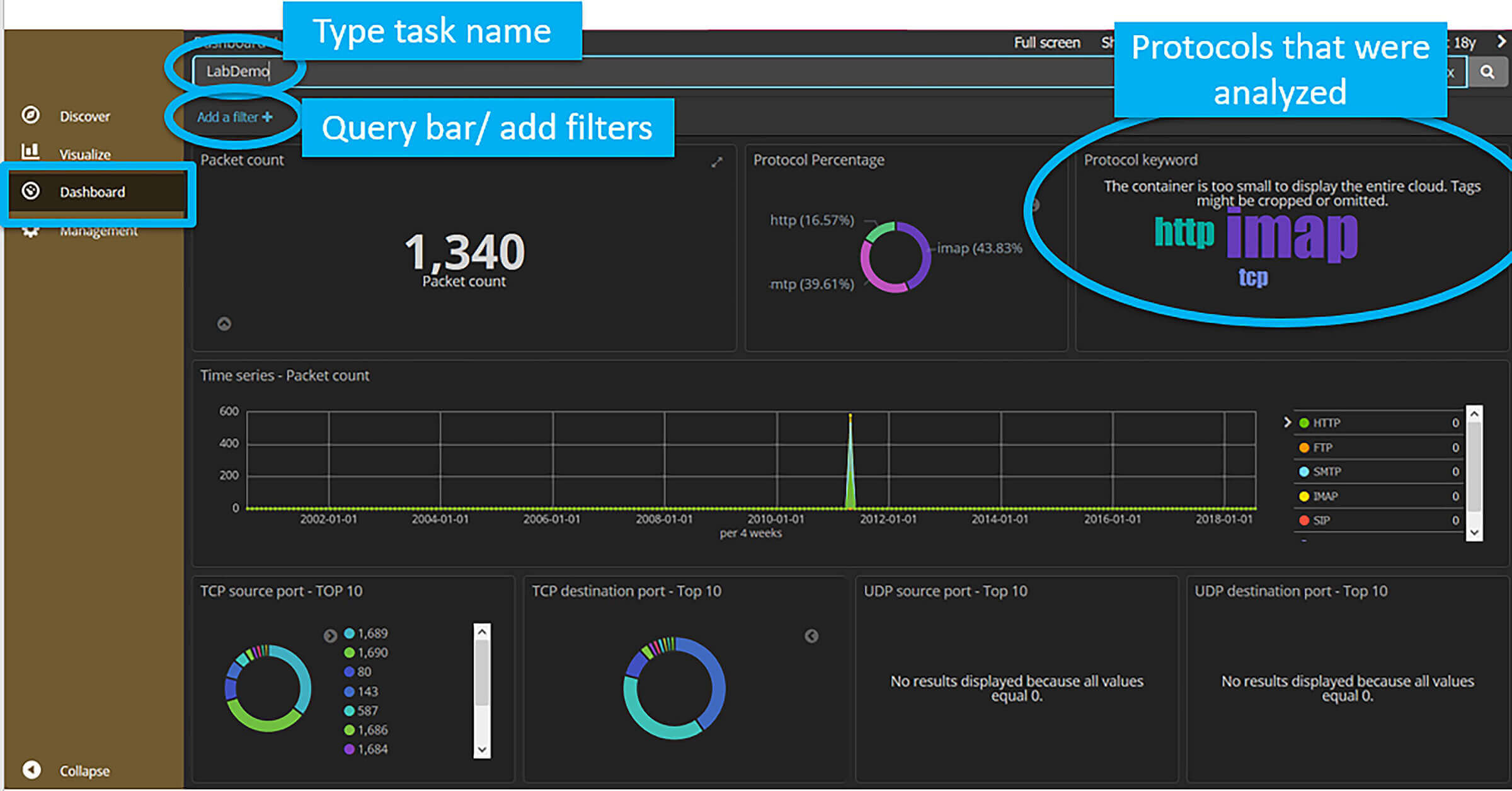
Network Forensics Tools
- tcpdump. Tcpdump is a popular command line tool available for capturing and analyzing network traffic primarily on Unix based systems.
- Wireshark. It would be a surprise if someone worked in the Cyber Security field and not heard of the tool Wireshark.
- Network Miner. ...
- Splunk. ...
- Snort. ...
Full Answer
What are the best network forensics tools?
In this section, let us go through the Network Forensics tools mentioned earlier. Tcpdump is a popular command line tool available for capturing and analyzing network traffic primarily on Unix based systems. Using tcpdump, we can capture the traffic and store the results in a file that is compatible with tools like Wireshark for further analysis.
