What are the best cyber attack maps on Google?
Here are the top 5 Cyber Attack Maps found in Google. They all seem to show the cyber attacks in a slightly different perspective. This is the Norse attack map as an example: Here is a brief overview of each map: 1. Norse's map ranks the country of attack origin, attack type, attack target country and displays a live feed of attacks.
How real is the threat of cyber attacks?
However the fact remains that the average enterprise Is hit by a cyber attack every 1.5 seconds so threats are no less real. As many as 93% of those attacks are phishing attacks carrying ransomware payloads.
Which countries are the top targets for cyber attacks?
This also shows that India and Sweden are the top countries for targets and attacks respectively, however the Norse map shows USA at the top for both. 3.
What is the Raven cyber threat map?
This map is a simple retro-style map that offers a clear description of most of the current attacks, however, for some other attacks you need to register, upgrade your account to view more details. Raven is a free, open-source project that allows anyone to self-host their cyber threat trackers and map.
What is a cyber threat map?
A cyber threat map, also known as a cyber-attack map, is a real-time map of the computer security attacks that are going on at any given time.
How does FireEye threat map work?
FireEye. FireEye's threat map keeps things quite simple; thus, it lacks the details of the other solutions. According to the organization, the map uses "a subset of real attack data" that has been optimized for "better visual presentation."
What is a threat map and what are its uses?
Threat Map is a visual representation of the source and destination locations around the world for the traffic through your Firebox. The Threat Map shows only the event types associated with the detailed view you select: Denied Packets (Blocked) — Shows only denied events.
What is FireEye in cyber security?
FireEye Network Security is an effective cyber threat protection solution that helps organizations minimize the risk of costly breaches by accurately detecting and immediately stopping advanced, targeted and other evasive attacks hiding in Internet traffic.
How accurate are cyber threat maps?
You will see but a very small percentage of the real attacks as they are carefully curated to make it all "look purdy." Nice to show to management because it visualizes the problem and makes it very easy to understand, but do not count on any actual accuracy.
What is FireEye known for?
FireEye is one of the world's top cybersecurity firms with major government and enterprise customers around the world. The company is known for its top-notch research on state-sponsored threat actors and its incident response capabilities.
What is Fortinet threat map?
Cyber crime has become a business. A very profitable business. At any given time, cyber attacks are being flung from all corners of the world.
How does cyber threat intelligence work?
Threat intelligence solutions gather raw data about emerging or existing threat actors and threats from a number of sources. This data is then analyzed and filtered to produce threat intel feeds and management reports that contain information that can be used by automated security control solutions.
What is a Pew Pew map?
Entrenched security professionals view cyber-attack maps with a somewhat jaded eye. They call them "pew pew" maps, mimicking a child-like sound to represent gunfire when playing with toys. In fact, one map actually uses these sounds to an amusing effect.
How does FireEye work?
It uses FireEye Dynamic Threat Intelligence to correlate alerts generated by FireEye and network security products and security logs to validate a threat: Identify and detail vectors an attack used to infiltrate an endpoint. Determine whether an attack occurred (and persists) on a specific endpoint.
What are FireEye tools?
Featured FireEye ProductsHelix Security Platform. Applies threat intelligence, automation, and case management.Endpoint Security. Comprehensive endpoint defense to stop breaches in their tracks.Email Security. Detects and blocks every kind of unwanted email, especially advanced attacks.Cloud Security.
Is FireEye an antivirus?
FireEye Endpoint Security (formerly FireEye HX) is a modern endpoint protection platform combining traditional anti-virus with advanced real-time indicator detection and prevention.
How does FireEye detect and prevent zero day attacks?
It uses the MVX engine to analyze web traffic to detect exploits, malware executables and multi- protocol callbacks. It also includes an Intrusion Prevention System (IPS) with conventional signature matching to detect common attacks and provides riskware protection to block spyware and adware.
How does FireEye NX work?
When deployed inline, FireEye Network Threat Prevention Platform (NX Series) Series blocks outbound callbacks and informs CounterACT about the infected system, the threat severity, and the indicators of compromise (IOCs).
