My guess is:
- AWS access key ID is a form of unique user/account identifier
- AWS secret key is like private key
- When AWS CLI sends a API request, the payload is signed by generating an HMAC with the secret key as the key
- The HMAC, AccessKeyID and the payload is sent to AWS service
How to get AWS access key and secret key?
- Sign in to the AWS Management Console as the root user. ...
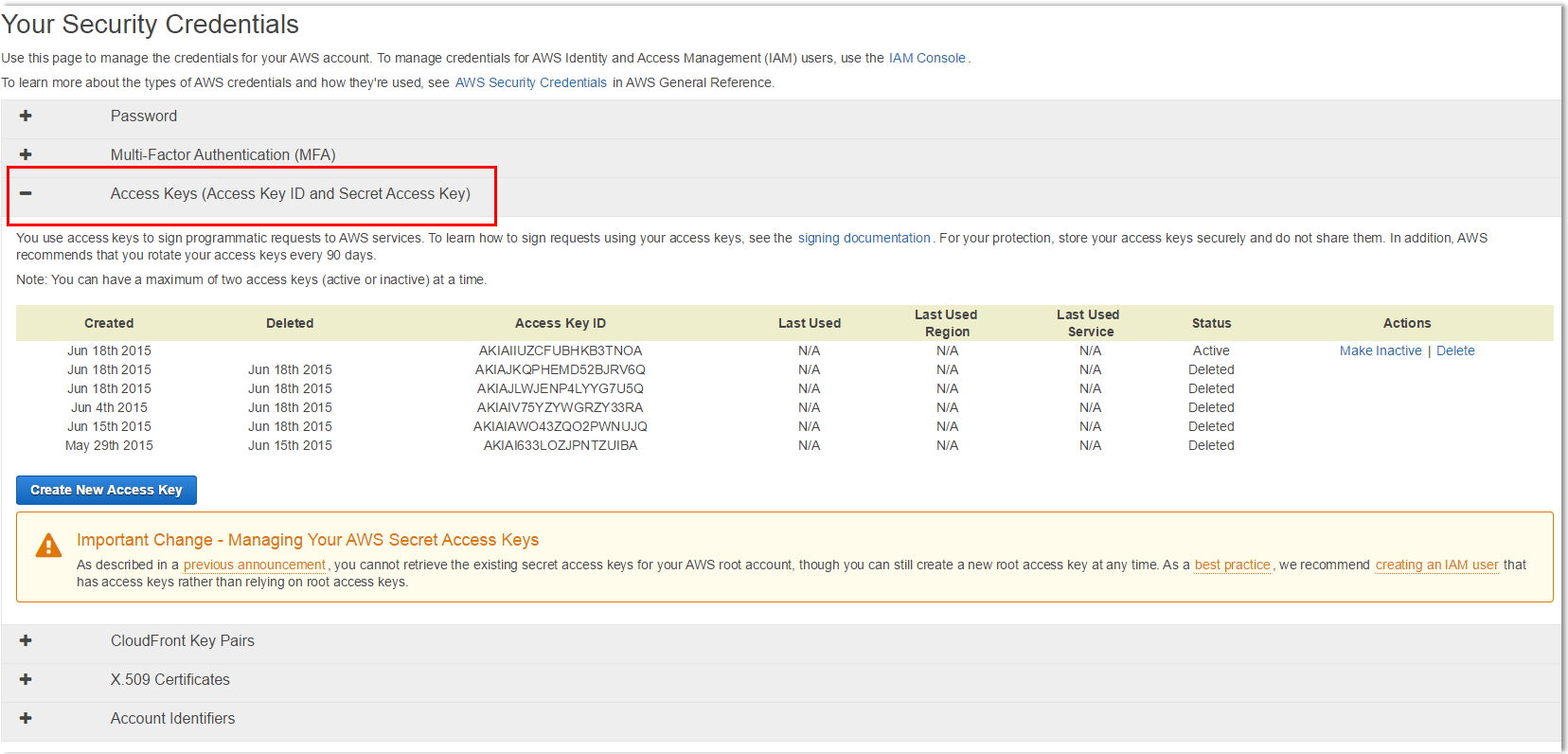
- In the navigation bar on the upper right, choose your account name or number and then choose My Security Credentials .
- Expand the Access keys (access key ID and secret access key) section.
- Do one of the following: To create an access key, choose Create New Access Key. ...
How to secure AWS?
When organizations adopt AWS services, the responsibility of security is shared between AWS and the customer. Regardless of the size of your organization, leveraging the expertise of an AWS Partner such as Cloud Comrade is a valuable way to increase your security posture.
How to configure AWS credentials?
- Open VS Code.
- To open the Command Palette, on the menu bar, choose View, Command Palette. Or use the following shortcut keys: Windows and Linux – Press Ctrl+Shift+P. ...
- Search for AWS and choose AWS: Create Credentials Profile.
- Enter a name for the initial profile.
- Enter the access key ID for the credentials. ...
- Enter the secret access key for the credentials. ...
How to switch user on the AWS CLI?
- Sign in to the AWS Management Console as an IAM user and open the IAM console at https://console.aws.amazon.com/iam/ .
