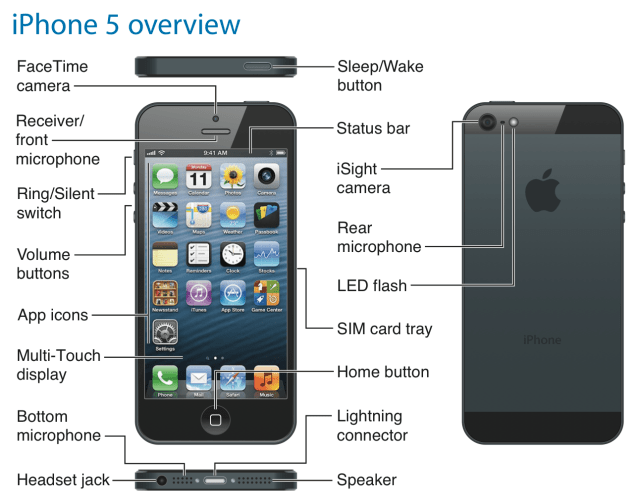
For example:
| Main configuration file name | User configuration file name |
| stt_cs_cz_5_online.bs | stt_cs_cz_5_online.bs .usr |
| kws_nl_nl_5.bs | kws_nl_nl_5.bs .usr |
| phnrec_pashto.bs | phnrec_pashto.bs .usr |
| vpextract4_xl4.bs | vpextract4_xl4.bs .usr |
How can I configure an user?
Configure User Accounts . Navigate to Users | Local Users & Groups. Click Add. Under the Ssettings tab enter the desired Name and Ppassword. On the Groups Tab ensure the user is a member of Trusted Users. On to VPN Access tab , select the Address Objects or Address Groups that the user needs access to and add to the user's access list. Click OK.
How do I add another user to my computer?
To add another account to your PC:
- Select Start > Settings > Accounts > Access work or school.
- Next to Add a work or school account, select Connect.
- Enter that person's account info, select the account type, and then select Add.
How to switch users in Windows 11?
Change an Account to Administrator via Windows Settings
- Press the Win + I keys on the keyboard to open Windows 11 Settings. ...
- Navigate to the Accounts section and click Family & other users.
- Under the Other users section, you can see all the user accounts on the Windows 11 system. ...
- Select Administrator and click OK to save the change. ...
How to reset configuration?
How to reset configuration. 1) unplug the device from power. 2) press and hold the button right after applying power. Note: hold the button until LED will start flashing. 3) release the button to clear configuration. Note: If you wait until LED stops flashing, and only then release the button - this will instead launch Netinstall mode, to ...
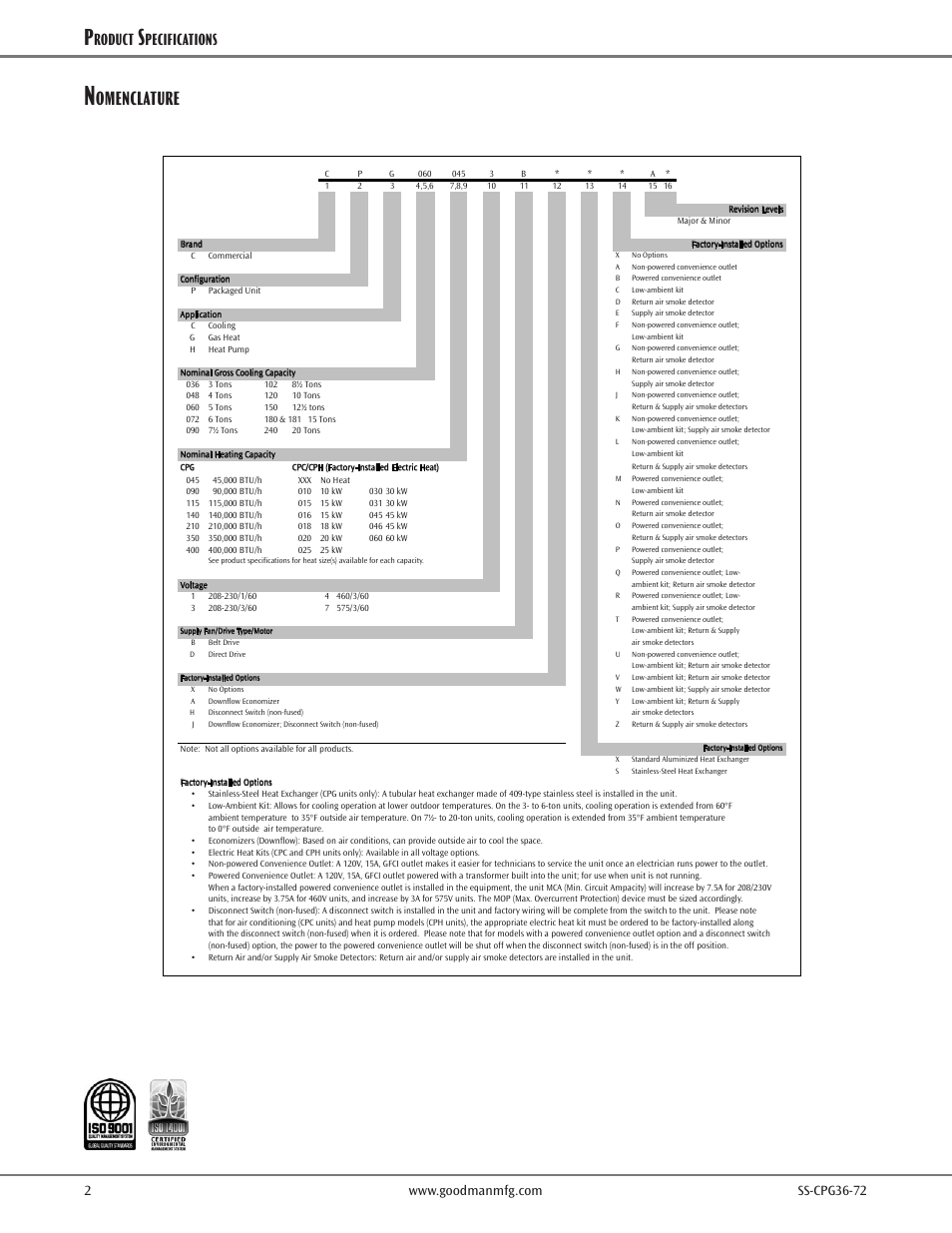
What is user configuration and computer configuration?