How does FireEye ex work?
FireEye Email Security (EX Series) secures against advanced email attacks. As part of the FireEye Threat Prevention Platform, EX uses signature-less technology to analyze every email attachment and successfully quarantine spear-phishing emails used in advanced targeted attacks.
What is FireEye MVX?
FireEye Network Security MVX is a signature-less, dynamic analysis engine that inspects suspicious objects to identify targeted, evasive and unknown threats. The IDA engines detect and block malicious objects based on machine-, attacker- and victim-intelligence.
What is cyber threat map?
A cyber threat map, also known as a cyber attack map, is a real-time map of the computer security attacks that are going on at any given time. One of the most famous was released by the company Norse and went so viral, even among non-hackers, that it got its own story in Newsweek in 2015.
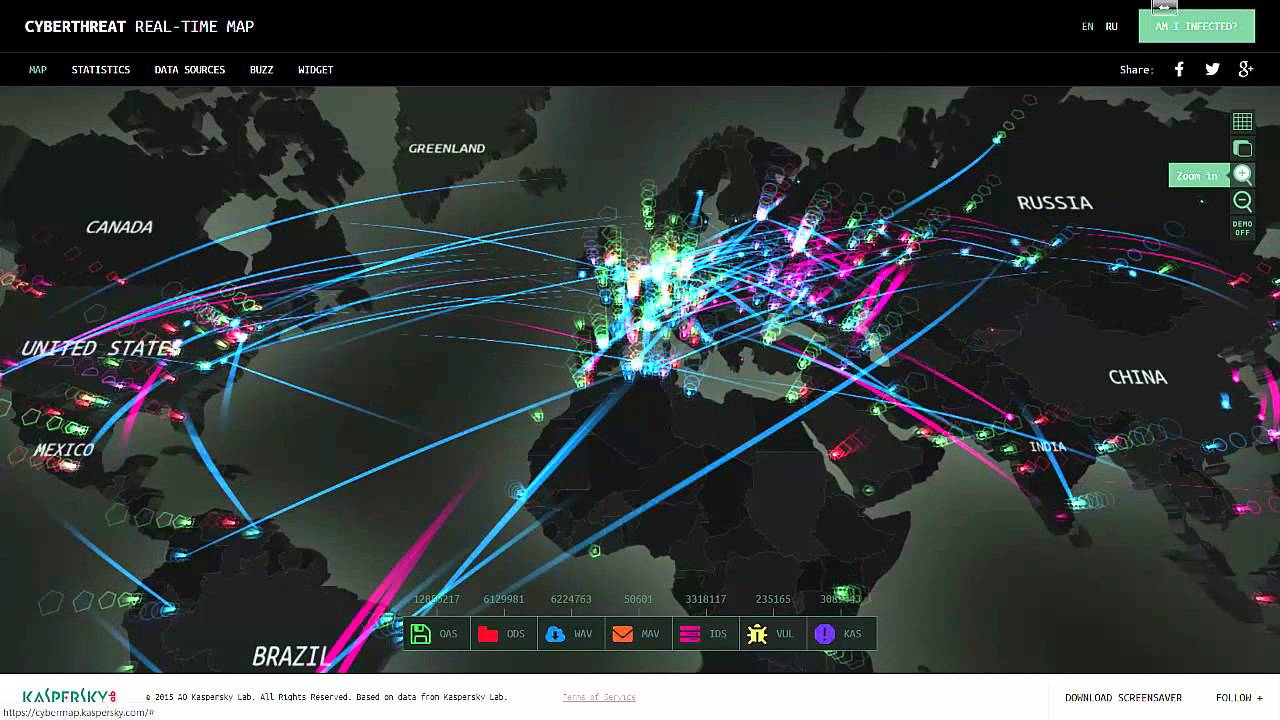
What is a Kaspersky threat map widget?
The Widget. Kaspersky Lab has figured out that cybersecurity professionals often use threat maps to visually represent their work to clients. To make it easier, they have created a Cyberthreat map widget, which you can embed in your website, as shown below, so that clients can see a representation of the latest threats.
What happens when a hacker hits a Norse sensor?
