice of preventing unauthorized access, use, disclosure, disruption, modification, inspection, recording or destruction of information. Information can be physical or electronic one. Information can be anything like Your details or we can say your profile on social media, your data in mobile phone, ...
What does confidentiality mean in email?
Confidentiality – means information is not disclosed to unauthorized individuals, entities and process. For example if we say I have a password for my Gmail account but someone saw while I was doing a login into Gmail account. In that case my password has been compromised and Confidentiality has been breached.
What does authenticity mean in a message?
Authenticity – means verifying that users are who they say they are and that each input arriving at destination is from a trusted source.This principle if followed guarantees the valid and genuine message received from a trusted source through a valid transmission.
What is the purpose of information security?
Information security is considered as safeguarding three main objectives: Confidentiality: Data and information assets must be confined to people who have authorized access and not disclosed to others. Integrity: Keeping the data intact, complete and accurate, and IT systems operational.
What is information security policy?
Share: An information security policy is a set of rules enacted by an organization to ensure that all users of networks or the IT structure within the organization’s domain abide by the prescriptions regarding the security of data stored digitally within the boundaries the organization stretches its authority.
What is the most important thing a security professional should remember?
The most important thing that a security professional should remember is that his knowledge of the security management practices would allow him to incorporate them into the documents he is entrusted to draft. That is a guarantee for completeness, quality and workability.
What is the purpose of an organization that strives to compose a working information security policy?
An organization that strives to compose a working information security policy needs to have well-defined objectives concerning security and strategy. Management must agree on these objectives: any existing disagreements in this context may render the whole project dysfunctional.
Why do institutions create information security policies?
Institutions create information security policies for a variety of reasons: To establish a general approach to information security. To detect and forestall the compromise of information security such as misuse of data, networks, computer systems and applications.
What is the importance of sharing security policies with staff?
Sharing IT security policies with staff is a critical step. Making them read and acknowledge a document does not necessarily mean that they are familiar with and understand the new policies. On the other hand , a training session would engage employees and ensure they understand the procedures and mechanisms in place to protect the data.
What is a data classification policy?
A data classification policy may arrange the entire set of information as follows: High Risk class: Data protected by state and federal legislation (the Data Protection Act, HIPAA, FERPA) as well as financial, payroll and personnel (privacy requirements) are included here.
What Is Information Security?
Why Is Information Security Important?
- Companies and institutions from all sectors and of all sizes collect impressive amounts of data in order to operate smoothly, provide a better service and compete with others. In such an environment, being able to keep this data safe is as important as being able to gather it. That is why, information security practices are more important than ever. As of today, many experts wo…
What Are The 5 Components of Information Security?
- Information security consists of various practices and sub-disciplines. It aims to keep your data from unauthorized access and maintain its integrity, hinder any malware from rooting in your devices and networks, retain the important information when needed, provide a smooth and safe flow of information between networks and devices, and keep your n...