Computer Configuration: These policies apply to the local computer, and do not change per user. User Configuration: These policies apply to users on the local machine, and will apply to any new users in the future, on this local computer.
What is a user configuration file?
In computing, configuration files (commonly known simply as config files) are files used to configure the parameters and initial settings for some computer programs. They are used for user applications, server processes and operating system settings.
What is single user configuration?
Single-user mode is a mode in which a multiuser computer operating system boots into a single superuser. It is mainly used for maintenance of multi-user environments such as network servers. Some tasks may require exclusive access to shared resources, for example running fsck on a network share.
What are the types of user server configuration?
Types of serversWeb server. An open-source web server is used for accessing the world wide web through public domain software. ... Proxy server. ... Virtual machine (VM) ... File transfer protocol (FTP) server. ... Application server. ... File server. ... Database server. ... 8. Mail server.More items...
What is a configuration example?
When artwork is laid out in order to maximize the connections between the pieces, this is an example of configuration. When you try to set up your computer hardware and software to work the way you want such as adding a wireless mouse and keyboard, this is an example of configuration.
What is configuration settings?
Definition(s): The set of parameters that can be changed in hardware, software, or firmware that affect the security posture and/or functionality of the information system.
What is the importance of configuring user access?
User access levels define what information the different users on your account can access and edit. They are particularly important for when you want to keep your employees' hourly rates confidential. When adding a new user, you'll be asked to assign them a user role.
What is user Access configuration level?
The Access Management section enables the Administrator to add, copy or delete users, groups or sites in the system. Each user must be assigned to at least one group in order to determine their security level. Each group is assigned a specific security level.
What is network configuration?
Network configuration is the process of assigning network settings, policies, flows, and controls. In a virtual network, it's easier to make network configuration changes because physical network devices appliances are replaced by software, removing the need for extensive manual configuration.
What is server configuration?
A server configuration defines a specific database as the repository for its data. To prevent corruption, that database can be associated with only one server configuration. However, that database can be used by other applications.
What is the basic server configuration?
Step-by-step Guide To Setting Up A Server Select The Server Hardware. Select The Server Operating System. Choose A Good Server Location. Configure The Server. Implement Server Security.
Where is user configuration in Windows 7?
In Windows 7: . Open User Account Control Settings, type UAC in the Start Search box, and then click Change User Account Control settings in the Control Panel window.
Where is the users configuration file located?
As per the XDG standard, all user-specific config files are stored inside the $XDG_CONFIG_HOME directory (usually /home/
What is user configuration file in Linux?
What are Linux Configuration Files? A configuration file, also known as a config file, is a local file that controls the operations of a program, utility or process. Linux configuration files contain the settings and instructions for different systems, utilities, applications and processes.
Which configuration file you will be able to see a list of users?
User information is stored in the system's /etc/passwd file. Looking at the contents of this file will allow us to see a list of the users on a system. Each user will take up one line in the file.
What is the importance of configuring user access?
User access levels define what information the different users on your account can access and edit. They are particularly important for when you want to keep your employees' hourly rates confidential. When adding a new user, you'll be asked to assign them a user role.
What is software settings?
The Software Settings folder under User Configuration contains software settings that apply to users regardless of which computer they log on to. This folder also contains software installation settings, and it might contain other settings that are placed there by independent software vendors (ISVs).
What is the Windows Settings folder?
The Windows Settings folder under User Configuration contains Windows settings that apply to users regardless of which computer they log on to. This folder also contains the following items: Folder Redirection, Security Settings, and Scripts.
Where are security settings?