What are forensics tools used for in criminal investigation?
Forensic tools help investigators to extract crucial pieces of evidence from electronic devices to be presented in a court of law to put the criminals behind bars. Disclaimer: – The tools mentioned in the list have been extensively used by investigators across the world.
What is network forensics and how does it work?
There are two main applications for network forensics. The first is security, which entails analyzing a network for unusual traffic. An attacker may be able to delete all system logs on a target computer. They leave the network-based proof as the sole forensic evidence accessible.
What are the most commonly used offensive network security tools?
There are several offensive network security tools commonly used by security professionals. NMAP, Metasploit, OWASP ZAP are some of the most commonly used freely available tools.

What is network forensic tools?
Network forensic tools enable security professionals to monitor network performance and compromises. These tools are used to monitor internal and external network attacks. Technological improvements have enabled criminals to wipe out tracks of cybercrime to elude alterations.
Which is network forensic analyst tool?
Network Forensic Analysis Tools (NFATs) help administrators monitor their environment for anomalous traffic, perform forensic analysis and get a clear picture of their environment. To gain a better definition of the tool, it examines three NFATs: SilentRunner, NetIntercept and NetDetector.
Which tool is used for forensic imaging?
Autopsy and the Sleuth Kit are likely the most well-known forensics toolkits in existence. The Sleuth Kit is a command-line tool that performs forensic analysis of forensic images of hard drives and smartphones. Autopsy is a GUI-based system that uses The Sleuth Kit behind the scenes.
What is the tool used for network based evidence collection?
Routers, Firewalls and proxy logs Routers are used to route the traffic from one network to another and they are the most commonly used devices in enterprise networks and they often contain many features that are of interest during a network forensic investigation.
What is the process of network forensic?
Network Forensics examinations have seven steps including Identification, Preservation, Collection, Examination, Analysis, and Presentation and Incident Response. Identification process has a huge impact on the following steps as this step is the path to the conclusion of the case.
Why is network forensics useful?
Network forensics is necessary in order to determine the type of attack over a network and to trace the culprit. A proper investigation process is required to produce the evidence recovered during the investigation in the court of law.
What are the tools in criminal investigation?
Tools To establish facts and develop evidence, a criminal investigator must use these tools-information, interview, interrogation, and instrumentation.
What is the role of computer forensics tools?
Computer forensics is widely known for catching criminals in various types of fraud. However, investigators are now using computer forensics to catch murderers, and access encrypted data daily that will stand as evidence in a court of law.
What are the tools that the network administrator uses to manage the network that an investigator can use in an investigation?
General purpose tools tcpdump, wireshark/tshark and tstat are popular protocol analyzers. These tools are used to inspect recorded traffic. They can be either packet-centric or session-centric. Xplico and NetworkMiner are Network Forensic Analysis (NFAT) tools.
What are different types of network based evidence?
(1) Internet or the Network-based Evidence, (2) Stand-alone computers, (3) Stand-alone devices & (4) Mobile devices. The processes and tools involved in collection of all these types of digital evidence differs from each other and the types of crimes tend to be linked with one or other such device.
What is router forensics?
Router forensics include the techniques used to extract information about an event that occurred on a router. Routers perform the traffic directing functions on the Internet.
What is Internet forensic?
The investigation of criminal activity that has occurred on the Internet. It deals with the analysis of the origins, contents, patterns and transmission paths of email and Web pages as well as browser history and Web server scripts and header messages.
What tools are used for forensic investigations?
NMAP, Metasploit, OWASP ZAP are some of the most commonly used freely available tools. While these tools may not be directly helpful for forensic investigators, organizations often see attacks initiated by script kiddies, in which case having knowledge of these tools can help deriving some quick conclusions.
What is Wireshark tool?
Wireshark is an open-source tool available for capturing and analyzing traffic with support for applying filters using the graphical user interface. On the system, where Wireshark is running, one can choose the interface on which traffic needs to be captured.
What is tcpdump used for?
Tcpdump can either be used to do a quick packet capture for troubleshooting or for capturing traffic continuously in large volumes for future analysis. It is worth noting that tcpdump can be used to capture both layer 2 and layer 3 data.
What is nmap used for?
Nmap. Nmap is probably the most commonly used tool, especially during network security assessments. Nmap is often used to identify open ports, but it can also be used to perform vulnerability assessment to certain extent using the support for NSE scripts. In most cases, nmap is noisy, especially when scans are performed in large volumes.
What is metasploit used for?
Metasploit. Metasploit is an exploitation framework often used in penetration testing. It comes with several different modules and it consists of many popular exploits that can be used to exploit vulnerabilities in operating systems, web applications and other services accessible over the network.
