
What is the purpose of a SQL injection?
SQL injection is a code injection technique used to attack data-driven applications, in which malicious SQL statements are inserted into an entry field for execution (e.g. to dump the database contents to the attacker). SQL injection must exploit a security vulnerability in an application's software, for example, when user input is either incorrectly filtered for string literal escape ...
How to detect SQL injection?
- Use parameterized stored procedures to accept inputs for common searches. ...
- Parameterize dynamic SQL, when used. ...
- Use sp_executesql when executing dynamic SQL. ...
- If needed, use QUOTENAME to cleanse a variable of potentially unwanted characters. ...
- Ensure that application and web code are also cleansing inputs. ...
What is SQL injection how does it work?
With a successful attack, an attacker can gain:
- Unauthorized access to an application. An attacker can successfully bypass an application’s authentication mechanism to have illegitimate access to it.
- Information disclosure. An attack could lead to a complete data leakage from the database server.
- Loss of data availability. ...
- Compromised data integrity. ...
What is the impact of SQL injection?
- User Authentication: Validating input from the user by pre-defining length, type of input, of the input field and authenticating the user.
- Restricting access privileges of users and defining as to how much amount of data any outsider can access from the database. ...
- Do not use system administrator accounts.
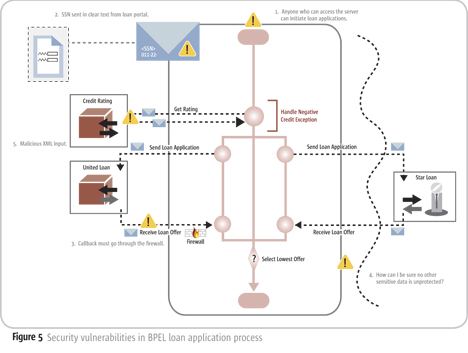
What do you mean by SQL injection?
SQL injection is a code injection technique that might destroy your database. SQL injection is one of the most common web hacking techniques. SQL injection is the placement of malicious code in SQL statements, via web page input.
What is SQL injection and how it works?
SQL injection (SQLi) is a type of cyberattack against web applications that use SQL databases such as IBM Db2, Oracle, MySQL, and MariaDB. As the name suggests, the attack involves the injection of malicious SQL statements to interfere with the queries sent by a web application to its database.
What is SQL injection and its types?
In-band SQL Injection occurs when an attacker is able to use the same communication channel to both launch the attack and gather results. The two most common types of in-band SQL Injection are Error-based SQLi and Union-based SQLi.
Why SQL injection is used?
Attackers use SQL injection to alter or update data in the database and add additional data. For instance, in the case of a financial application, an attacker can use SQL injection to change account balances. Even worse, attackers can gain administrative rights to an application database.
Why do hackers use SQL injection?
Using SQL injection, a hacker will try to enter a specifically crafted SQL commands into a form field instead of the expected information. The intent is to secure a response from the database that will help the hacker understand the database construction, such as table names.
What are 5 types of SQL injection?
You can classify SQL injections types based on the methods they use to access backend data and their damage potential.In-band SQLi. The attacker uses the same channel of communication to launch their attacks and to gather their results. ... Inferential (Blind) SQLi. ... Out-of-band SQLi.
How is SQL injection prevention?
How to Prevent an SQL Injection. The only sure way to prevent SQL Injection attacks is input validation and parametrized queries including prepared statements. The application code should never use the input directly. The developer must sanitize all input, not only web form inputs such as login forms.
How is SQL injection detected?
Detection methods range from checking server logs to monitoring database errors. Most network intrusion detection systems (IDS) and network perimeter firewalls are not configured to review HTTP traffic for malicious SQL fragments, making it possible for an attacker to bypass network security boundaries.
Overview
- Businesses use fields such as contact forms, feedback forms, checkout forms, and search bars to interact with website users. These fields let users legitimately submit information to the business’s database and retrieve information from it. This “open line” between user and database is prone to a web security threat known as SQL injection.If the field is coded incorrectly, an attac…
Definition
- SQL Injection is the technique of inserting complete or partial SQL commands in user-supplied data fields of web applications and submitting them for execution by the database server.
