
Free & open source computer forensics tools
- Forensic toolkits. These are multipurpose forensic toolkits that can carry out a number of detailed digital forensic tasks.
- Network forensic tools. These tools help in the extraction and forensic analysis of activity across the network. ...
- Forensic imaging tools. ...
- Memory forensics. ...
- Website forensics. ...
- Removable media forensics. ...
Full Answer
What is the best free forensic investigation tool for IT security?
22 FREE Forensic Investigation Tools for IT Security Expert. 1 Autopsy. Autopsy is a GUI-based open source digital forensic program to analyze hard drives and smartphones efficiently. Autospy is used by thousands ... 2 Encrypted Disk Detector. 3 Wireshark. 4 Magnet RAM Capture. 5 Network Miner. More items
What are the different types of digital forensics tools?
Here are some broad categories to give you an idea of the variety that comes under the umbrella of digital forensics tools: Database forensics. Email analysis. Audio/video forensics. Internet browsing analysis. Network forensics. Memory forensics. File analysis.
Are there any free forensic tools available for Linux?
SIFT (SANS investigative forensic toolkit) workstation is freely available as Ubuntu 14.04. SIFT is a suite of forensic tools you need and one of the most popular open source incident response platform. Extract all exciting information from Firefox, Iceweasel and Seamonkey browser to be analyzed with Dumpzilla. Foxton has two free exciting tools.
What is software forensics used for?
Software forensics. It is the centerpiece of lawsuits, trials, and settlements when companies are in dispute over issues involving software patents, copyrights, and trade secrets. Software forensics tools can compare code to determine correlation, a measure that can be used to guide a software forensics expert.
What is a deft?
What is NFAT for Mac?
How many downloads does the SIFT tool have?
What is forensics tool?
What is a sleuth kit?
How much will cybercrime cost in 2019?
What is Wireshark used for?
See 4 more
About this website
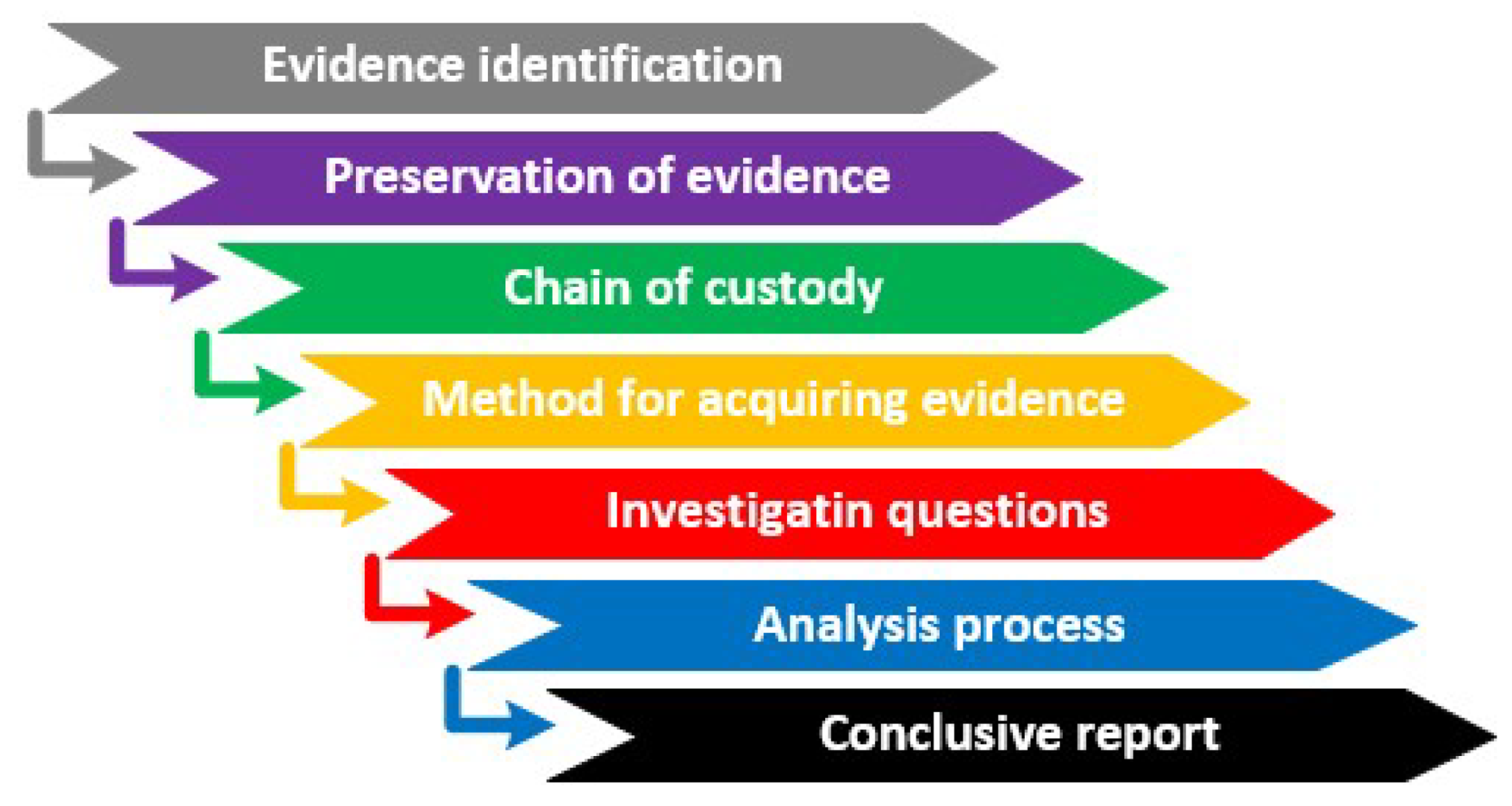
What is a free tool for creating forensic images?
SIFT Workstation SIFT (SANS investigative forensic toolkit) Workstation is a freely-available virtual appliance that is configured in Ubuntu 14.04. SIFT contains a suite of forensic tools needed to perform a detailed digital forensic examination. It is one of the most popular open-source incident response platforms.
What type of forensics is the tools used for?
Digital Forensic Tools are software applications that help to preserve, identify, extract, and document computer evidence for law procedures. These tools help to make the digital forensic process simple and easy.
Which is an open-source forensic tool?