When a hacker hits a Norse sensor, the hacker believed that it had breached a system. Instead, Norse collected information about the hacker’s toolkit, including his or her IP address. This information then manifested as data on the cyber attack map.
Can anyone look at a cyber threat map?
First of all, anyone can look at a cyber threat map and understand something about current attacks. For laypeople, it might just be an understanding of how prevalent these attacks are . For pros, a cyber threat map can provide data that can lead to the discovery of a potential new attack.
Do cyber attacks work like mousetraps?
If cyber attacks are sneaky mice – or, more appropriately, giant rats – then cyber attack maps work like the mousetrap. Norse, for example, maintained a global threat intelligence network of more than 8 million sensors and “honeypots” in 47 countries across the world.
Is Kaspersky a good threat map?
Kaspersky’s cyber threat map may be the best in the business in terms of interactivity and visual appeal. It’s also mobile optimized so you can show it to clients or colleagues from anywhere. And if you want particular data, the site offers you the option to find it.
What is Fireeye threat map?
FireEye's threat map keeps things quite simple; thus, it lacks the details of the other solutions. According to the organization, the map uses "a subset of real attack data" that has been optimized for "better visual presentation."
What is threat map?
Threat maps provide that visual connection that turns information into intelligence. There a few different types of threat maps. Some display comprehensive information, some show limited amounts of data to narrow its scope. Some threat maps use a different timeframe when illustrating attacks, near real-time or historical.
Why are threat maps useful?
In contrast to what some experts say, threat maps can be useful for your organization's threat intelligence as you can gather valuable insights to improve your organization’s cybersecurity posture. However, you shouldn't base your whole threat intelligence efforts on threat maps. Instead, use them as an addition to other sources.
What is threat intelligence?
With cyber attacks happening around the world and across the cyber connected world, threat intelligence, specifically threat maps, are a powerful way to make threats and attackers concrete. Threat maps illustrate the millions of cyber threats happening every day. In addition to visualizing the attacks, cyber threat maps also provide ...
Do threat actors forge their real locations?
Threat actors tend to forge their real locations, meaning that these are often displayed incorrectly on attack maps and their source may be incorrect. As a result, some cybersecurity professionals question the real value of threat maps.
Do threat maps show real time?
Many of these maps may claim that they show data in real-time, but in reality, most show a playback of records of previous attacks. Also, threat maps show anonymized data, without any insights into the identity of the attackers or the victims. Threat actors tend to forge their real locations, meaning that these are often displayed incorrectly on ...
What is Kaspersky map?
The Kaspersky map has a section for statistics, gives an overview of their data sources, and is highly interactive. You can customize the look of the map by filtering certain types of malicious threats, such as email malware, Web site attacks, vulnerability scans, etc. 5.
What is the Norse attack map?
Norse's map ranks the country of attack origin, attack type, attack target country and displays a live feed of attacks. You can also filter the data down by location and by protocol. 2.
Learning Objectives
Who Should Attend
- This is a fast-paced technical course that is designed to providehands-on experience hunting for attackers in modern enterpriseenvironments, including collecting and analyzing endpoint and networkevidence. The content and pace is intended for students with somebackground in incident response, forensic analysis, network trafficanalysis, log analysis, security assessments, and/or p…
Prerequisites
- Completion of Endpoint Investigations instructor-led course; aworking understanding of networking and network security, the Windowsoperating system, file system, registry and regular expressions, andbasic experience scripting in Python (or similar) language.
Course Description
- Attacks against enterprises continue to increase in frequency andsophistication. To proactively detect and defend data and intellectualproperty, organizations must have the ability to look for threatswithout relying solely on security products for detection. Thisintensive three-day course is designed to teach the fundamentalhunting techniques neede...
Hunting Use Cases
- This course includeseight hunting use cases, for example, indicator removal on hosts, DNSprotocol abuse, and others. Each use case follows the hunting processby presenting a hunt mission and providing artifacts for hands-onanalysis in a lab environment. Each use case has the following format: 1. Real-world Threats 2. Technology Review 3. Hunt Mission: Hypothesis Devel…