Example
- The first example is very simple. It shows, how an attacker can use an SQL Injection vulnerability to go around application security and authenticate as the administrator. The following script is pseudocode executed on a web server. It is a simple example of authenticating with a username and a password. The example database has a table named users with the following columns: us…
- One example is Havij, a tool that was developed by Iranian security professionals. Point it at a potential target and Havij probes the site to determine what type of database is in use. Using that knowledge, Havij then builds queries to probe characteristics of the database. Requiring little to no SQL expertise from the end user, Havij can potentially extract fields, tables, and sometimes e…
- We will use as an example the HTB23101 security advisory (CVE-2012-4034), specifically vulnerability 1.7.This vulnerability allows execution of arbitrary SQL commands by modifying HTTP POST parameters. Successful exploitation requires that HTTP Referer belongs to the vulnerable website.To demonstrate vulnerability exploitation we will use the Burp Suite. To do s…
Prevention
- The only sure way to prevent SQL Injection attacks is input validation and parametrized queries including prepared statements. The application code should never use the input directly. The developer must sanitize all input, not only web form inputs such as login forms. They must remove potential malicious code elements such as single quotes. It is also a good idea to turn o…
- The first step in preventing a SQL injection attack is to establish which (if any) of your applications are vulnerable. The best way to do this is to launch your own attacks to see whether they are successful. But SQL is a complex language, so it is not a trivial task to construct code snippets that can be injected into a query to attempt to compromise a database. The good news is that th…
- Now that we know what a SQL injection is, let's see how we can protect our code from this kind of attack. Here we're focusing on a couple of very effective techniques available in Java and other JVM languages, but similar concepts are available to other environments, such as PHP, .Net, Ruby and so forth.For those looking for a complete list of available techniques, including database-sp…
Mitigation
- An SQL injection is a well known attack and easily prevented by simple measures. After an apparent SQL injection attack on TalkTalk in 2015, the BBC reported that security experts were stunned that such a large company would be vulnerable to it.
- We believe that web application developers often simply do not thinkabout \"surprise inputs\", but security people do (including the bad guys),so there are three broad approaches that can be applied here.Note that not all databases are configured the same way, and not alleven support the same dialect of SQL (the \"S\" stands for \"Structured\",not \"Standard\"). For instance, most vers…
- Neutralization of input data is considered the main defense approach against SQL injection attacks. This should be achieved by sanitizing input data before using it in SQL queries within application or by means of security software such as WAF or IDS/IPS system.We will try to demonstrate common errors that occur during development and give advices on how to avoid th…
Conclusion
- In this article, we've covered SQL Injection vulnerabilities in Java applications – a very serious threat to any organization that depends on data for their business – and how to prevent them using simple techniques.As usual, full code for this article is available on Github.
- In this article we have demonstrated some techniques for helping defend against SQL Injection attacks. We can see that we can implement security measures both in the database itself (such as implementing Stored Procedures and restricting table permissions) as well as in the front end application (such as user validation and error handling). If your database supports Stored Proce…
- An attacker gaining administrative access to a database is an extreme security breach that SQL injection makes possible. Through this type of attack, a hacker can change or delete parts of the entire database. The attacker can also launch attacks from a compromised server and access confidential information stored in the database. Preventing this major security threat is possible …
- SQL Injection is a real problem, and there are many documented real-life incidents that have led to credit card information or Telcommunication network customer data being stolen.For this reason, you should always use bind parameters, and, for dynamic queries, you should rely on a framework that was designed for such a task, like Criteria API or jOOQ.You should never resort to using Stri…
Security
- An SQL Injection vulnerability may affect any website or web application that uses an SQL database such as MySQL, Oracle, SQL Server, or others. Criminals may use it to gain unauthorized access to your sensitive data: customer information, personal data, trade secrets, intellectual property, and more. SQL Injection attacks are one of the oldest, most prevalent, and most dange…
- See our picks for top database security tools to help protect your company from SQL injection attacks A successful attack on the database that drives a website or web application, such as a SQL injection login bypass attack, can potentially give a hacker a broad range of powers, from modifying web site content (\"defacing\") to capturing sensitive information such as account cre…
Types
- There are several types of SQL Injection attacks: in-band SQLi (using database errors or UNION commands), blind SQLi, and out-of-band SQLi. You can read more about them in the following articles: Types of SQL Injection (SQLi), Blind SQL Injection: What is it.
Introduction
- In the first part of this series we saw how SQL Injection attacks work, how they can be used by a hacker to hack all major database brands, and the potential consequences of leaving yourself open to them. In this article we will look at the methods you can secure your database and front end applications to protect yourself from SQL Injection hacks. We will discover that multiple tec…
- One of my readers asked me to answer the following StackOverflow question. Right from the start, I noticed that the entity query was constructed by concatenating strings, which can expose your application to SQL Injection attacks.Unfortunately, I’ve been seeing this problem over and over throughout my career, and not all developers are aware of the serious risk associated with …
Form
- SQL injection was considered one of the top 10 web application vulnerabilities of 2007 and 2010 by the Open Web Application Security Project. In 2013, SQLI was rated the number one attack on the OWASP top ten. There are four main sub-classes of SQL injection: Classic SQLI Blind or Inference SQL injection Database management system-specific SQLI Compounded SQLI SQL inj…
- At this point, we know how to create code that is invulnerable to SQL injection. We learned that the correct way to handle application-level SQL calls is through parameterized queries. In .NET languages like C# and VB.NET, we have access to easy-to-use classes and methods, some of which we discussed in this article. Other web frameworks and programming languages have the…