Xplico. This is an open-source network forensic analysis tool (NFAT) that can extract app data from internet traffic. For instance, Xplico can extract email, HTTP contents, VoIP call, FTP, TFTP, etc., from a pcap file.
Which of the following software is used in computer forensic?
Computer forensicsNamePlatformVersionDigital Forensics FrameworkUnix-like/Windows1.3Elcomsoft Premium Forensic BundleWindows, macOS1435E3: Universal SoftwareWindows3.1EnCaseWindows8.1117 more rows
What is FTK Imager used for?
FTK® Imager can create perfect copies, or forensic images of computer data without making changes to the original evidence. The forensic image is identical in every way to the original, including file slack and unallocated space or drive free space.
What are the 3 most important tools in forensic sciences?
During the forensic science process, forensic equipment is used to process samples and evidence to solve crimes....13 Technologies for Modern Forensic SciencesLINK ANALYSIS SOFTWARE. ... DRUG TESTING. ... LA-ICP-MS. ... FIRE TECHNOLOGY. ... 3D SCANNER. ... HIGH-POWERED MICROSCOPES. ... HIGH-SPEED BALLISTICS PHOTOGRAPHY.More items...•
Is access data FTK open-source?
FTK Imager is an open-source software by AccessData that is used for creating accurate copies of the original evidence without actually making any changes to it.
Is Forensic Toolkit free?
Yes, there is. Forensic Toolkit (FTK) is a computer forensics software application provided by AccessData. The toolkit includes a standalone disk imaging program called FTK Imager. FTK Imager is a free tool that saves an image of a hard disk in one file or in segments that may be reconstructed later.
What is digital forensic software?
It is an open-source software that analyzes disk images created by “dd” and recovers data from them. With this software, professionals can gather data during incident response or from live systems. Professionals can integrate TSK with more extensive forensics tools. FTK Imager.
What are the two types of forensics software tools?
Due to the wide variety of different types of computer-based evidence, a number of different types of computer forensics tools exist, including: Disk and data capture tools. File viewers. File analysis tools.
What is a database forensic tool?
Database servers store sensitive information. Database forensics refers to the branch of digital forensic science specifically related to the study of databases and the data they keep. Database forensics look at who access the database and what actions are performed.
Which of the following are forensic imaging software?
The process of forensic imaging is itself managed by "imaging software" like TIM (the Tableau Imager), EnCase Forensic or FTK Imager. Imaging software creates reads the source evidence through the write blocker and creates a "forensic image" on a destination device.
What are the two types of forensics software tools?