- In the IAM console, choose your user name on the navigation bar in the upper right. ...
- Choose Switch Role. ...

What is AWS Secret access key?
Secret access keys are—as the name implies—secrets, like your password. For your own security, AWS doesn't reveal your password to you if you forgot it (you'd have to set a new password). Similarly, AWS does not allow retrieval of a secret access key after its initial creation.
Where is my AWS access key and secret key?
1 Go to Amazon Web Services console and click on the name of your account (it is located in the top right corner of the console). Then, in the expanded drop-down list, select Security Credentials. 2 Click the Continue to Security Credentials button. 3 Expand the Access Keys (Access Key ID and Secret Access Key) option.
What is S3 access key and secret key?
Access Keys are used to sign the requests you send to Amazon S3. Like the Username/Password pair you use to access your AWS Management Console, Access Key Id and Secret Access Key are used for programmatic (API) access to AWS services. You can manage your Access Keys in AWS Management Console.
How do I get the secret key and access key in AWS root?
Choose your account name in the navigation bar, and then choose My Security Credentials. If you see a warning about accessing the security credentials for your AWS account, choose Continue to Security Credentials. Expand the Access keys (access key ID and secret access key) section. Choose Create New Access Key.
Do AWS access keys expire?
Long-term access keys, such as those associated with IAM users and AWS account root users, remain valid until you manually revoke them. However, temporary security credentials that you obtain through IAM roles and other features of the AWS Security Token Service are valid for only a short time.
Where is the S3 Bucket access key?
Sign in to the AWS Management Console and open the Amazon S3 console at https://console.aws.amazon.com/s3/ . In the Buckets list, choose the bucket that you want to enable an S3 Bucket Key for. Choose Properties. In the Default encryption section, under Bucket Key, you see the S3 Bucket Key setting for your bucket.
Can I access S3 bucket with access key?
Is it possible to access an S3 bucket from another account using the access key ID and secret access key? Yes, if it is configured. Access to S3 is S3 bucket is determined by who you are, your IAM policy, what action you need to and what is the bucket configuration is(policy, permissions, block public access, ...).
How do I use AWS access key and secret key in terraform?
So first I install the AWS CLI. Then we run aws configure. [ ] $ aws configure AWS Access Key ID []: ENTER-YOUR-ACCESS-KEY-HERE AWS Secret Access Key []: ENTER-YOUR-SECRET-KEY-HERE Default region name []: us-west-2 Default output format []
What is AWS S3 endpoint?
A VPC endpoint for Amazon S3 enables AWS Glue to use private IP addresses to access Amazon S3 with no exposure to the public internet. AWS Glue does not require public IP addresses, and you don't need an internet gateway, a NAT device, or a virtual private gateway in your VPC.
What is difference between root user and IAM user in AWS?
There are two different types of users in AWS. You are either the account owner (root user) or you are an AWS Identity and Access Management (IAM) user. The root user is created when the AWS account is created. IAM users are created by the root user or an IAM administrator for the account.
How do I log into AWS console using access key and secret key?
For IAM sign-in dashboard, you need the username and password. When a new IAM user is added, the user gets the username, password, access key and secret key, and the IAM URL from the IAM admin. You can understand this better with the AWS training.
What are the different types of AWS accounts?
There are two types of accounts in an organization: a single account that is designated as the management account, and one or more member accounts. The management account is the account that you use to create the organization.
How do I log into AWS console using access key and secret key?
For IAM sign-in dashboard, you need the username and password. When a new IAM user is added, the user gets the username, password, access key and secret key, and the IAM URL from the IAM admin. You can understand this better with the AWS training.
How do I use AWS access key and secret key in terraform?
So first I install the AWS CLI. Then we run aws configure. [ ] $ aws configure AWS Access Key ID []: ENTER-YOUR-ACCESS-KEY-HERE AWS Secret Access Key []: ENTER-YOUR-SECRET-KEY-HERE Default region name []: us-west-2 Default output format []
Which entity is associated with an access key ID and Secret access key?
IAM userAn IAM user is an entity that represents a person or service. Can be assigned: An access key ID and secret access key for programmatic access to the AWS API, CLI, SDK, and other development tools.
How do I find my AWS CLI credentials?
To list all configuration data, use the aws configure list command. This command displays the AWS CLI name of all settings you've configured, their values, and where the configuration was retrieved from. To list all your profile names, use the aws configure list-profiles command.
Console access
There are two different types of users in AWS. You are either the account owner (root user) or you are an AWS Identity and Access Management (IAM) user. How you sign in to the AWS Management Console depends on whether you are the root user or an IAM user.
Programmatic access
You must provide your AWS access keys to make programmatic calls to AWS or to use the AWS Command Line Interface or AWS Tools for PowerShell.
Temporary access keys
You can also create and use temporary access keys, known as temporary security credentials. In addition to the access key ID and secret access key, temporary security credentials include a security token that you must send to AWS when you use temporary security credentials.
Permissions required
To create access keys for your own IAM user, you must have the permissions from the following policy:
Managing access keys (console)
You can use the AWS Management Console to manage an IAM user's access keys.