Security settings are available under the Windows Settings folder under Computer Configuration and User Configuration in Group Policy Object Editor. Security settings or security policies are rules that you configure on a computer or multiple computers that protect resources on a computer or network. With security settings, you can specify the security policy of an organizational unit, domain, or site.
Security Configurations
Desktop Central offers a bunch of configurations that when deployed, aids in hardening the security of your endpoints. The security configurations offered by Desktop Central are as follows :
Productivity Configurations
Amp up the productivity of your network by deploying the following configurations to all the computers in your network.
Desktop Configurations
Deploy the below mentioned desktop configurations & save ample amount of time in managing the desktops.
What is user configuration?
The “User Configuration” screen allows you to view your Username, the Name on the account, Status, Employed By, Password Expiration information, Last Login, Last Inquiry, Last Push, Last Browser Used, Screen Resolution, Failed Login Attempts, and Last Failed Login. The areas that you can take action on are changing your password, changing your name, and adding a Carrier Contact Role.
How many sections are there in user configuration?
User Configuration is broken out into six different sections. Each section, User Config, Contact Info, User Activity, Push Options, Services, and Lookup Codes will be shown below.#N#To access the User Configuration sections, hover over the cogwheel (1), and choose the section that you need to work with.
What is pipeline system access?
Pipeline System Access - Pipeline System Access allows you to see the permissions that you have, including the Carrier, Company, User Type, Product, and Locations. If you need to make changes to any of these permissions, please contact your company administrator or the Transport4 Help Desk.
How to add carrier contact in Colonial?
Colonial will use this information if it needs to contact someone at your company. To add a “Carrier Contact Role” click “Add Carrier Contact Role” and choose from the “Available Roles” on the left. Click the role that you would like to add and use the arrow key to move it to the “Assigned Roles” on the right.
Can administrators search for other users?
Administrators can work with these features on other accounts as well as their own. In addition to the basic configuration, administrators can search to find other users, add PSS rights, add Carrier Contact Roles, add Users, copy Users, and edit Users.
What is the difference between a computer configuration and a user configuration?
The first one is rather obvious and concerns the type of object that Group Policy affects (computer and user, respectively). What might be less obvious is the fact that some of the settings exist only within a computer or user context.
Where are group policies stored?
While NT 4—based System Policies are stored entirely in files with the extension .pol located in the NETLOGON share (on all domain controllers), the contents of Group Policies are split between Active Directory and files. The Active Directory part is called the Group Policy Container (GPC). The remaining part, known as the Group Policy Template (GPT) resides in the System Volume (SYSVOL) folder on all Windows 2000 and Windows Server 2003 domain controllers. Both locations (Active Directory and file system) contain a uniquely named subfolder structure within the Policies folder, as shown in Figures 11.7 and 11.8. Each subfolder is named with the Globally Unique Identifier (GUID) of the GPO that it contains. The GUID uniquely identifies Active Directory objects. As you can see on the right side of both figures, within each GPO folder are two subfolders, MACHINE and USER. The Group Policy Template also contains a file, GPT.INI. One of its purposes is maintaining a version number that is used to determine if the policy has been changed. The Group Policy Container stores similar information in the Version Number Active Directory attribute. Both version numbers are used to prevent unnecessary processing of the GPO (when no changes have occurred since the GPO was last applied) and keep the GPC and GPT synchronized.
Is desktop configuration irrelevant?
Similarly, Desktop configuration is irrelevant from the computer configuration point of view, since a computer object does not run any interactive sessions and does not use the Desktop.
What is a configuration file?
Configuration files can be, and often are, very simple in structure. For instance, if you were to write an application, and the only thing it ever needed to know was its user's preferred name, then its one and only config file could contain exactly one word: the name of the user. For example:
Where are the configuration files on my computer?
There are thousands of configuration files on your computer. You may never directly interact with the bulk of them, but they're scattered throughout your /etc folder and in ~/.config and ~/.local and /usr. There are probably some in /var and possibly even in /opt. If you've ever opened one by accident or to make a change, you may have wondered why some configuration files look one way while others look completely different.
Why are config files important?
They allow you to customize how you interact with an application or how an application interacts with the rest of your system. It's thanks to config files that any time you launch an application, it has "memories" of how you like to use it.
What format do you use for configuration?
If you must use a binary format for configuration, use one that already exists as an open standard, such as NetCDF.
Why is it important to store configurations?
Storing configurations is a flexible task because as long as developers know how their code puts data into a file, they can easily write code to extract that data as needed. However, the tech industry graciously favors well-documented standardization, so several well-known formats have evolved over the years to make configuration easy.
Does configuration use a key?
Usually, though, an application needs to keep track of more than just one piece of information, so configuration often uses a key and a value:
Question
Recently I noticed that user configuration settings is disabled on default domain controller policy. I wonder if it is disabled by design or by someone manually.
Answers
Testing in my lab for user configuration settings on default domain controller policy, nothing is configured, however, it is still showed as enabled.
All replies
Testing in my lab for user configuration settings on default domain controller policy, nothing is configured, however, it is still showed as enabled.