Due to the wide variety of different types of computer-based evidence, a number of different types of computer forensics tools exist, including: Disk and data capture tools. File viewers. File analysis tools.
What tools do forensic scientists use to collect evidence?
portable infrared, laser or ultraviolet light. Digital camera. voice recorder. sketchpad, logbooks, and pens....But the most common tools in a forensic lab are:Laboratory Microscopes.Portable/ Laboratory Fume Extractor.GC System.Mass Spectrometers.
What tools are used to analyze evidence?
The instruments commonly used in criminal or environmental forensic investigations and analysis include scanning electron and optical microscopes. These tools are used to characterize forensic evidence like fabrics, metals, textile or glass.
What tools are needed for evidence?
Bodily fluid collection kit (sterile swabs, distilled water, — optional presumptive tests, and sterile packaging that allows the swabs to air dry). Camera (plus memory cards, back up battery, remote flash, tripod and remote cord). Evidence seals/tape. Flashlight(s) with extra batteries.
Top 10 free tools for digital forensic investigation
Juniper researchers state that cybercrime will cost over 2 trillion USD to businesses by 2019. As costs go up, so the demand for digital forensic experts will increase in tandem. Tools are a forensic examiner's best friend – using the right tool helps to move things faster, improve productivity and gather all the evidence.
The Best Open Source Digital Forensic Tools
Forensic investigations are always challenging as you may gather all the information you could for the evidence and mitigation plan. Here are some of the computer forensic investigator tools you would need. Most of them are free! Whether it’s for an internal human resources case, an investigation into unauthorized access to a server, or if you
Open Source Android Forensics Toolkit download | SourceForge.net
Download Open Source Android Forensics Toolkit for free. OSAF-TK your one stop shop for Android malware analysis and forensics. Welcome to OSAF! The OSAF-Toolkit was developed, as a senior design project, by a group of IT students from the University of Cincinnati, wanting to pioneer and pave the way for standardization of Android malware analysis.
What is a deft?
DEFT (digital evidence and forensics toolkit) is a Linux-based distribution that allows professionals and non-experts to gather and preserve forensic data and digital evidence. The free and open source operating system has some of the best computer forensics open source applications. DEFT Zero is a lightweight version released in 2017.
What is NFAT for Mac?
This is a network forensic analysis tool (NFAT) for Windows, Mac OS X, Linux, and FreeBSD. These tools come in a free edition as well as a professional paid edition. Network Miner’s free edition can
How many downloads does the SIFT tool have?
Tools can be opened manually from the terminal window or with the help of top menu bar. Having more than 100,000 downloads to date, SIFT continues to be a widely used open-source forensic and incident response tool.
What is forensics tool?
Available in free and professional versions, this forensics tool helps you to collect evidence from a mobile phone. It collects all device information such as serial number, IMEI, OS, etc., and recovers messages, contacts and call logs. Its file browser feature enables you to have access to and analyze photos, documents, videos and device database.
What is a sleuth kit?
Sleuth Kit Autopsy. Autopsy is a digital forensics platform that efficiently analyzes smartphones and hard disks. It is used worldwide by a large number of users, including law enforcement agencies, the military, and corporations to carry out investigations on a computer system.
How much will cybercrime cost in 2019?
According to Juniper Research, cybercrime losses to businesses will surpass $2 trillion by the year 2019. With data breaches occurring all around the world every day, the demand for experts in computer forensics will also increase. Whether you need to investigate an unauthorized server access, look into an internal case of human resources, or are interested in learning a new skill, these free and open source computer forensics tools will help you conduct in-depth analysis, including hard drive forensics, memory analysis, forensic image exploration, and mobile forensics. However, this is not an extensive list by all means and may not cover all necessary tools required for a complete investigation. It only includes some of the popular and useful tools. Using the right tools can always help you move things faster and result in more productive results.
What is Wireshark used for?
WireShark is one of the most commonly used network protocol analyzers. It allows you to investigate your network activity at the microscopic level. Wireshark is widely used by government agencies, corporations and educational institutes.
What is the most famous Linux forensic suite?
Pala din. PALADIN forensic suite – the world’s most famous Linux forensic suite is a modified Linux distro based on Ubuntu available in 32 and 64 bit. Paladin has more than 100 tools under 29 categories, almost everything you need to investigate an incident. Autospy is included in the latest version – Paladin 6.
What is autopsy software?
Autopsy is a GUI-based open source digital forensic program to analyze hard drives and smartphones efficiently. Autospy is used by thousands of users worldwide to investigate what happened on the computer.