Managing access keys (AWS CLI)
To manage an IAM user's access keys from the AWS CLI, run the following commands.
Managing access keys (AWS API)
To manage an IAM user's access keys from the AWS API, call the following operations.
Rotating access keys
As a security best practice, we recommend that you regularly rotate (change) IAM user access keys. If your administrator granted you the necessary permissions, you can rotate your own access keys.
Auditing access keys
You can review the AWS access keys in your code to determine whether the keys are from an account that you own. You can pass an access key ID using the aws sts get-access-key-info AWS CLI command or the GetAccessKeyInfo AWS API operation.
How to get access to my Amazon account?
1 Go to Amazon Web Services console and click on the name of your account ( it is located in the top right corner of the console). Then, in the expanded drop-down list, select Security Credentials. 2 Click the Continue to Security Credentials button. 3 Expand the Access Keys (Access Key ID and Secret Access Key) option.
How to get IAM on Amazon?
1 Go to Amazon Web Services console and click on the name of your account (it is located in the top right corner of the console). In the expanded drop-down list, select Security Credentials. 2 Click the Get Started with IAM Users button.
What happens if you don't write down the key?
If you do not write down the key or download the key file to your computer before you press "Close" or "Cancel" you will not be able to retrieve the secret key in future. Then you'll have to delete the keys which you created start to create new keys. FREE WHITEPAPER.
Can you retrieve a secret key in AWS?
You will see the list of your active and deleted access keys. Note: You cannot retrieve the existing secret key. You can see the AWS secret access key only once immediately after creating. So, in order to get a secret key, you will need to create a new one.
What is AWS access key?
Correct, AWS access key is a unique identifier for a user. BTW, in some cases, it could be considered as sensitive data, sharing access key can lead to tracking like who accesses which systems and when, check this post for more details. If you are an administrator, regularly rotate the access keys for IAM users
What is AWS Signature Version 4?
AWS has designed their own custom authentication algorithm. You are referencing the older signature version (v2), a newer one (v4) was released in 2014. Details are outlined here: Authenticating Requests (AWS Signature Version 4) . A major difference is that the request is not signed with the secret itself, but with a signing key which is generated using the secret. It also uses HMAC-SHA256 for signing.
When AWS CLI sends a API request, the payload is signed by generating an HMAC with?
When AWS CLI sends a API request, the payload is signed by generating an HMAC with the secret key as the key
Can you use access key as password?
Correct, consider your Access key as user name and Secret key as the password.
Can MongoDB create private keys?
The main targeted user base has no knowledge about this sort of thing (just look at the thousands of "open" MongoDB-instances where you can read all the personal data of millions of people without authentication), so requiring the creation of private keys and public certificates will lead to a lot of troubles, security and support wise. With the implementation as it is Amazon can provide you with keys that are created by using "good random" and a short documentation how to use it to access their services.
Our security policy on secret access keys
Secret access keys are—as the name implies—secrets, like your password. For your own security, AWS doesn’t reveal your password to you if you forgot it (you’d have to set a new password). Similarly, AWS does not allow retrieval of a secret access key after its initial creation.
A security suggestion
Remember IAM Best Practice s : you should lock away your AWS root account credentials and use IAM users instead. You can create an IAM user that can do nearly anything that a root account can. The benefit of IAM is that you can control the permissions of an IAM user, or delete the user altogether, at any time.
What is AWS access key?
The Access key ID and Secret Access key values are the security credentials AWS uses to verify your identity and grant or deny you access to specific resources.
How to create access key in AWS?
In the AWS IAM credentials tab scroll down to the Access keys section and click on the Create access key button
What happens if you upload credentials to a remote repository?
If your credentials get exposed, for instance you upload them to a remote repository with public access, you have to immediately deactivate and delete them.
What to do if your account already has credentials?
If your account already has credentials, which you are not using or don't have access to, it's best to deactivate and delete them
Which is the best way to access AWS resources?
Using credentials associated with an IAM account is the recommended way to access AWS resources, because you can control the permissions of an IAM user, whereas the root account permits any action on all resources in the account.
Can you download a file with a secret access key?
Download the file with the Access key id and Secret access key. Note that the Secret Access Key can only be retrieved at the moment of creation.

Console Access
Programmatic Access
- You must provide your AWS access keys to make programmatic calls to AWS or to use the AWS Command Line Interface or AWS Tools for PowerShell. When you create your access keys, you create the access key ID (for example, AKIAIOSFODNN7EXAMPLE) and secret access key (for example, wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY) as a set. The secret access key...
Externally Authenticated Users
- Your users might already have identities outside of AWS, such as in your corporate directory. If those users need to work with AWS resources (or work with applications that access those resources), then those users also need AWS security credentials. You can use an IAM role to specify permissions for users whose identity is federated from your organization or a third-party …
Temporary Access Keys
- You can also create and use temporary access keys, known as temporary security credentials. In addition to the access key ID and secret access key, temporary security credentials include a security token that you must send to AWS when you use temporary security credentials. The advantage of temporary security credentials is that they are short term. After they expire, they're …