What is a nmap?
Nmap is probably the most commonly used tool, especially during network security assessments. Nmap is often used to identify open ports, but it can also be used to perform vulnerability assessment to certain extent using the support for NSE scripts.
Is Wireshark a security tool?
Wireshark is more of a traffic capturing and analysis tool than an offensive network security tool, and it can greatly help during network forensic investigations.
What is network forensics?
Network Forensics. Network forensics is the study of data in motion, with special focus on gathering evidence via a process that will support admission into court. This means the integrity of the data is paramount, as is the legality of the collection process. Network forensics is closely related to network intrusion detection: ...
What is the primary activity of network forensics?
The primary activities of network forensics are investigative in nature. The investigative process encompasses the following:
What is NFA in cyber security?
Network forensics aim at finding out causes and impacts of cyber attacks by capturing, recording, and analyzing of network traffic and audit files [75 ]. NFA helps to characterize zero-day attacks and has the ability to monitor user activities, business transactions, and system performance. As a result, attack attribution, what attack methods and tactics were used and attack duration, can be analyzed and derived using NFA.
Why do analysts use different tools?
Because network forensics can be performed for many purposes with dozens of data source types, analysts may use several different tools on a regular basis, each well-suited to certain situations. Analysts should be aware of the possible approaches to examining and analyzing network traffic data and should select the best tools for each case, rather than applying the same tool to every situation. Analysts should also be mindful of the shortcomings of tools; for example, a particular protocol analyzer might not be able to translate a certain protocol or handle unexpected protocol data (illegal data field value). It can be helpful to have an alternate tool available that might not have the same deficiency.
What is computer forensics?
Traditionally, computer forensics has focused on file recovery and filesystem analysis performed against system internals or seized storage devices. However, the hard drive is only a small piece of the story. These days, evidence almost always traverses the network and sometimes is never stored on a hard drive at all.
What is traffic visualization?
Visualizing the traffic flows and the relationships among hosts. Some tools can even tie IP addresses, domain names, or other data to physical locations and produce a geographic map of the activity.
What are the primary objectives of digital forensics?
There are at least three distinct communities within digital forensics: law enforcement, military, and business and industry, each of which has its own objectives and priorities. For example, prosecution is the primary objective of the law enforcement agencies and their practitioners and is often done after the fact. Military operations' primary objective is to guarantee the continuity of services, which often have strict real-time requirements. Business and industry's primary objectives vary significantly, many of which want to guarantee the availability of services and put prosecution as a secondary objective.
What is network forensics?
Network forensics is a type of digital forensics which goal is to monitoring, correlate, examine and analysis of computer network traffic for various purposes like-information gathering, legal evidence, or intrusion detection.
What is a TCP/IP sniffer?
TCP/IP protocol stack. These sniffers capture th e packets exchanged in the Ethernet and allow
What tools help to reveal the browsing history of a website?
Web Historian [6] and Index.dat analyzer [7]. These tools help to reveal the browsing history of
What is a honey pot network?
a network to which no traffic should co me from outside. A network of Honey pots across the
Is email a tool for cybercrimes?
With the advent of information and communication technologies, e-mail is one of the prime tools for communication. Almost everyone uses emails for business communications as well as for sharing personal information. E-mail is vulnerable against cybercrimes. This chapter focuses on the basic concepts of web forensics and then provides an insight about the e-mailing policies, email architecture, and existing investigation techniques used by forensic investigators. Most of the organizations implement some standard e-mailing policies; however, it is not sufficient to handle and prevent the digital crimes. We need to monitor and investigate emails for proper check. This chapter discusses some prominent tools and techniques through which forensic experts can gather and analyze data about suspected email accounts for investigation and produce evidence in the court of law.
How many tools can forensics use?
It is an easy to use platform offering more than 150 forensic tools that investigators can use to analyze computer memory to discern actionable evidence. It features an interactive GUI and can be installed on flash drives or external hard drives to be used directly without any installation on the required device.
Why is forensic tool important?
Forensic tools help investigators to extract crucial pieces of evidence from electronic devices to be presented in a court of law to put the criminals behind bars. Disclaimer: – The tools mentioned in the list have been extensively used ...
How has forensics evolved?
The history of Forensics has evolved over decades through various branches of forensic science . Forensics have become an integral part of law enforcement activities across the globe. These applications are central to fighting cybercrime and protecting digital assets in the current age of the internet and advancing globalization. Crime can take many forms and it becomes necessary to gather evidence and obtain a conviction for perpetrators. Forensic tools help investigators to extract crucial pieces of evidence from electronic devices to be presented in a court of law to put the criminals behind bars.