What is RAM capturer?
RAM Capturer by Belkasoft is a free tool to dump the data from a computer’s volatile memory. It’s compatible with Windows OS. Memory dumps may contain encrypted volume’s password and login credentials for webmails and social network services.
What is a defraser?
Defraser forensic tool may help you to detect full and partial multimedia files in the data streams.
What is a FAW?
FAW (Forensics Acquisition of Websites) is to acquire web pages for forensic investigation, which has the following features.
How much will cybercrime cost in 2024?
Juniper Research suggests Cybercrime will cost over $5 trillion to the business by 2024. So computer forensic expert demand will also increase.
How much will data breach cost in 2024?
A data breach happens almost every day. Juniper Research suggests Cybercrime will cost over $5 trillion to the business by 2024. So computer forensic expert demand will also increase. Tools are the administrator’s best friend; using the right tool always helps you to move things faster and make you productive.
What is a paladin forensic suite?
Paladin Forensic Suite is a Live CD based on Ubuntu that is packed with wealth of open source forensic tools. The 80+ tools found on this Live CD are organized into over 25 categories including Imaging Tools, Malware Analysis, Social Media Analysis, Hashing Tools, etc.
What is FTK imager?
FTK Imager is a data preview and imaging tool that allows you to examine files and folders on local hard drives, network drives, CDs/DVDs, and review the content of forensic images or memory dumps . Using FTK Imager you can also create SHA1 or MD5 hashes of files, export files and folders from forensic images to disk, review and recover files that were deleted from the Recycle Bin (providing that their data blocks haven’t been overwritten), and mount a forensic image to view its contents in Windows Explorer.
What is ExifTool used for?
ExifTool is a command-line application used to read, write or edit file metadata information. It is fast, powerful and supports a large range of file formats (although image file types are its speciality). ExifTool can be used for analysing the static properties of suspicious files in a host-based forensic investigation, for example.
What is a deft CD?
DEFT is another Linux Live CD which bundles some of the most popular free and open source computer forensic tools available. It aims to help with Incident Response, Cyber Intelligence and Computer Forensics scenarios. Amongst others, it contains tools for Mobile Forensics, Network Forensics, Data Recovery, and Hashing.
What is a free hex editor?
Free Hex Editor Neo is a basic hex editor that was designed to handle very large files. While a lot of the additional features are found in the commercial versions of Hex Editor Neo, I find this tool useful for loading large files (e.g. database files or forensic images) and performing actions such as manual data carving, low-level file editing, information gathering, or searching for hidden data.
What is digital image forensics?
Digital image forensics. While this is not an exhaustive list, it gives you a picture of what constitutes digital forensics tools and what you can do with them. Sometimes multiple tools are packaged together into a single toolkit to help you tap into the potential of related tools.
How to parse USB files?
When you launch USB Historian, click the ‘+’ icon on the top menu to launch the data parse wizard. Select which method you want to parse data from (Drive Letter, Windows and Users Folder, or Individual Hives/Files) and then select the respective data to parse. Once complete you will see information similar to that shown in the above image.
What is a pentoo overlay?
Pentoo Penetration Testing Overlay and Livecd is a live CD and Live USB designed for penetration testing and security assessment. Based on Gentoo Linux, Pentoo is provided both as 32-bit and 64-bit installable live CD. Pentoo also is available as an overlay for an existing Gentoo installation. It features packet injection patched wifi drivers, GPGPU cracking software, and many tools for penetration testing and security assessment. The Pentoo kernel includes grsecurity and PAX hardening and extra patches – with binaries compiled from a hardened toolchain with the latest nightly versions of some tools available.
What is memory forensics?
Memory forensics tools are used to acquire or analyze a computer's volatile memory (RAM). They are often used in incident response situations to preserve evidence in memory that would be lost when a system is shut down, and to quickly detect stealthy malware by directly examining the operating system and other running software in memory.
What is Kali Linux?
Kali Linux is a Debian-derived Linux distribution designed for digital forensics and penetration testing, formerly known as BackTrack. Parrot Security OS is a cloud-oriented Linux distribution based on Debian and designed to perform security and penetration tests, do forensic analysis, or act in anonymity. It uses the MATE Desktop Environment, ...
What is mobile device forensics?
Mobile device forensics. Mobile forensics tools tend to consist of both a hardware and software component. Mobile phones come with a diverse range of connectors, the hardware devices support a number of different cables and perform the same role as a write blocker in computer devices.
What was the most common method of forensic investigation in the 1980s?
During the 1980s, most digital forensic investigations consisted of "live analysis", examining digital media directly using non-specialist tools. In the 1990s, several freeware and other proprietary tools (both hardware and software) were created to allow investigations to take place without modifying media.
What is the key used to decrypt a file?
In encryption, the key used to decrypt the file. The file owner keeps the private key. public key. In encryption, the key used to encrypt a file; it's held by a certificate authority, such as a global registry, network server, or company such as VeriSign.
What is drive slack?
Drive slack is made up of both file slack and RAM slack. A public/private key encryption first used in Windows 2000 on NTFS-formatted disks. The file is encrypted with a symmetric key, and then a public/private key is used to encrypt the symmetric key. the original Microsoft file structure database.
What is virtual machine?
Virtual machines are limited to the host computer's peripheral configurations, such as mouse, keyboard, CD/DVD drives, and other devices. Virtual machines can run only OSs that are older than the physical machine's OS.
What is a device driver?
Device drivers contain instructions for the OS on how to interface with hardware devices.
What is zone bit recording?
Zone bit recording is how disk manufacturers ensure that a platter's outer tracks store as much data as possible.
What does "re-create a suspect drive" mean?
Re-create a suspect drive to show what happened.
What is a "reproducible results"?
Records an investigator's actions in examining a case. In testing tools, the term "reproducible results" means that if you work in the same lab on the same machine, you generate the same results. True.
What is the Honeynet Project?
T/F The Honeynet Project was developed to make information widely available in an attempt to thwart Internet and network attackers.
Why is T/F important in forensics?
T/F One of the most critical aspects of digital forensics is validating digital evidence because ensuring the integrity of data you collect is essential for presenting evidence in court.
How many modes of defense does the NSA have?
The NSA's defense in depth (DiD) strategy contains three modes of protection. Which option below is not one of the three modes?
What does T/F mean in a file system?
T/F The Sysinternals Handle utility shows only file system activity, but does not show what processes are using files on the file system .
Why is T/F not possible?
T/F Because attorneys do not have the right of full discovery of digital evidence, it is not possible for new evidence to come to light while complying with a defense request for full discovery.
Should the hard drive be removed?
The hard drive should be removed, if practical, and the system's date and time values should be recorded from the system's CMOS.
What is a deft?
DEFT (digital evidence and forensics toolkit) is a Linux-based distribution that allows professionals and non-experts to gather and preserve forensic data and digital evidence. The free and open source operating system has some of the best computer forensics open source applications. DEFT Zero is a lightweight version released in 2017.
What is NFAT for Mac?
This is a network forensic analysis tool (NFAT) for Windows, Mac OS X, Linux, and FreeBSD. These tools come in a free edition as well as a professional paid edition. Network Miner’s free edition can
How many downloads does the SIFT tool have?
Tools can be opened manually from the terminal window or with the help of top menu bar. Having more than 100,000 downloads to date, SIFT continues to be a widely used open-source forensic and incident response tool.
What is forensics tool?
Available in free and professional versions, this forensics tool helps you to collect evidence from a mobile phone. It collects all device information such as serial number, IMEI, OS, etc., and recovers messages, contacts and call logs. Its file browser feature enables you to have access to and analyze photos, documents, videos and device database.
What is a sleuth kit?
Sleuth Kit Autopsy. Autopsy is a digital forensics platform that efficiently analyzes smartphones and hard disks. It is used worldwide by a large number of users, including law enforcement agencies, the military, and corporations to carry out investigations on a computer system.
How much will cybercrime cost in 2019?
According to Juniper Research, cybercrime losses to businesses will surpass $2 trillion by the year 2019. With data breaches occurring all around the world every day, the demand for experts in computer forensics will also increase. Whether you need to investigate an unauthorized server access, look into an internal case of human resources, or are interested in learning a new skill, these free and open source computer forensics tools will help you conduct in-depth analysis, including hard drive forensics, memory analysis, forensic image exploration, and mobile forensics. However, this is not an extensive list by all means and may not cover all necessary tools required for a complete investigation. It only includes some of the popular and useful tools. Using the right tools can always help you move things faster and result in more productive results.
What is Wireshark used for?
WireShark is one of the most commonly used network protocol analyzers. It allows you to investigate your network activity at the microscopic level. Wireshark is widely used by government agencies, corporations and educational institutes.