Why are smartphones important in forensics?
In the era of mobile applications, smartphones are almost always vital sources of forensic evidence that highlight the digital paper trail for investigators to follow. Even though the actual crime may have been committed using other electronic devices, the intent and plan to commit the crime may have been discussed and shared among acquaintances.
What is X Ways Forensics?
X-Ways Forensics provides a large array of various types of tools that aid in digital forensics. From data recovery to disk cloning, finding and retrieving lost data, recovering deleted files and many more – X-Ways Forensics has grown to become an absolute must-have for all budding and professional cyber forensic analysts.
What is NetworkMiner used for?
It is used to analyze or even capture packets transferred on a network to detect devices and corresponding operating systems, names of hosts, open ports, etc. And the best part – activities using the NetworkMiner does not generate traffic on a network.
Why do criminals destroy evidence?
In the event of a crime, the perpetrators often try to destroy the evidence in order to escape justice. This is an extremely common occurrence in the case of cybercrimes. In such a scenario, it is deleted information on devices that help investigators nab the criminals and restore the damages. Few forensic tools can recover deleted information as well as ProDiscover Forensic. It lets people know if there have been any changes made to any files or stored data.
What is digital forensics?
Digital forensics tools can fall into many different categories, some of which include database forensics, disk and data capture, email analysis, file analysis, file viewers, internet analysis, mobile device analysis, network forensics, and registry analysis. Many tools fulfill more than one function simultaneously, ...
What is a wrapper in forensics?
Many tools fulfill more than one function simultaneously, and a significant trend in digital forensics tools are “wrappers”—one that packages hundreds of specific technologies with different functionalities into one overarching toolkit.
What is DFF software?
The DFF was developed with the three main goals of modularity (allowing for changes to the software by developers), scriptability (allowing for automation), and genericity (keeping the operating-system agnostic to help as many users as possible). The software is available for free on GitHub.
Who is the writer of Wireshark?
Writer. Matt Zbrog. Matt Zbrog is a writer and freelancer who has been living abroad since 2016.
Is a smoking gun a device?
Today’s smoking gun is more likely to be a laptop or a phone than it is a more literal weapon. Whether such a device belongs to a suspect or victim, the vast swathes of data these systems contain could be all an investigator needs to put together a case.
Is Autopsy open source?
Developed by the same team that created The Sleuth Kit, a library of command line tools for investigating disk images, Autopsy is an open source solution, available for free in the interests of education and transparency. The latest version is written in Java, and it is currently only available for Windows.
What is the most important forensic tool?
2. ProDiscover Forensic. It is one of the most significant Forensic Tool that will enable the computer to locate the data on the computer’s Hard Disk and will also protect the evidence it found and generate good quality of analyzed results for any legal procedures.
What is X-Ways forensic?
X-Ways Forensic is a very advanced working Tool that runs faster; recovers deleted files, potable. It also offers features as it runs on a USB stick on Windows Server.
What is Xplico sniffer?
Xplico is a networking Forensic Tool that reconstructs the contents with a packet sniffer like Netsniff-ng. it extracts and reconstructs all web pages that are generally lost.
What is a SANS toolkit?
SANS Investigative Forensic Toolkit (SIFT) is a Toolkit that is based on Ubuntu Server Live CD that contains a complete set of tools in which you wish to perform a rigorous forensic cybercrime or any incident responsive inquiry. This is a free available SIFT forensic toolkit that is similar to any advanced incident inquiry and a tool that suite is also an additional feature in the course of SANS’ Advanced Incident Response. It signifies that effective investigations and acknowledging to the intrusions is the only way to accomplish the cutting-edge and open-source-system tool that is easily out there and are often updated.
What is computer aided investigation environment?
Computer-Aided Investigative Environment is a Linux Live CD to meet up with the standards of forensic reliability. It is a semi-automated report generator to get the results in very less time. In the present version, CAINE is based on Linux and LightDM. It also has a user-friendly interface to work effectively.
What are the procedural rules for forensic investigators?
Generally, Forensic investigators usually follow a quality set of procedural rules like after physically isolating the electronic equipment in question is to make sure it should not be by chance corrupted, investigators make sure that a digital duplicate shared copy of that device is stored.
What is the purpose of forensics?
To point out all the hidden private details that area unit has left when or throughout an occurrence, then the forensics is employed. The aim of forensics methods is to look, preserve, and analyze the data in a very detailed form on a computer system to seek out a potential proof for an attempt.